Buy Tenable Cloud Security Solutions
Start to finish CNAPP and driving CIEM abilities now accessible to safeguard multi-cloud conditions.
Threats have evolved. Get ahead of cyber risk.
Your assault surface is developing, continuously changing and more interconnected than any other time in recent memory. With specific security apparatuses offering a fragmented picture, it can feel difficult to respond to the inquiry, “How secure would we say we are?”
Reasonable’s way to deal with openness the board consolidates perceivability across all features of the assault surface with business setting so you can precisely comprehend your association’s digital gamble and focus on moderation.
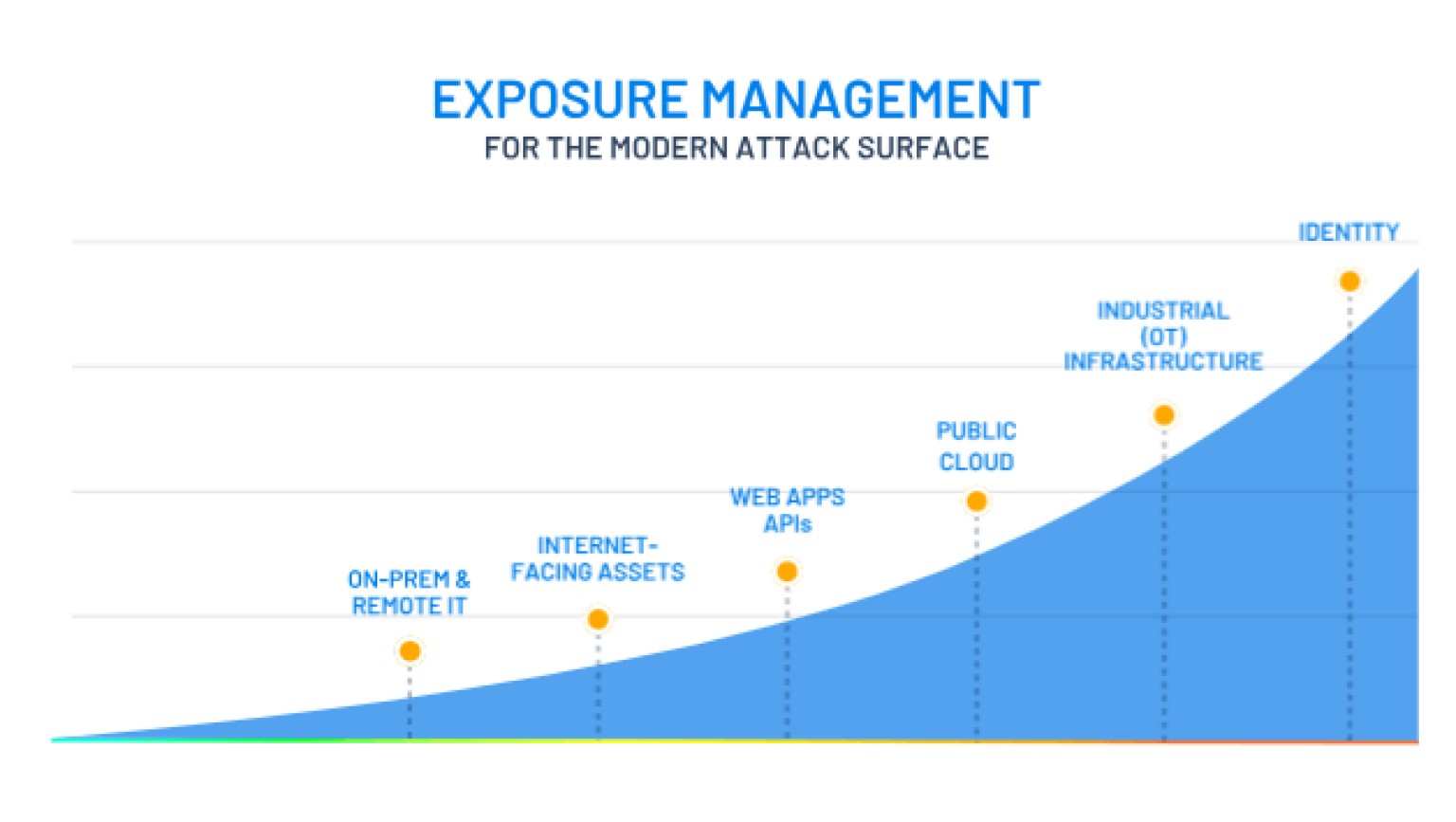
GET A SINGLE, UNIFIED VIEW OF YOUR MODERN ATTACK SURFACE
Buy Tenable One which is an exposure management platform that combines risk-based vulnerability management, web application security, cloud security and identity security.
Comprehensive Visibility
Valid One aides your network protection groups gain a brought together perspective on all resources and related programming weaknesses, design weaknesses and qualification weaknesses, whether on-prem or in the cloud, to comprehend where you are presented to risk.
Predict & Prioritize
The stage assists security pioneers with expecting the results of a digital assault by drawing upon the business' biggest informational collection and figuring out connections between resources, openings, honors and dangers across an assault way.
Effectively Communicate Cyber Risk
Security chiefs and business pioneers have a brought together and business-adjusted perspective on digital gamble. Clear KPIs show progress over the long haul with benchmarking against outer friends. The stage gives significant experiences into your by and large digital gamble, with the capacity to bore into departmental or functional units.
PROACTIVELY ADDRESS AND MANAGE YOUR CYBER RISK
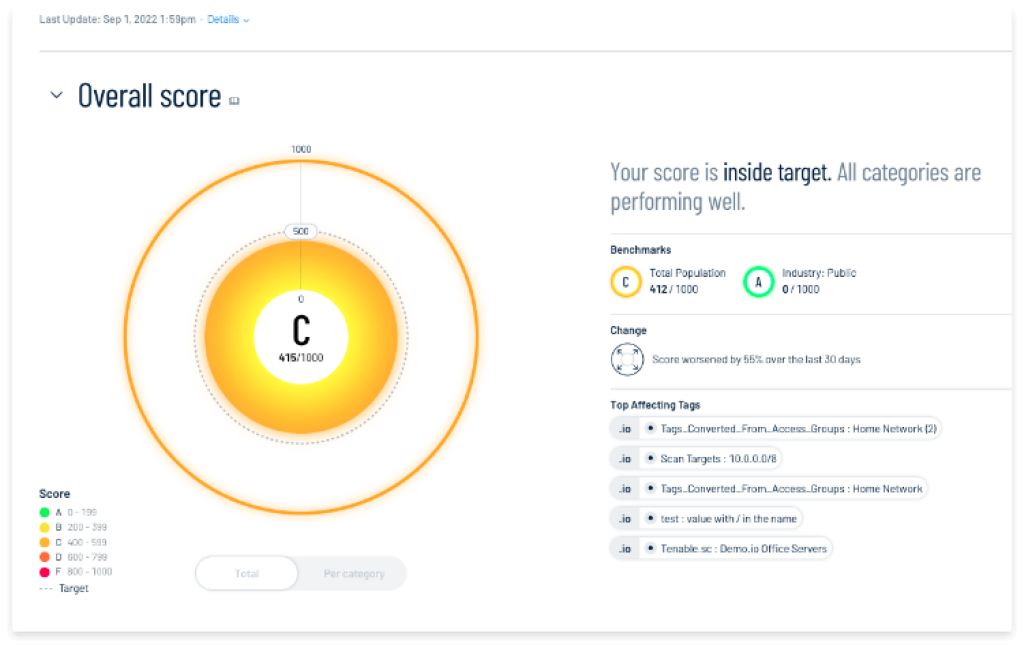
Quantify Your Exposure
Exposure View enables focused security efforts through clear, concise insight into your organization’s security exposure through a unified global exposure score drawn from a variety of different data sources.
It helps answer such critical questions as:
- How secure are we?
- Where do we stand in our preventative and mitigation efforts?
- How are we doing over time?
- What are the key events?
Eliminate Attack Paths
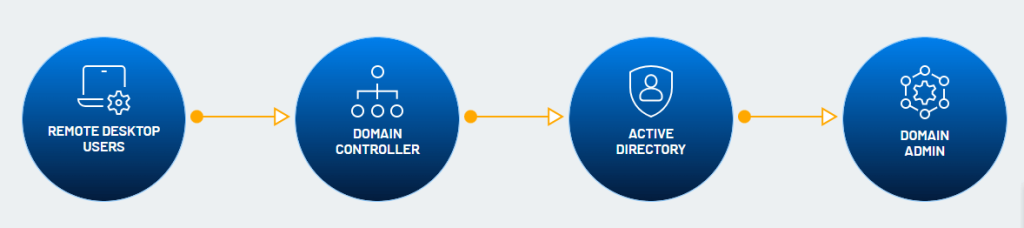
Attack path visualization and prioritization capabilities provide a pre-emptively focused response to remove the paths attackers may take. It performs this function by mapping critical risks to the MITRE ATT&CK framework to visualize all viable attack paths continuously — both on-prem and in the cloud.
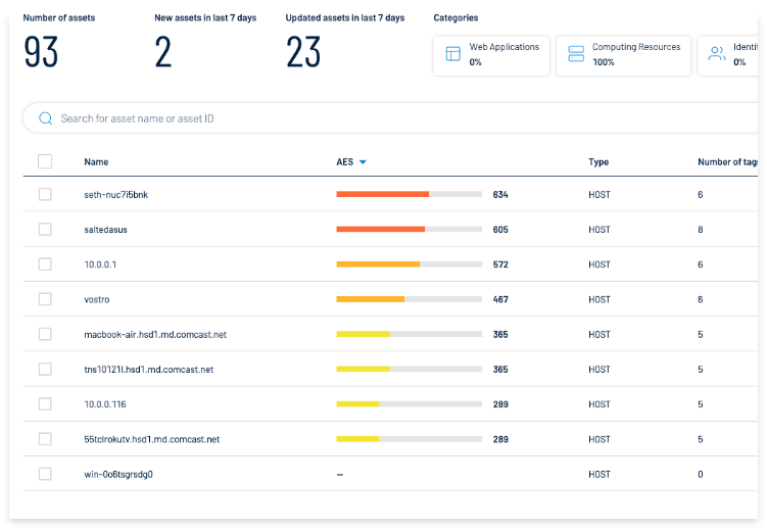
See Everything - Eliminate Blind Spots
Far reaching Resource Stock gives full perceivability into all resources and openings paying little mind to information source (weakness the board, web application security, cloud security and dynamic registry security, and so on.). This unified view smoothes out investigation, works on announcing and assists you with making a move quicker.
Buy Tenable Vulnerability Management Solutions
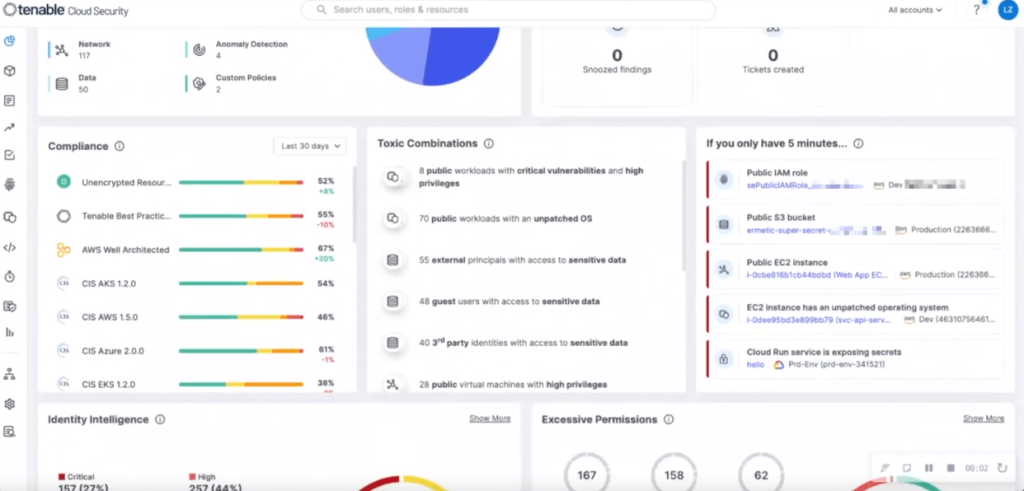
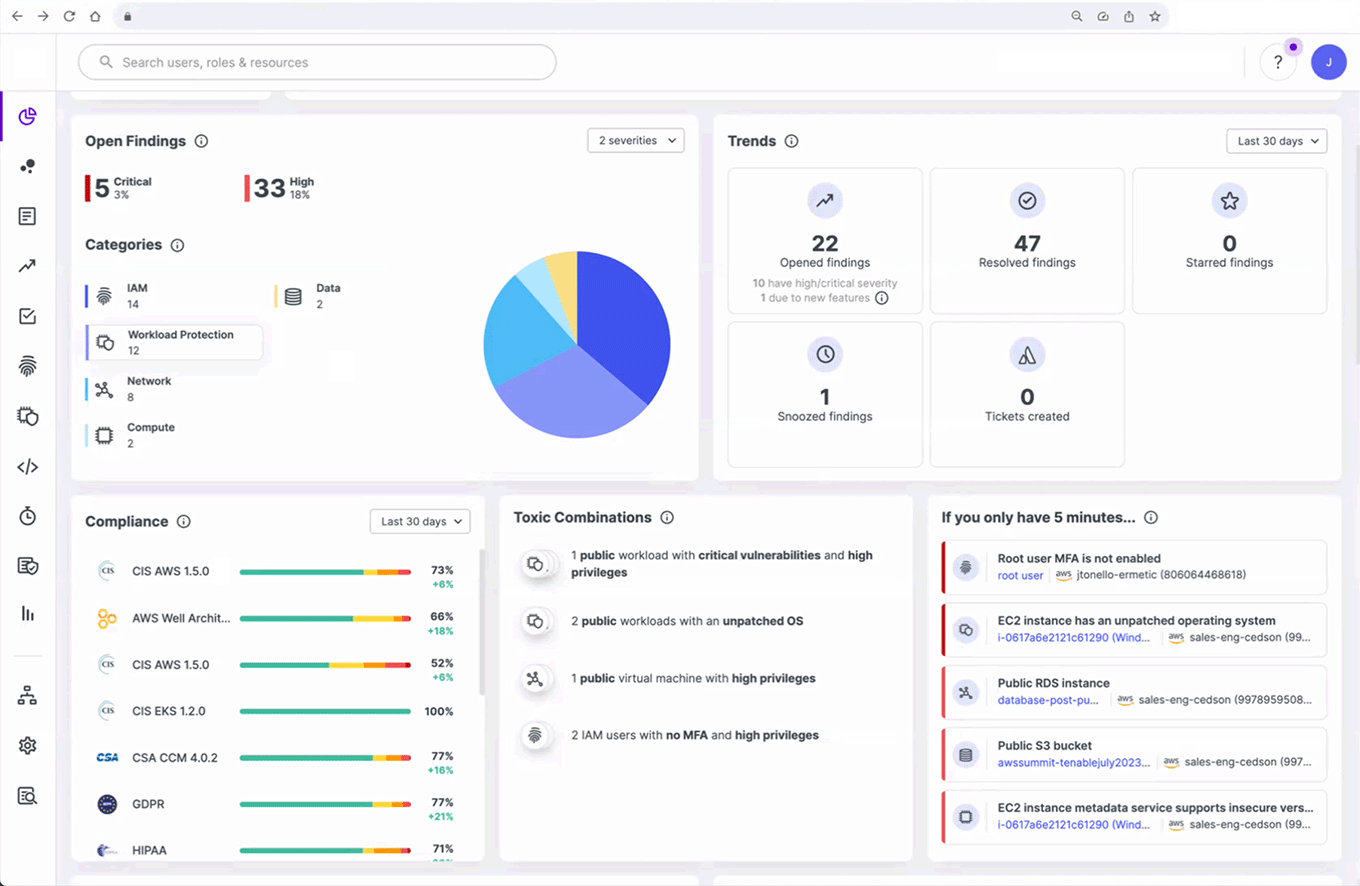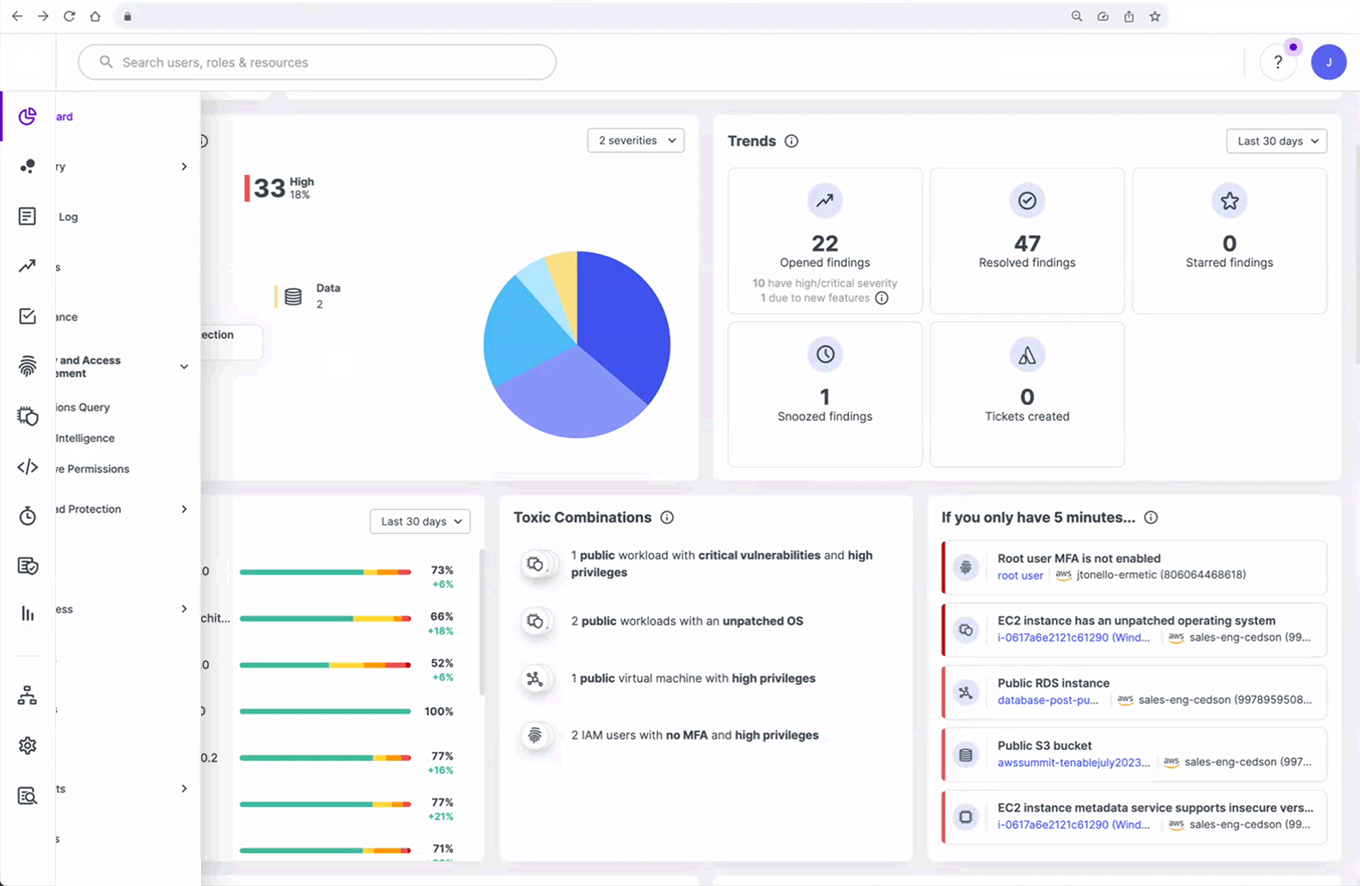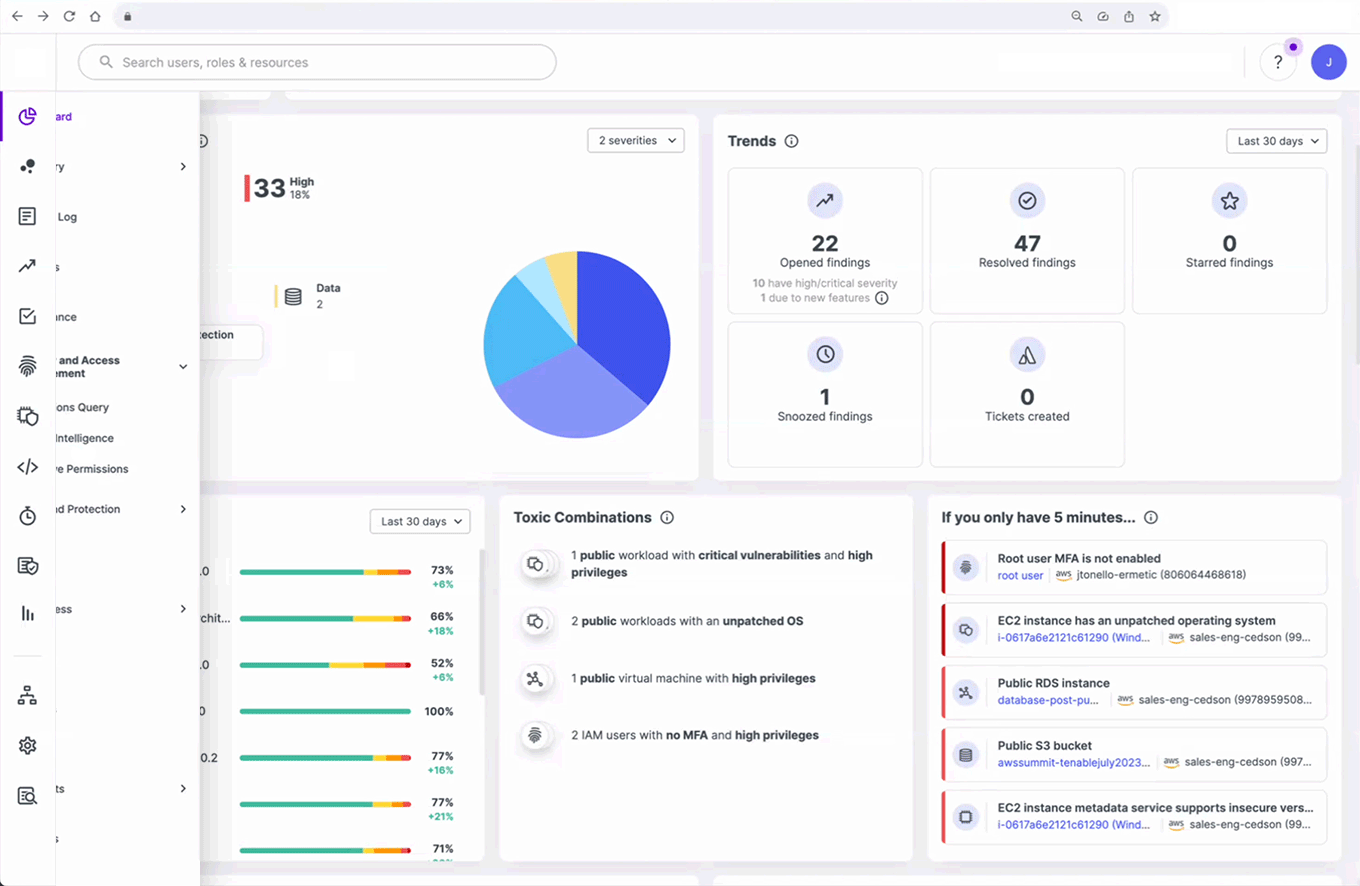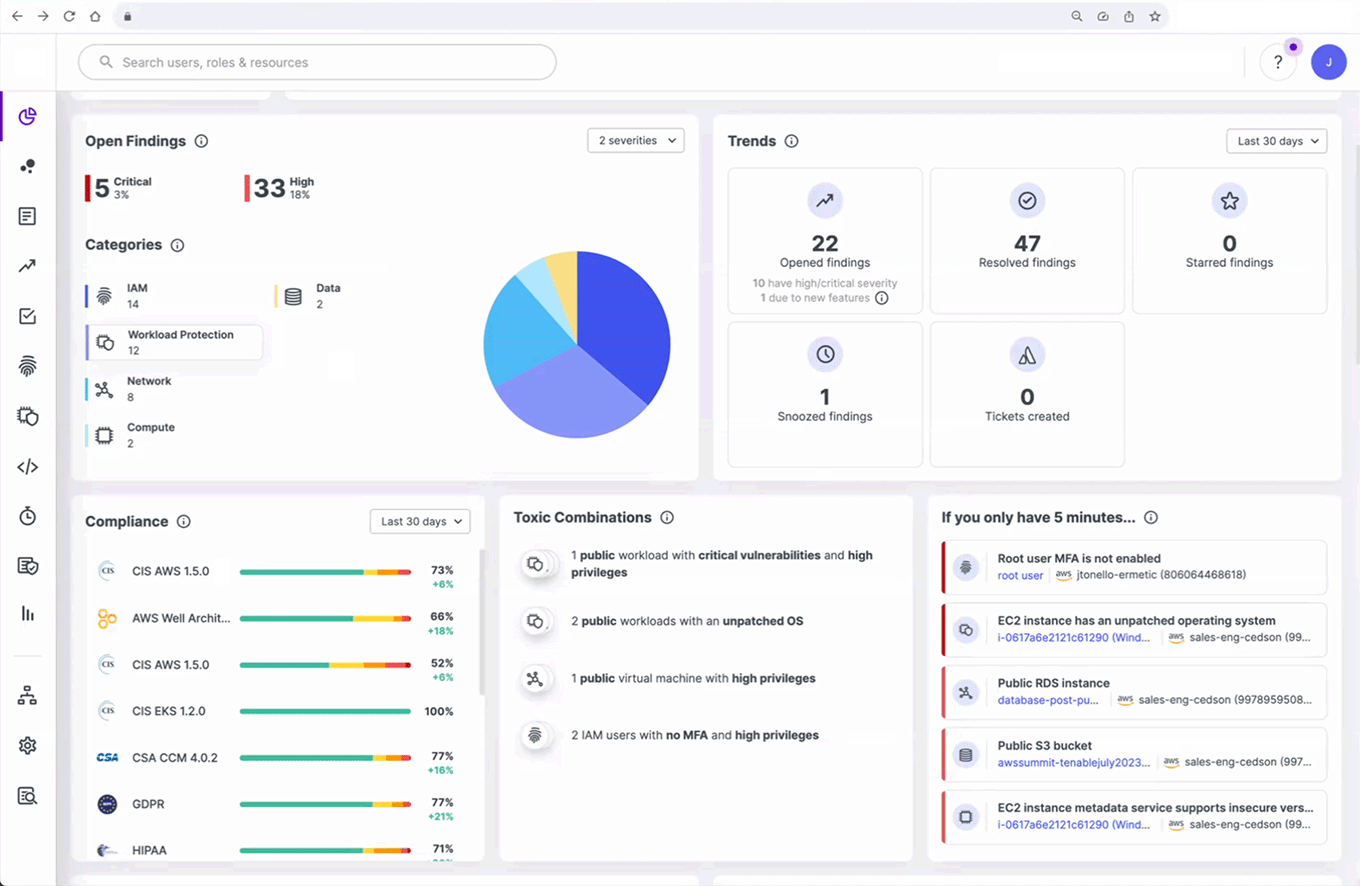
Unified Cloud Native Application Protection Platform (CNAPP)
Comprehensive CNAPP: Secure Your Cloud and Cloud Identities
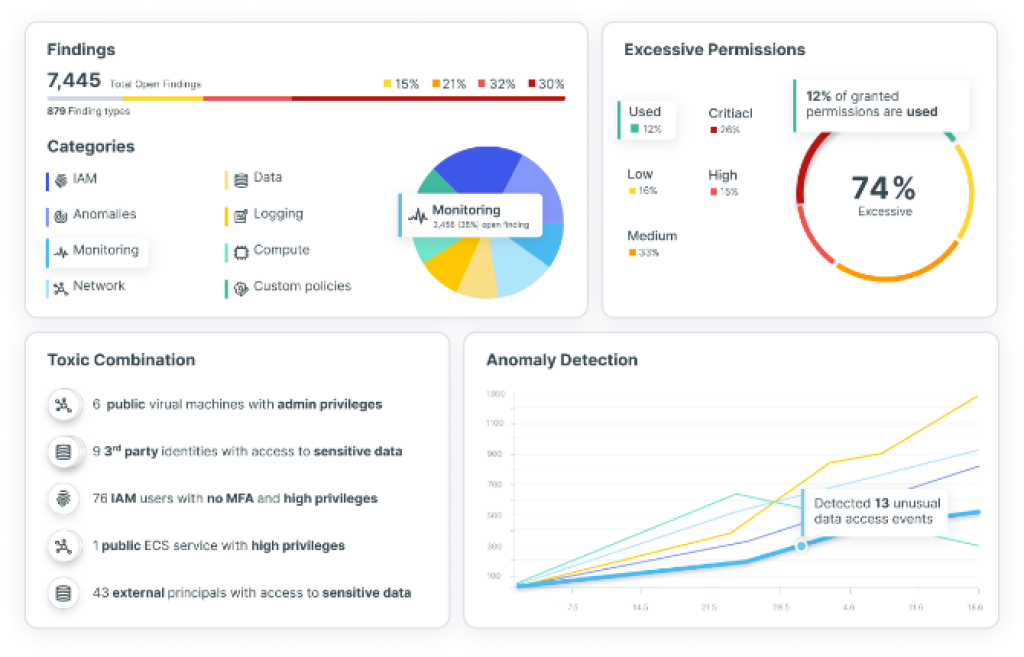
Cloud Security Posture Management (CSPM) and Compliance
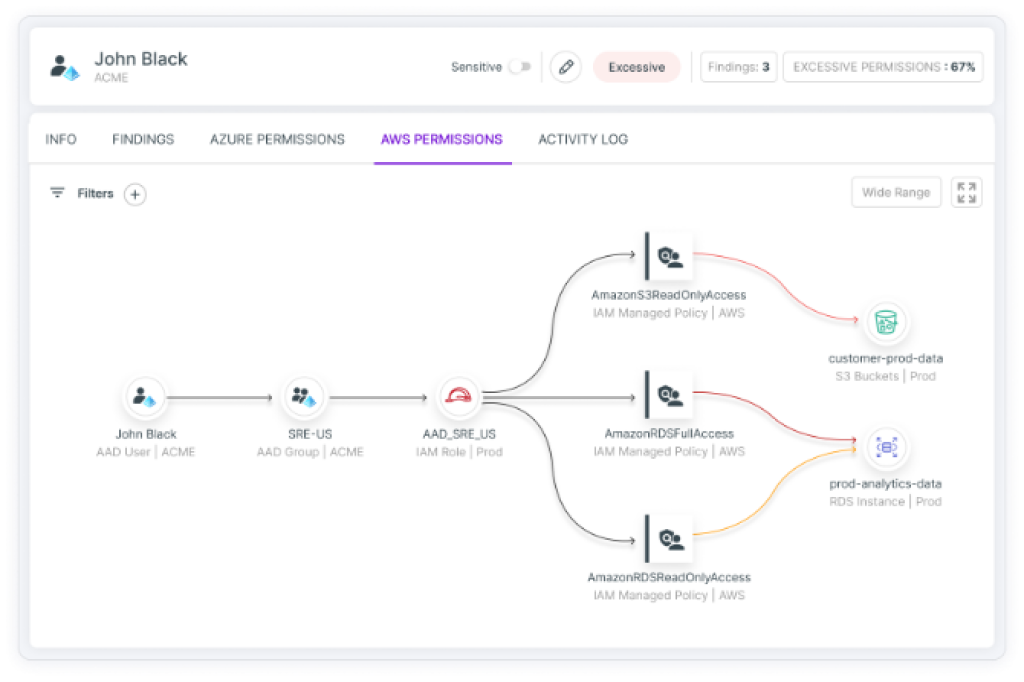
Cloud Infrastructure Entitlement Management (CIEM)
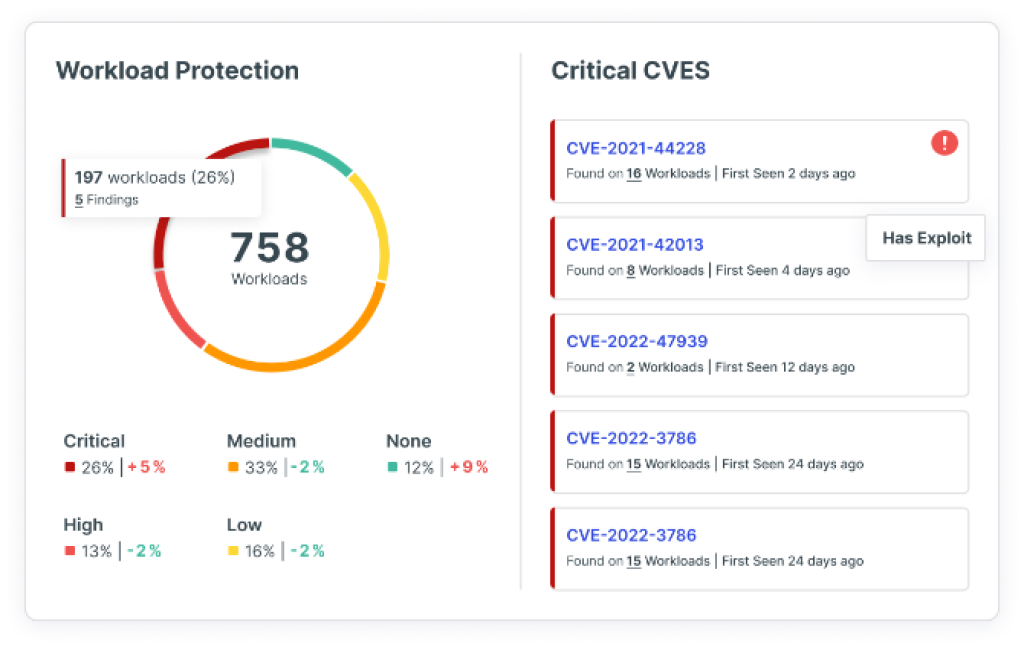
Cloud Workload Protection (CWPP)
Unified Cloud Native Application Protection Platform (CNAPP)

Tenable Web App Scanning
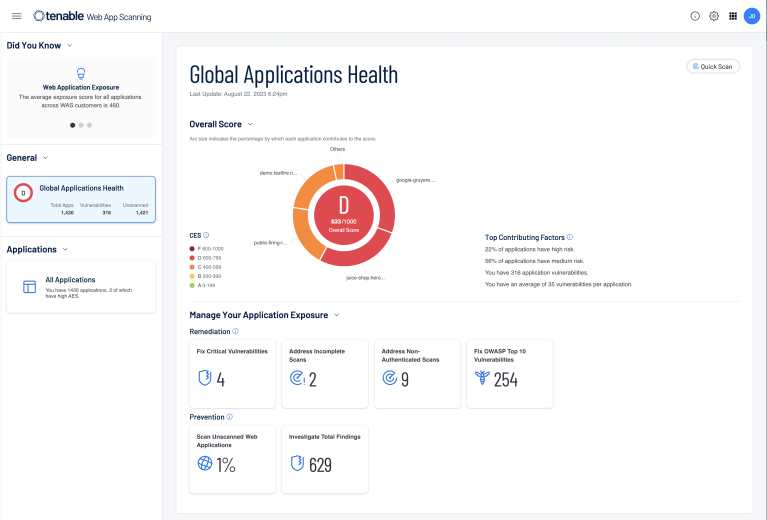
Simple, Scalable and Automated Vulnerability Scanning for Web Applications
Take advantage of web application security built by the largest vulnerability research team in the industry.
SIMPLE
Set up new web app scans in seconds by using the same workflows you are already familiar with. No need to spend hours or days manually tuning scans.
UNIFIED
View vulnerable web app components and custom code vulnerabilities alongside your IT and cloud assets. Eliminate complexity from managing multiple, siloed solutions.
ACCURATE
Comprehensive web app assessments built by experts give you confidence that your development teams aren’t wasting time on false positives or missing high-risk vulnerabilities.
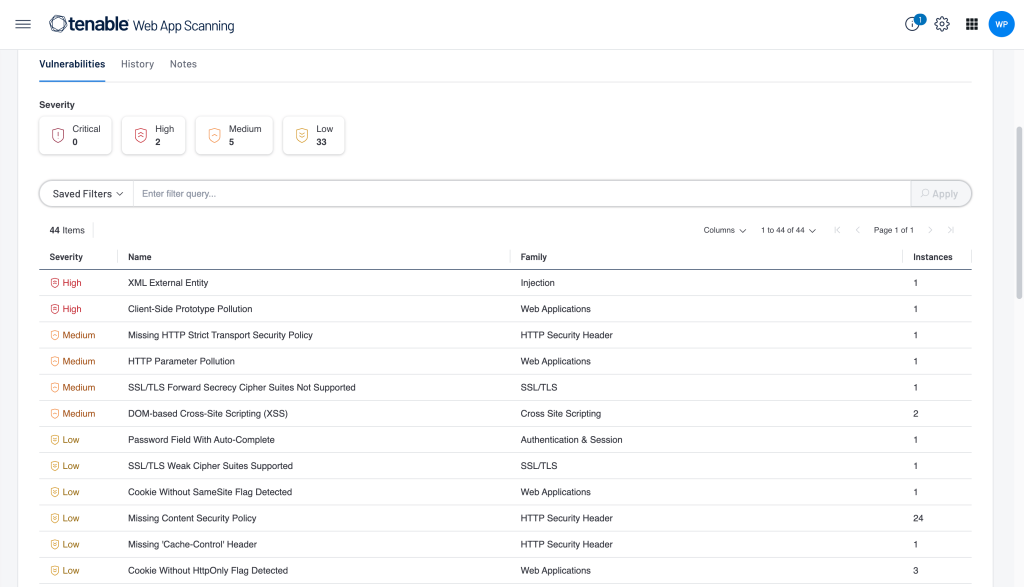
ACTIONABLE RESULTS IN MINUTES
- Results in Minutes
- Intuitive Scan Setup
- Fully Integrated Dashboards
- Easy Authentication Configuration
Buy Tenable Attack Surface Management Software
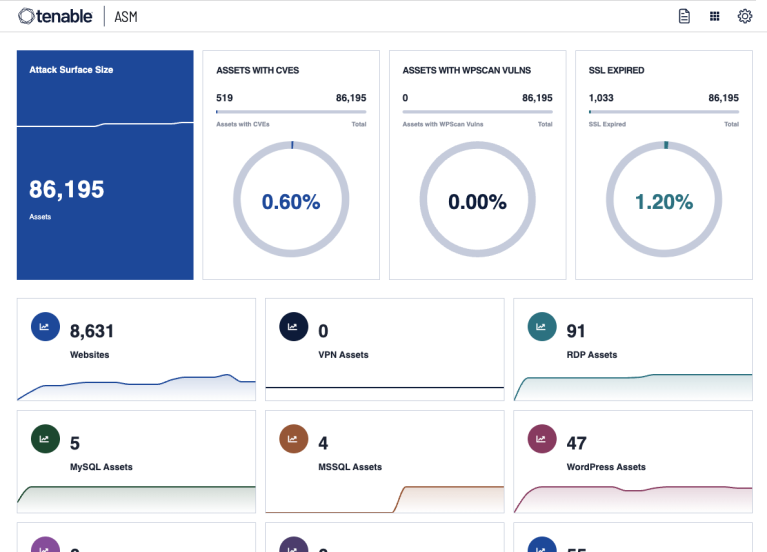
Gain Visibility Into Your External Attack Surface
Get comprehensive visibility into all of your internet-connected assets, services and applications to better understand your organization’s full digital footprint and better assess and manage risk
MITIGATE YOUR EXTERNAL RISKS
Discover What You Own
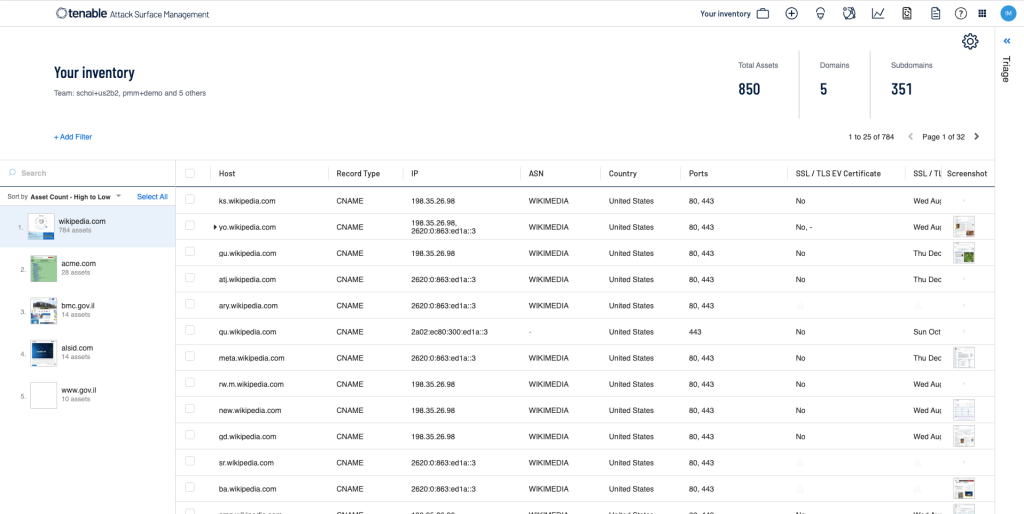
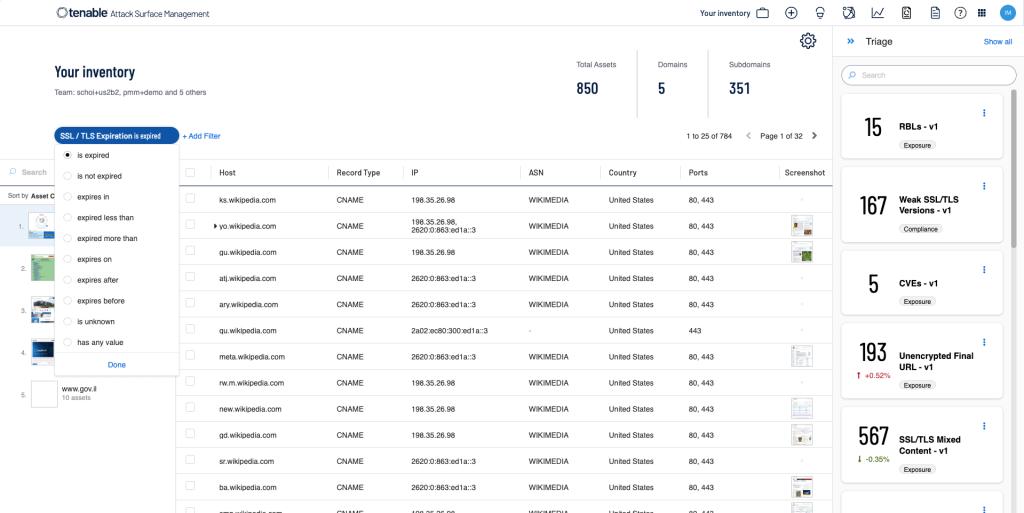
Understand Business Context
Easily Assess for Cyber Risk
EXTERNAL ATTACK SURFACE MANAGEMENT FOR:
Cybersecurity
Compliance
Brand Protection
Mergers & Acquisitions
Competitive Analysis
Legal
SOLUTIONS FOR
Automotive Manufacturing
Energy
Finance
Healthcare
Retail
Transportation
Try Free Demo
Frequently Asked Questions
What is Tenable, and what products does it offer?
Tenable is a cybersecurity software that offers products and solutions for vulnerability management, compliance management, and threat intelligence.It helps organizations identify, prioritize, and remediate vulnerabilities to reduce cyber risk.
How does Tenable.sc help organizations manage vulnerabilities effectively?
Buy Tenable.sc that provides continuous visibility into the security posture of IT assets, allowing organizations to detect vulnerabilities, misconfigurations, and compliance violations in real-time. It offers advanced analytics, reporting, and workflow automation to streamline vulnerability management processes.
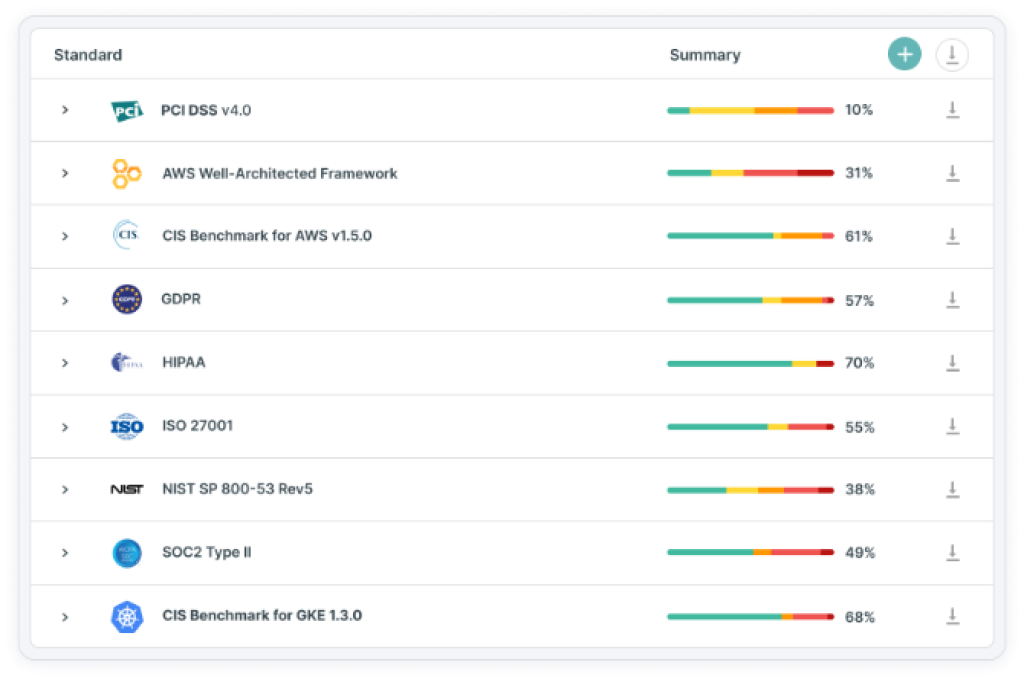
Can Tenable help organizations comply with industry regulations and standards?
Yes, buy Tenable software which offers solutions to help organizations comply with industry regulations and standards such as PCI DSS, CIS benchmarks, and ISO 27001. It provides built-in audit policies, customizable templates, and compliance dashboards to simplify compliance management efforts.
Is Tenable suitable for organizations operating in highly regulated industries?
Yes, buy Tenable that is suitable for organizations operating in highly regulated industries such as finance, healthcare, and government. Its comprehensive vulnerability management and compliance solutions help organizations address regulatory requirements and mitigate cyber risk effectively.









