Buy Teleport -The easiest and most secure way to access and protect all your infrastructure
Why Common Access Architectures Are No Longer Enough
Cloud & Identity are Top Cyber Targets
Most of assaults are presently centered around personality, with burglary of accreditations or insider facts or taking advantage of human mistake.
Passwords, Secrets & VPNs Don't Scale
Designers and security groups' inclinations are adjusted, with both looking for simpler, safer ways of administering access.
Compliance Needs Are Increasing
FedRAMP, HIPAA, SOC 2, SEC revelation, and that's just the beginning. Clients need to scale how they meet administrative prerequisites.
Modern Access for Today's Needs
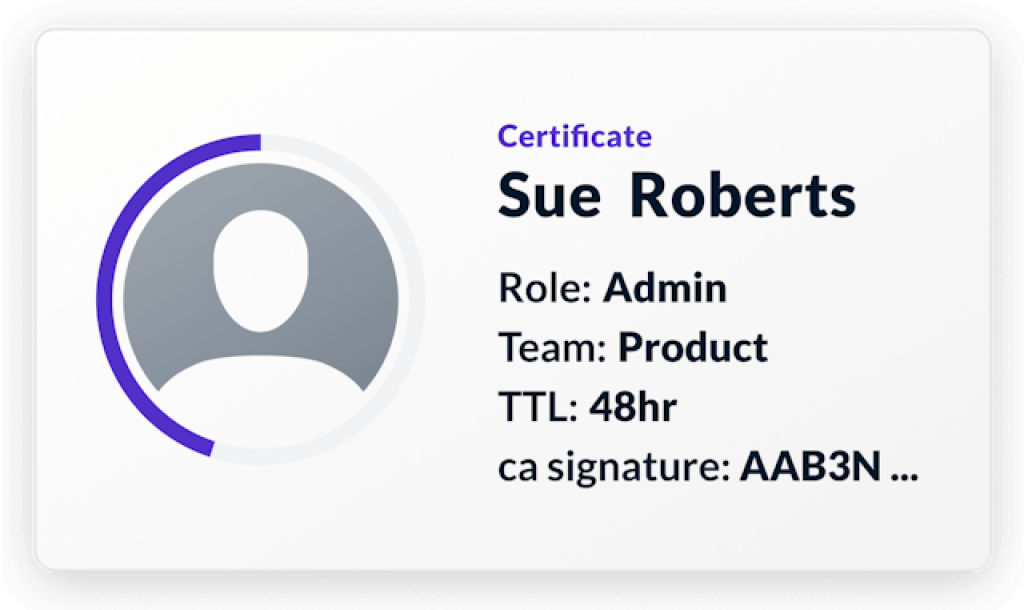
Cryptographic Identity
Zero Trust Access
Secretless Authentication & Ephemeral Privileges
Identity & Policy Governance
PLATFORM
Teleport Access
Teleport Identity
Teleport Policy
Teleport Access
Phishing-Resistant Identity
- User Identity
- Machine Identity
- Resource Identity
- Device identity
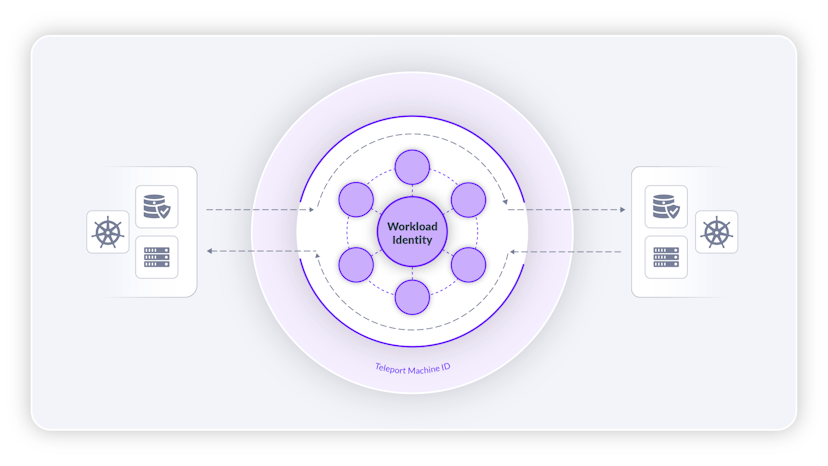
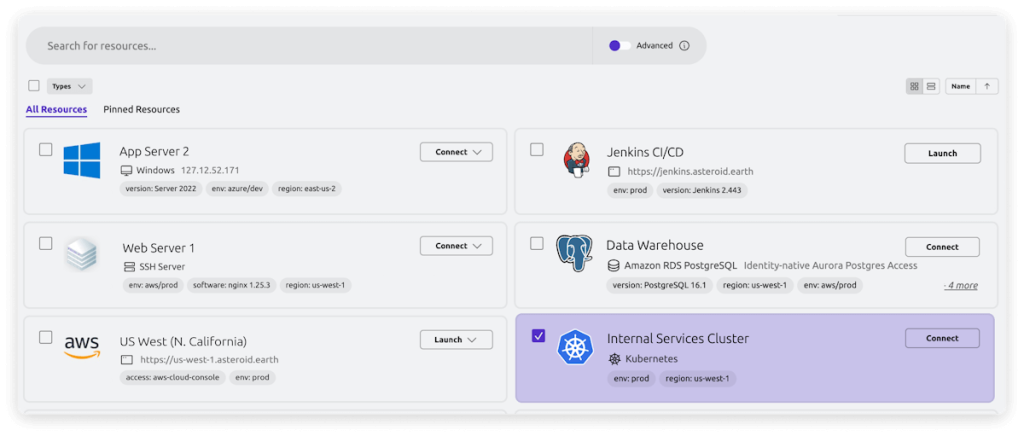
Unified Access
Break access silos with a unified inventory of all infrastructure resources in your organization. Eliminate the need for different access paths, passwords, shared secrets, vaults, and VPNs.
Trusted Infrastructure
Self-refreshing stock of confided in figuring assets (servers, mists, data sets, Kubernetes bunches, Web applications) and selected TPM-prepared client gadgets (PCs, workstations, YubiKeys, from there, the sky is the limit)
Secure Remote Access
Zero-trust admittance to applications and responsibilities from anyplace, with auditable access across mists, on-premises conditions and IoT armadas, without VPNs, stronghold has or vaults with shared mysteries.
Ephemeral Privileges
Short-lived Privileges
Access Requests
Consolidated Visibility & Audit
Identity-Based Audit Events
Gather organized, definite review occasions for every meeting with character, application and convention information.
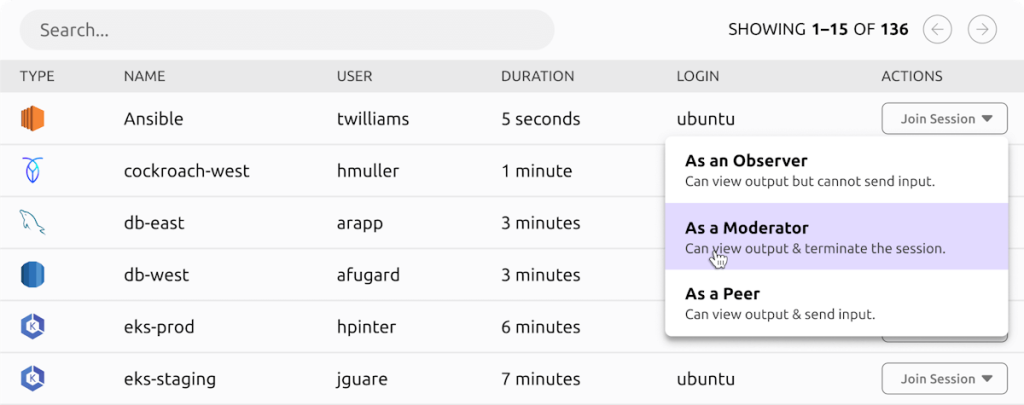
Interactive Session Controls
Record, replay, join, and moderate intuitive meetings for SSH and Kubernetes.
Live Sessions View
View each dynamic confirmed association across your whole foundation. Meddle if necessary.
Compliance & Policy
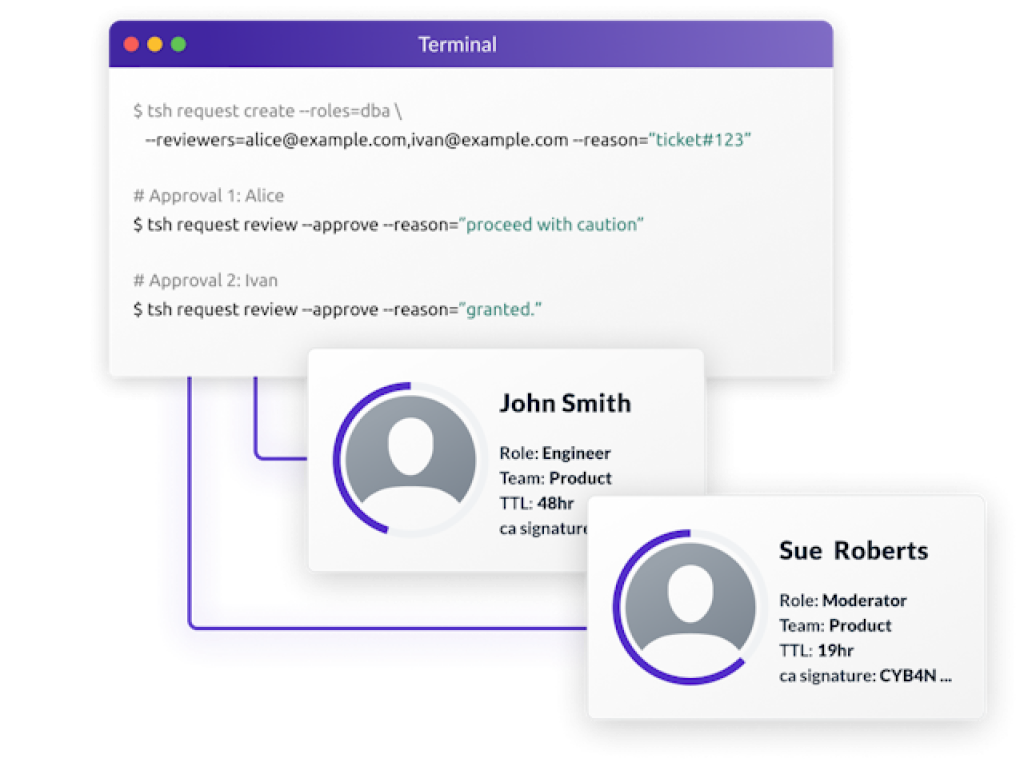
Dual Authorization
Session Sharing and Moderation
Supports Regulatory Standards
AI Assist
Troubleshoot Common Issues
Optimize Infrastructure
Collect Infrastructure Details
Run Generated Commands
Teleport Identity
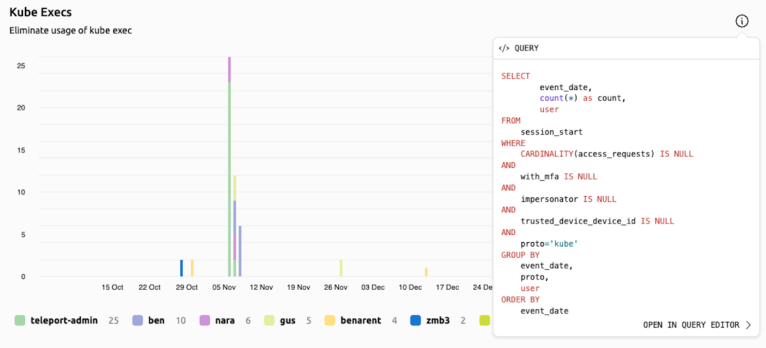
Eliminate Weak Access Patterns
Access Monitoring & Response
Identify excessively expansive honors and examine meetings that are not areas of strength for utilizing, for example, multifaceted verification or gadget trust.
Alerting and Response
Buy Teleport which provides Alert on access infringement and cleanse unused authorizations with robotized access rules.
Reduce Attack Surface with Just-in-Time Access
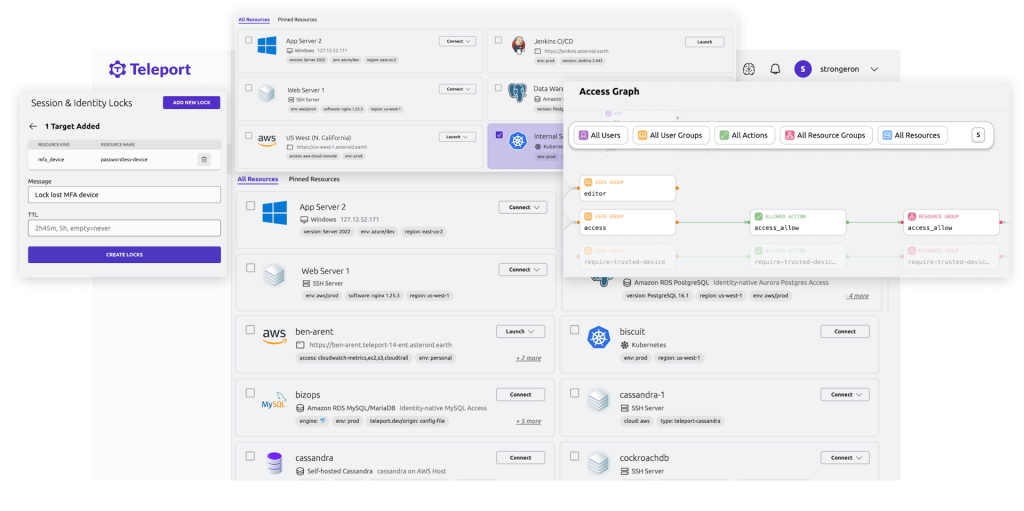
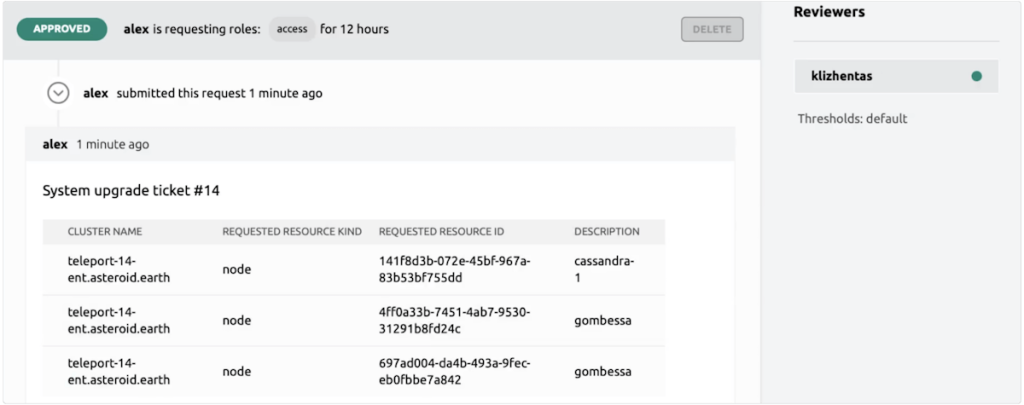
Access Requests
Award just those honors important to finish the job in question. Eliminate the requirement for super-special records. Designers can utilize their favored devices - kubectl, ssh, ansible, postgresql and some more.
Access Reviews
Survey access demands utilizing Slack, PagerDuty, Microsoft Groups, Jira and ServiceNow. Allot supervisors, computerize compulsory surveys, and carry out custom audit rationale utilizing our Programming interface and Go SDK.
Respond to Identity Threats
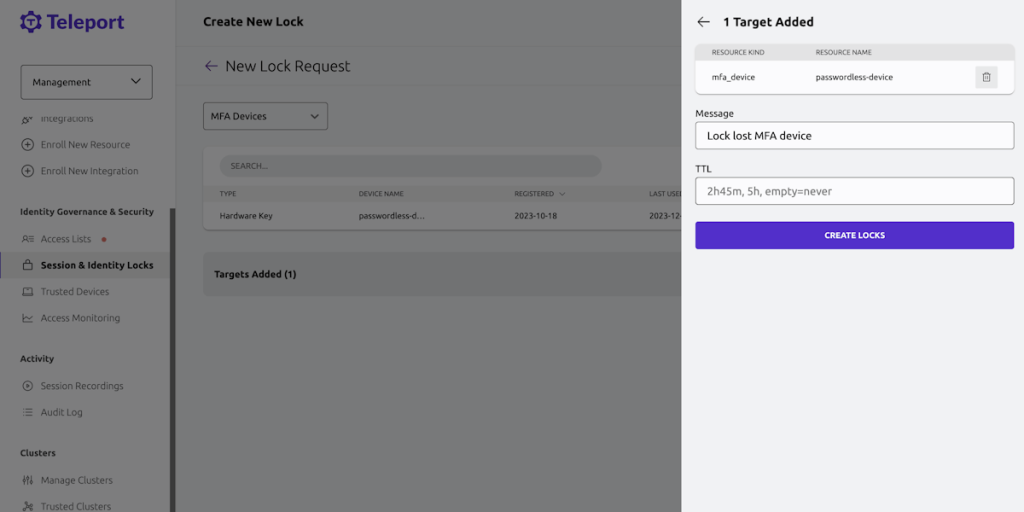
Identity Locking
Lock dubious or compromised personalities and shut down the entirety of their action across all conventions and administrations.
Access Management
Buy Teleport software that has arrangement or deprovision access for all clients and machines across the entirety of your foundation.
Harden Identity Assurance
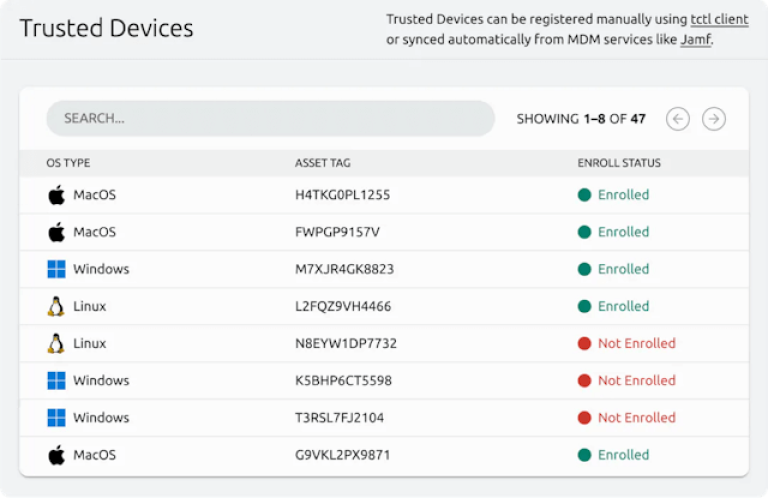
Device Trust
Require Paired User and Device Identity
Teleport Policy
Comprehensive Visibility
Instant Discovery
Eliminate Shadow and Risky Access
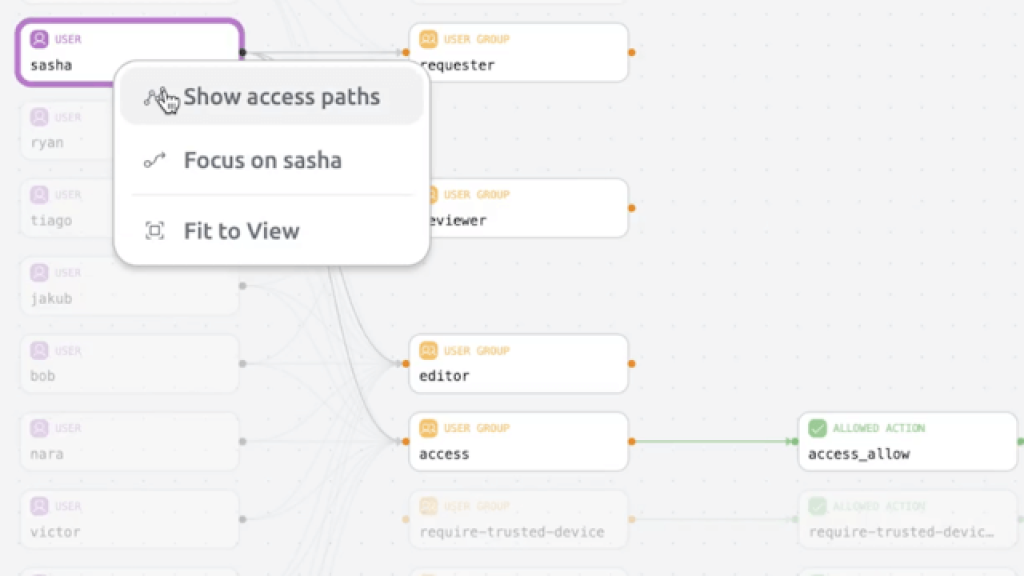
Query Access Graph
Buy Teleport software and Jump into definite access ways for clients, conventions, and assets through strong questions.
Optimize Access
Decisively examine and refine access ways to proactively dispense with expected dangers and tweak access conduct.
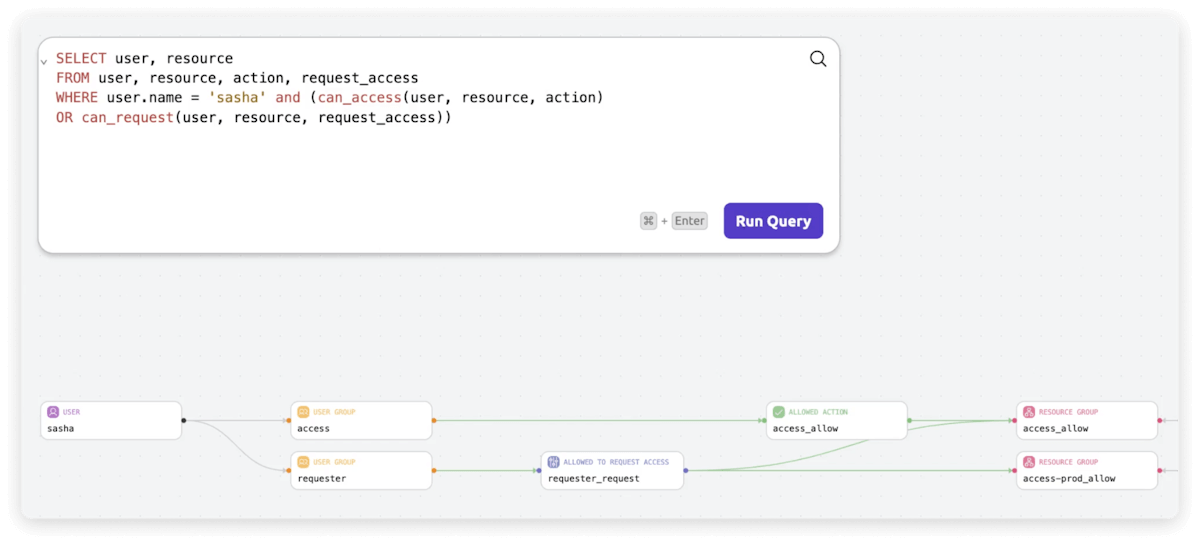
Unify Policy Management
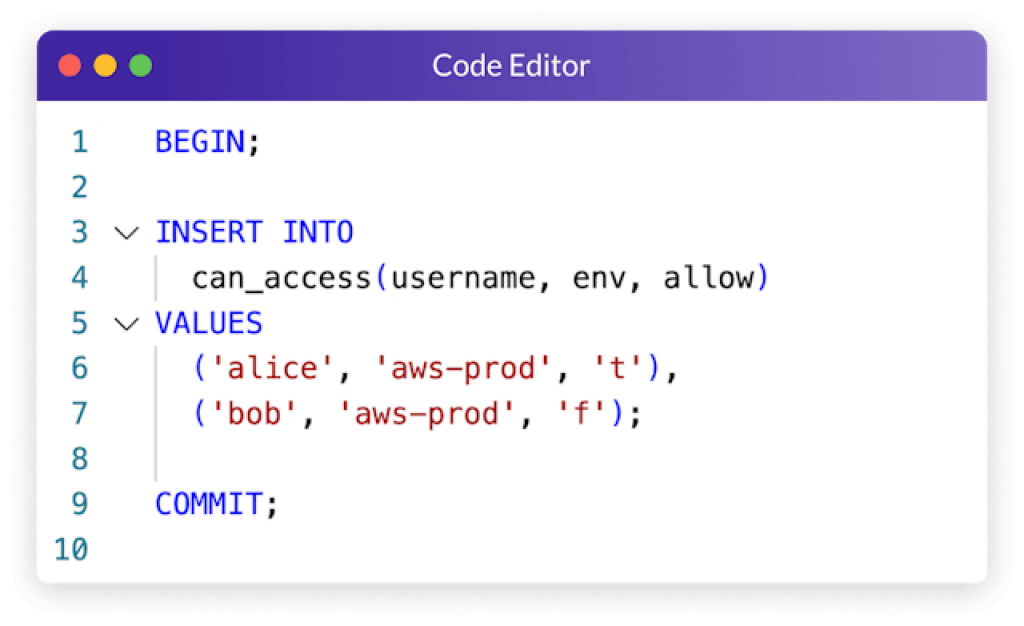
Query Policy
Manage Policy
SOLUTION FOR
E-Commerce & Entertainment
Financial Services
SaaS Providers
Try Free Demo
Frequently Asked Questions
What is Teleport software?
Teleport is a modern infrastructure access management solution designed to provide secure access to infrastructure resources such as servers, databases, and Kubernetes clusters.
How does Teleport software work?
Teleport uses a combination of SSH, Kubernetes, and database proxies to authenticate and authorize access requests. It employs strong encryption and certificate-based authentication to ensure secure connections.
Is Teleport suitable for my organization?
Buy Teleport software which is ideal for organizations that require secure, auditable access to their infrastructure resources, especially in multi-cloud or hybrid cloud environments. It is well-suited for companies in industries such as finance, healthcare, and technology that have stringent security and compliance requirements.
How do I get started with Teleport?
You may buy from official website or you can buy Teleport from software resellers like us and follow the installation instructions provided in the documentation. Additionally, you can explore Teleport’s features through interactive tutorials and demos available on the website.