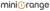Buy miniOrange Identity & Access Management Software

Get security solutions that lead the industry for your employees, customers, and partners to increase productivity, user ease, and customer sign-ups.
Securing user identities and their access with miniOrange Resellers
Workforce Identity
Protect and empower your employees, contractors and partners with simple and secure access to business resources.
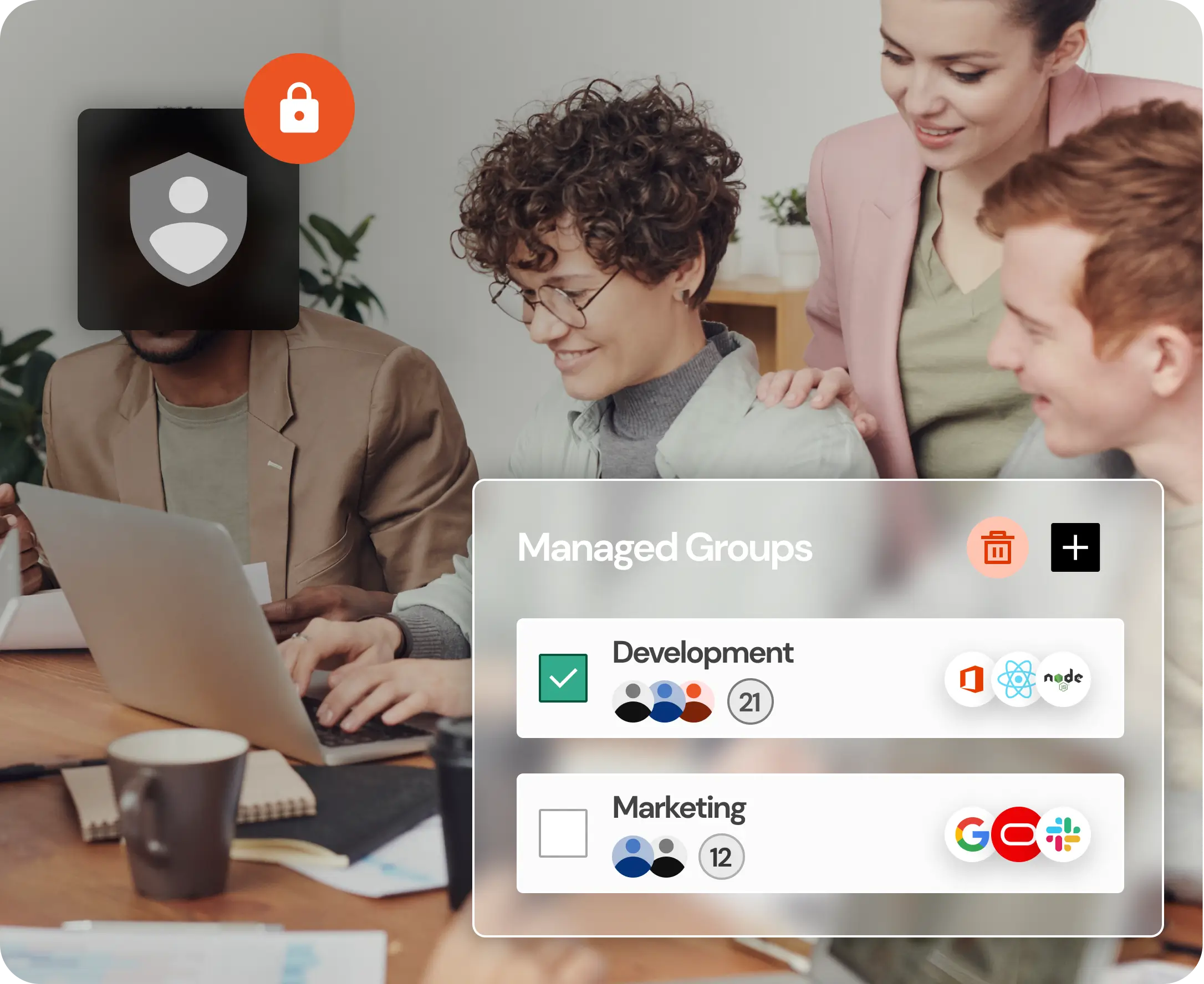
Customer Identity
Helps organizations to manage customer identities and data, as well as control customer access to applications and services.
PRODUCTS
Single Sign-On (SSO)

A solution that allows users to get one-click secure access to multiple On-Premise, SAAS, and Cloud-based applications using a single username and password.
- A single dashboard to access enterprise applications
- Customize access policies per application
- Get deep insights into application usage and user access
Features of Single Sign-On (SSO)
Extensive SSO solution
Enable SSO for any application that supports SAML, JWT, OAuth, or OpenID Connect protocols, including your in-house and legacy applications.
Leverage existing identity Sources
Allow users to SSO login using their existing Active Directory, ADFS, LDAP, HR Systems, Microsoft 365, G Suite, or Zoho credentials.
Tailor Made SSO Solution
Customized Registration and Login Page with Multi-Language Support which allows users to easily edit their self-service portal according to their requirements.
Improvised Audit
Gain deep insights into application usage and the user accesses activities from one central console for IT Admin.
Simplified user management
Easily adds or removes multiple users, and grants or revokes their access to applications in a single click via the Single Sign-On admin portal.
Multiple Deployment Options
Deploy the SSO solution on the platform of your Choice - Cloud, On-Premise, or Hybrid according to your requirements.
Benefits of SSO
Boost Productivity
SSO solution helps employees and end-users quickly access their enterprise apps with a single click. This eliminates the inconvenience of managing, remembering, and resetting multiple passwords, thus improving productivity with higher conversion rates.
Pay As You Go
The pay As You Go model (especially for cloud-based SSO services) helps you to spend less with a special user tier structure with 24/7 support. We have special discounts for educational and non-profit organizations.
Security Compliance
Security and Compliance factors enforce organizations to prove that they have taken adequate security measures to protect sensitive data. Single Sign-On (SSO) helps with regulatory compliance to meet data access and security risk protection requirements.
Reduced IT Costs
Enabling SSO allows users to manage individual dashboards and self-reset passwords, which eliminates the necessity for IT support, saves admin time on password resets, and supports tickets to focus on more important tasks. This helps in reducing IT costs.
Stronger Security
SSO authentication ensures that only authorized users get access to sensitive data. With Single Sign-On you can implement password policies like Password length, complexity, restrictions on password reuse, session timeout and self-service password reset policy to strengthen security without holding up your users access.
Scale as you grow
Buy miniOrange cloud-based arrangement and serious evaluating permit you to Pick your membership plan in view of current necessities, and afterward scale as you develop from miniOrange software resellers .
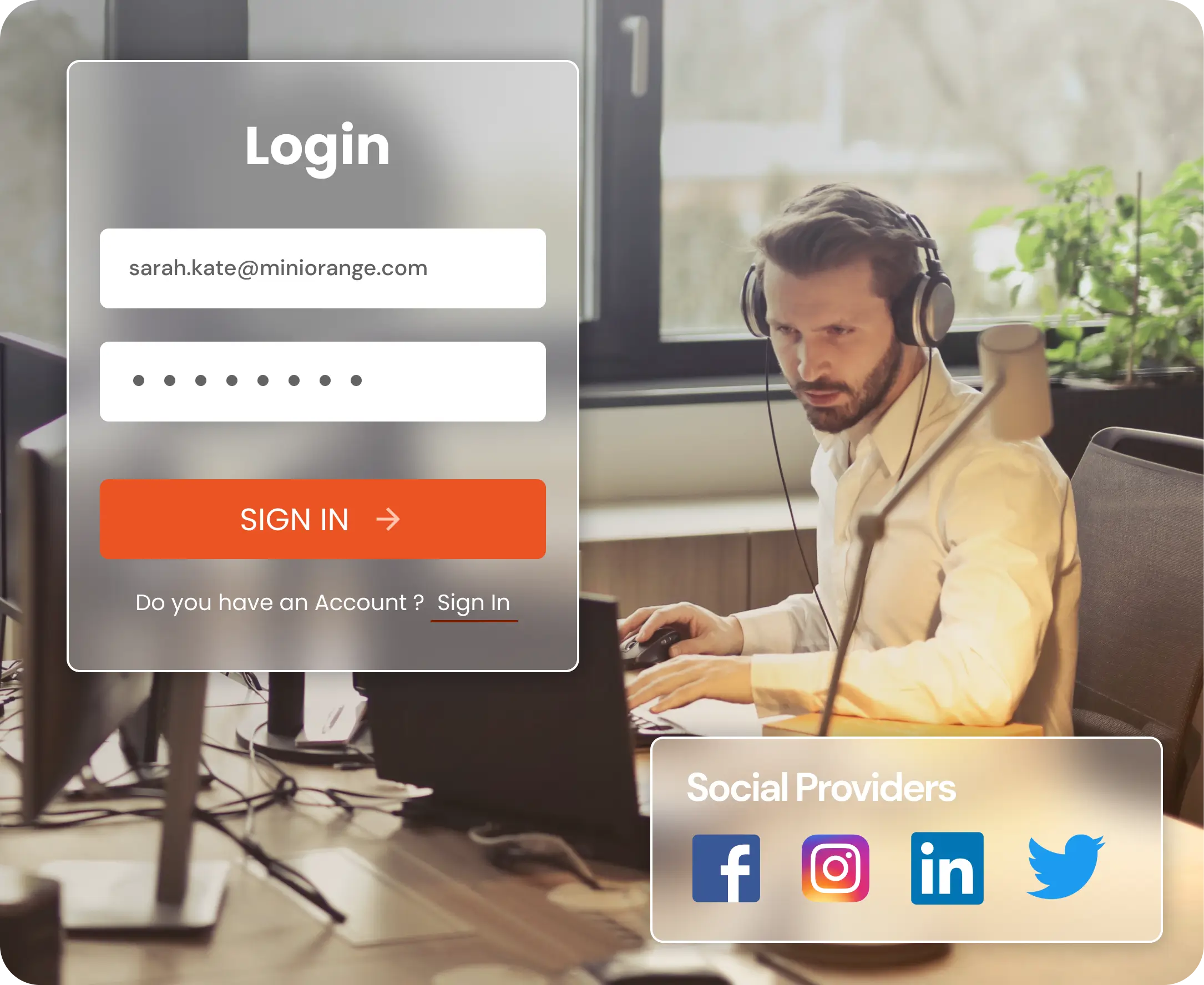
Multi-Factor Authentication (MFA)
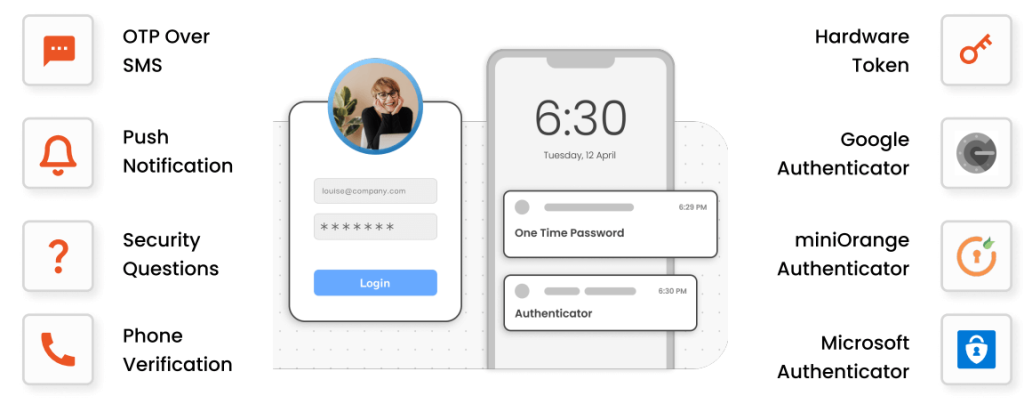
Multi-factor authentication (MFA) is an advanced level of authentication with two or more levels of security factors. Ensuring the correct identity has access to your sensitive information.
- For web apps, VPNs, VDIs, Network Devices, and Windows/Linux
- 15+ authentication methods
Benefits of Multi-Factor Authentication (MFA)
Enhanced security
Multi-Factor Authentication (MFA) adds an extra layer of security, reducing the chances of an attacker gaining access to the system.
Increased productivity and flexibility
Employees may securely access business apps and resources from practically any device and location, without jeopardising the company's network.
Fraud Prevention
Multi-Factor Authentication (MFA) adds an additional degree of protection by ensuring that everyone is who they say they are, preventing unwanted access.
Improved user trust
When employing Multi Factor Authentication (MFA), users may secure the protection of their personal information without exerting additional effort.
Reduced management cost
You'll observe less suspicious behaviour on client accounts if you use Multi-Factor Authentication (MFA), and you'll spend less money on security management as a result.
Adaptability for different use cases
Additional security is required when processing high-value transactions or accessing sensitive information from unknown networks and devices, such as geolocation, IP address, and time since the last login.
The Future of Workplace Security - Adaptive / Risk-based Authentication
Adaptive Authentication provides an extra edge to MFA security based on risk and access provided by the security admin to control user access.
Adaptive Authentication (also known as Risk-based Authentication) detects fraudulent attempts based on predetermined risk criteria and prompts customers to complete an additional authentication step to confirm their identities.
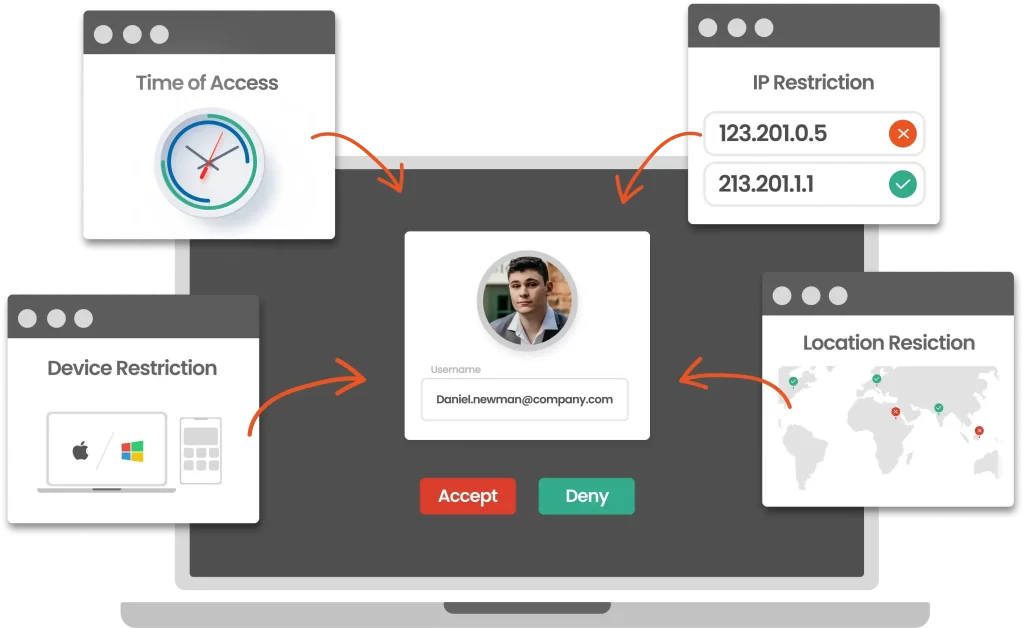
Adaptive / Risk-based authentication takes advantage of real-time analytics to get a complete picture of the circumstances surrounding each login.
When a user tries to sign in, a adaptive authentication system looks at things like:
- Device – Is the employee using their personal laptop instead of using a company-issued laptop?
- Location – Is the employee trying to access a system using a public network rather than the company’s network? Or is the employee in another time zone?
- IP Address – Is the employee connecting from a known IP? Or Is it info from another country?
- Sensitivity – Is the requested file critical to the company’s operations? Is it a little bit of knowledge, or is it significant?
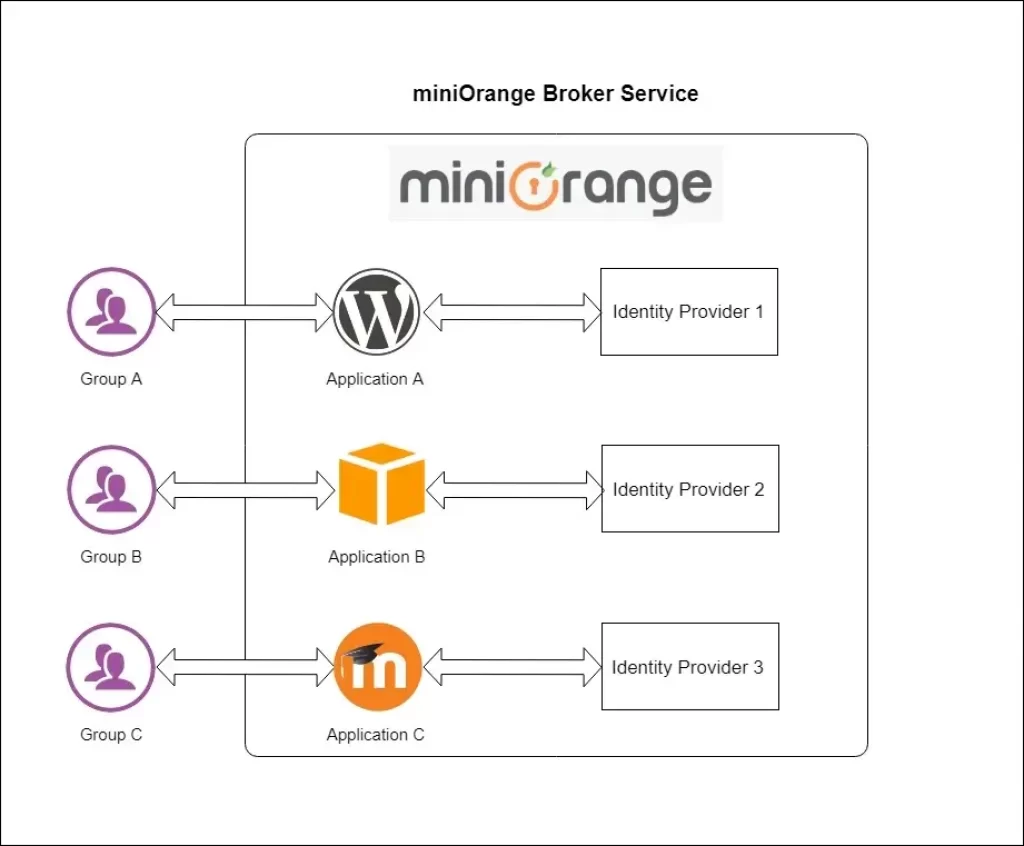
Identity Brokering
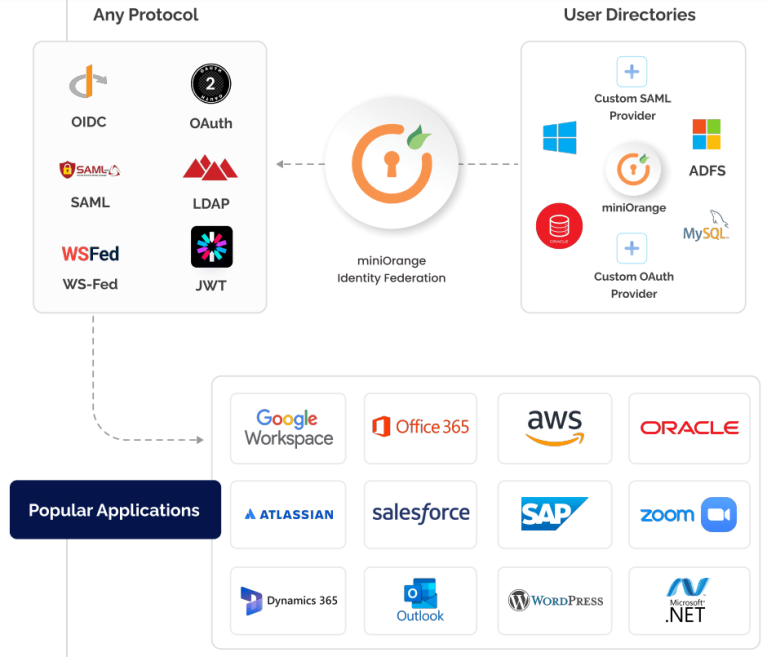
Identity Brokering Service
What is Identity Brokering Service?
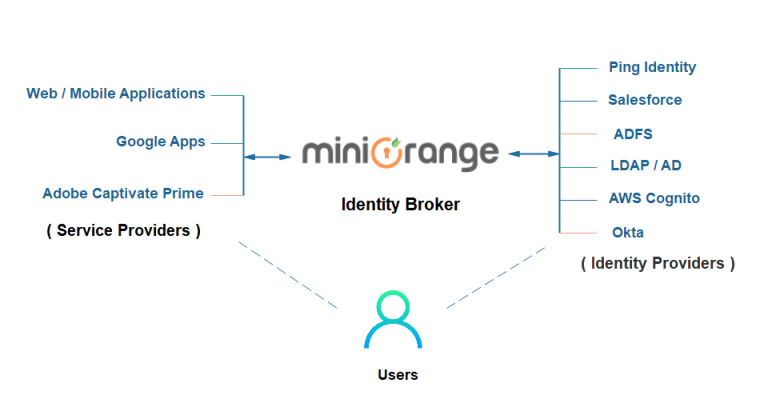
Character Facilitating is a method for laying out trust between parties that need to utilize online personalities of each other. Personality Intermediary is a help that interfaces various Help Providers(SPs) with various Character Providers(IdPs). Don’t bother understanding or executing complex Single Sign-On (SSO) conventions like SAML, OAuth, OpenID, CAS, and so forth.
Streamline Workforce and Customer security with designated features

Multiple SAML Providers
With IdP Facilitating, administrators can design different SAML Character Suppliers and arrange which clients/applications validate against which Personality Source.
App based Identity Source
Administrators can design which Personality Source should the clients be validated from in the event that the confirmation demand starts from a specific application.
Domain-based redirection to IDP
Administrators can arrange the areas of the clients who might confirm against any SAML, OAuth, and so on Personality Supplier through Character Representative Help.
Domain-based redirection to IDP
Clients can be diverted to a specific Personality Source consequently without inciting the client to pick his/her Character Source on each login endeavor.
Assertion Attribute Mapping
Clients can get ascribes from their IdP and guide them to SP client credits like firstname, lastname with help for custom ascribes through miniOrange Intermediary.
IDP / SP initiated SSO
With IdP Facilitating, clients can begin SSO from Specialist organization (SP) and are then diverted to the Personality Supplier (IDP) for verification as well as the other way around.
How to Setup Multiple IDPs for Identity Brokering?
Login using IDP selection page

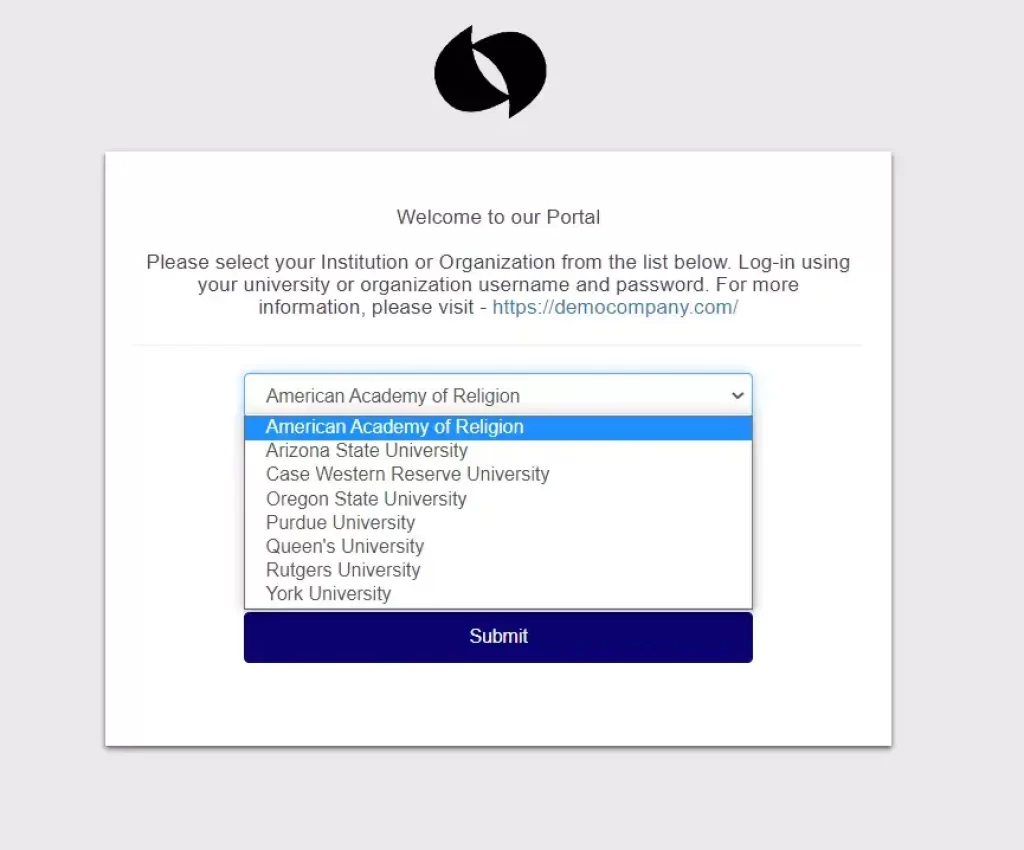
Login via Domain Mapping
miniOrange Character Merchant Administration gives Login through Space Planning highlight when you have different IDPs and you maintain that a specific arrangement of clients should confirm from one IdP while one more arrangement of clients to verify from one more IdP in view of their email spaces. All things considered, you can accomplish this with our Area Planning highlight. We have given a Space Planning field under every IdP where administrators can enter the area
Login via App Identity Provider Mapping
User Lifecycle Management through miniOrange Resellers
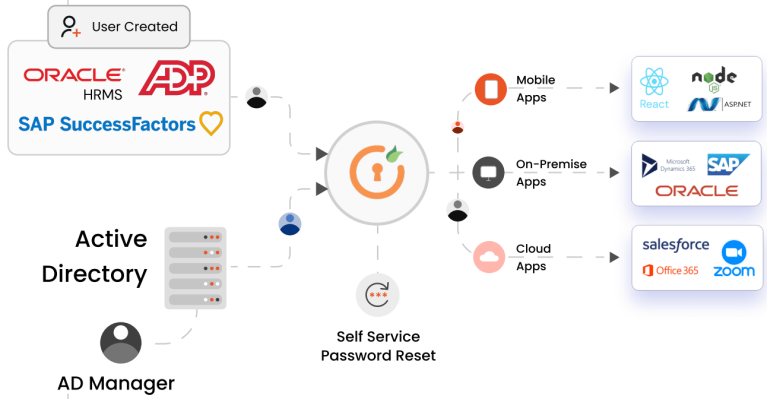
Buy miniOrange that automates the process of creating, deleting, and managing user accounts across multiple applications and services, simplifying user management and sync across platforms and reducing the
risk of errors or security vulnerabilities to your organization.
- Built in standardized support for SCIM, API, Webhooks and JIT for all your user lifecycle management needs across AD/LDAP, HR system, and any IdP
- Keep user data sync across all your platforms with timely bidirectional automated sync feature
- Quickly add, modify, or delete users with bulk upload and customizable attribute mapping options
Two-Factor Authentication

Two-Variable Confirmation (2FA) builds security of your records and conditions, by guaranteeing that the right arrangement of eyes approaches your touchy data sitting on the cloud or on-premise and shield your record from unapproved access.
2FA Authentication Factors
Knowledge Factor
Information factors incorporate numerous passwords, PIN codes, and replies to security questions. Anything you can recollect, type, say, do, execute, or in any case review when required is considered as an information based validation factor.
Possession Factor
This variable proposes that you have a specific article since it is unrealistic that a programmer would gain your secret key and take anything physical. This classification incorporates smartcards,mobile telephones, equipment tokens, programming tokens, and keychains.
Inherence Factor
This element is much of the time checked by a finger impression test on a gadget, however it likewise incorporates whatever might be an entirely remarkable distinguishing proof of your actual individual, like a retinal test, voice or facial acknowledgment, or some other kind of biometrics.

Features of 2FA
Zero Trust Authentication
Zero Trust approach inside 2FA assists with establishing a compelling climate, arrangements, and foundation to limit information breaks.
Passwordless Authentication
2FA login for clients utilizing just Username and OTP/TOTP hence, forestalling the need to enter Secret key.
Offline Authentication
Permit clients to sign in regardless of whether there is no web accessible by utilizing Disconnected 2FA technique
Role Based 2FA
Administrator can empower or cripple 2FA for a particular client job and for a specific application.
VPN / Windows Solution
Gives Two-Element Validation (2FA) answers for OpenVPN, Palo Alto, Cisco Heartbeat, Windows, RDP and so on.
User Self Enrollment
It offers inline enlistment of clients so you'll essentially initiate and arrangement 2FA and you're prepared.
Try Free Demo
Frequently Asked Questions
What is miniOrange software used for?
miniOrange is a leading provider of identity and access management solutions, offering a range of products and services to secure digital identities and enable secure access to applications and resources. Its solutions include single sign-on (SSO), multi-factor authentication (MFA), adaptive authentication, and more.
How does miniOrange help organizations enhance security?
Buy miniOrange that provides robust identity and access management solutions to help organizations strengthen security posture, mitigate identity-related risks, and ensure compliance with regulatory requirements.
Is miniOrange suitable for businesses of all sizes?
Yes, buy miniOrange software which offers solutions that cater to businesses of all sizes, from small and medium-sized enterprises (SMEs) to large enterprises.
Can miniOrange integrate with other IT systems and applications?
Yes, miniOrange software solutions offer seamless integration capabilities with a wide range of IT systems, applications, and cloud services commonly used in modern IT environments. This allows organizations to extend security controls and enforce policies across their entire IT infrastructure.