Safeguard the Digital Journey
Next-generation protection for web apps, services, and APIs, on the clouds you already trust.
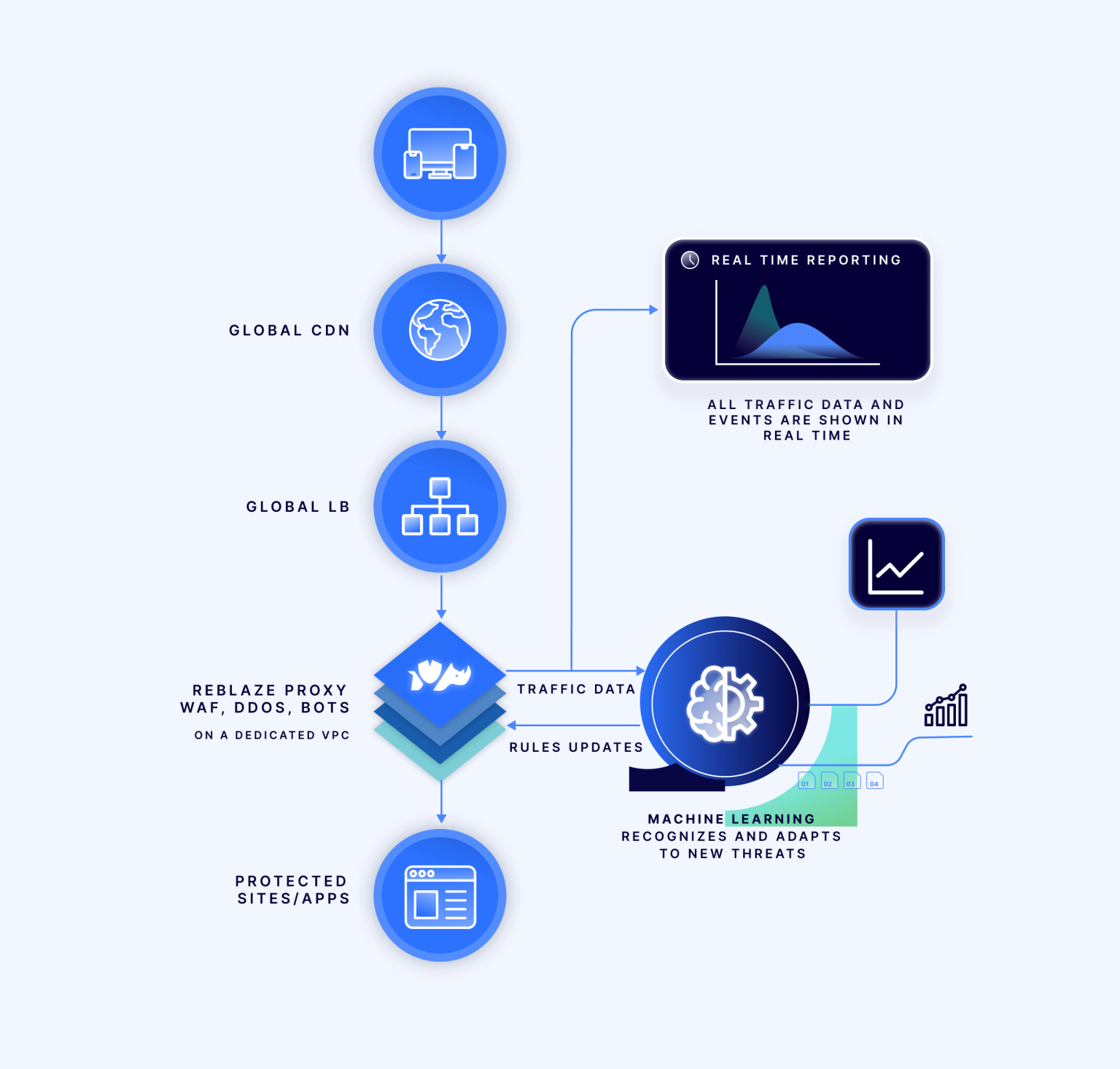
All-in-one, fully managed web security solution
Fully Managed Web Security
The platform is fully managed and maintained remotely by Reblaze personnel. Your security is always up-to-date and always effective. Whenever there are sudden increases in traffic, Reblaze automatically scales resources to accommodate the surge. Through the Dashboard, you can access a real-time summary of all incoming traffic, providing insights into what is permitted, what is blocked, and the reasons behind these decisions. For every request, you have access to comprehensive details, including headers and payloads. Even during extensive DDoS attacks, you can stay informed about the ongoing activities on your site.
Many Additional Benefits
Full DevOps Support
Unlike most WAFs that hinder DevOps processes, Reblaze fully supports it. When you deploy or modify an application or service, Reblaze recognizes, adapts, and starts protecting it immediately.
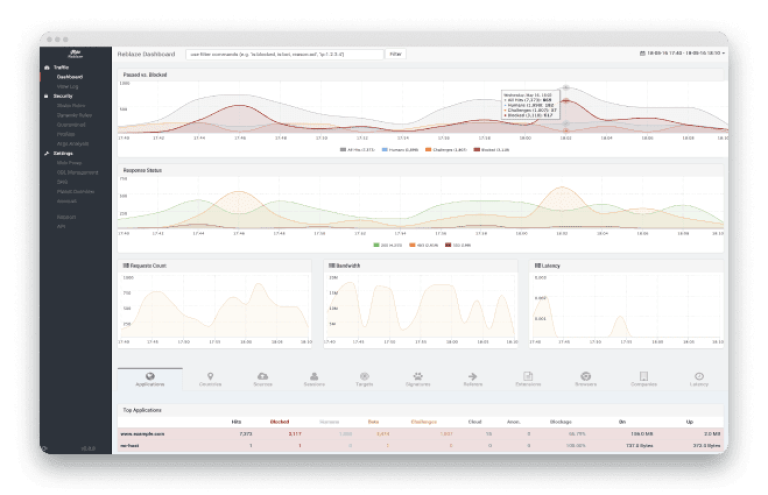
Full Real-Time Traffic Visibility
With the Reblaze dashboard, you gain an intuitive glimpse into your traffic, enabling you to effortlessly delve into individual requests for detailed analysis.
API for Programmatic Operation
Reblaze offers full programmability, enabling seamless operation through automation.
DNS and SSL Management
Reblaze personnel remotely maintain the platform, ensuring your security is consistently up-to-date and highly effective.
Solutions
Web Application Firewall (WAF)
The Reblaze Web Application Firewall

A Protective Shield for Your Web Assets
The Reblaze WAF protects against all the vulnerabilities in the OWASP Top 10, and many more:
Malicious Payloads
Code and SQL Injection
Cross-site Scripting
Form Manipulation
Cookie and Session Poisoning
Protocol Exploits
DNS Exploits
More Benefits
How the Reblaze WAF Works
Threat Blacklisting
Reblaze's security team maintains an expansive and expanding database of web vulnerabilities. Whenever a new threat emerges online, your Reblaze platform promptly receives an immediate update incorporating the precise solution to neutralize it.
Application Whitelisting
Defeating zero-day exploits is achieved by strictly adhering to a finely detailed rule-set of application specifications, which denies all traffic that fails to meet these criteria. Consequently, this robust approach virtually eliminates any possibility for hackers or intruders to inject any form of malicious code
Behavior Analysis
Employing sophisticated behavioral analysis, Reblaze effectively identifies and blocks various activities aimed at probing the network, such as network reconnaissance, penetration tests, and attempts at reverse-engineering pages or application protocols. This comprehensive approach thwarts both automated hacking and manual intrusion techniques with high accuracy and reliability.
Precise Administrative Tools
Reblaze's distinctive Access Control technology empowers clients with complete traffic control. It offers the flexibility to allow or block network traffic based on specific criteria such as countries, cities, networks, companies, anonymizer networks, cloud and data-center networks, and more
DDoS Protection
Distributed Denial of Service (DDoS) Protection

Multilayer DDoS Protection
Reblaze gives full-scope DoS and DDoS protection, thwarting attacks across layers 3, 4, and 7: organization, transport, and application.
Multivariate threat detection
Resources scale
Defeats hacking attempts, bots, and more
Handle bandwidth activity
Fully managed and always up-to-date
24/7 incident support
How Reblaze Protects Your Web Assets from DoS/DDoS
Dynamic DNS Allocation
By implementing this method, attackers are effectively prevented from sending DDoS traffic to your server. Instead, all traffic, including DDoS attacks and other types, is compelled to undergo analysis within the Reblaze system before reaching your server.
Elastic load balancing
The distribution of attacks across Reblaze's global clusters effectively alleviates the strain on both the targeted site and its ISP. As a result, the ISP is not compelled to throttle the traffic, even when facing a large-scale assault.
DDoS traffic is filtered
Advanced human and behavior detection mechanisms are utilized to filter DDoS traffic. This sophisticated approach allows legitimate visitors to access your site while effectively blocking any incoming DDoS traffic
Your domain can absorb
Even the most substantial DDoS attacks can be absorbed because Reblaze's distributed network is multi-homed across various providers for enhanced diversity and robustness. Leveraging the cloud, Reblaze offers an abundance of bandwidth, surpassing what most ISPs can provide, ensuring superior protection against cyber threats.
As attacks scale up
So does your level of protection. In modern DDoS incidents, attackers often execute attacks in escalating stages, intensifying their efforts to overwhelm the target. Reblaze adeptly mirrors this progression, instantly and automatically bringing additional resources online without any manual intervention necessary
More advanced attacks
So do the defenses in place. Reblaze is equipped with unique adaptive mechanisms that continuously learn and evolve over time. As DDoS and other attack methods become increasingly sophisticated, Reblaze's web security experts proactively deploy countermeasures throughout the network. With Reblaze's vigilant team monitoring the ever-changing threat landscape on the web, your staff can be confident that they are protected without the need to constantly keep up with the dynamic threat environment.
Bot Management
Exclude Hostile Bots From Your APIs and Web Applications
Multivariate Bot Detection
Incoming web traffic undergoes a sequence of progressively stricter challenges. If any of these challenges are not met successfully, the requestor is instantly denied network access and blocked.
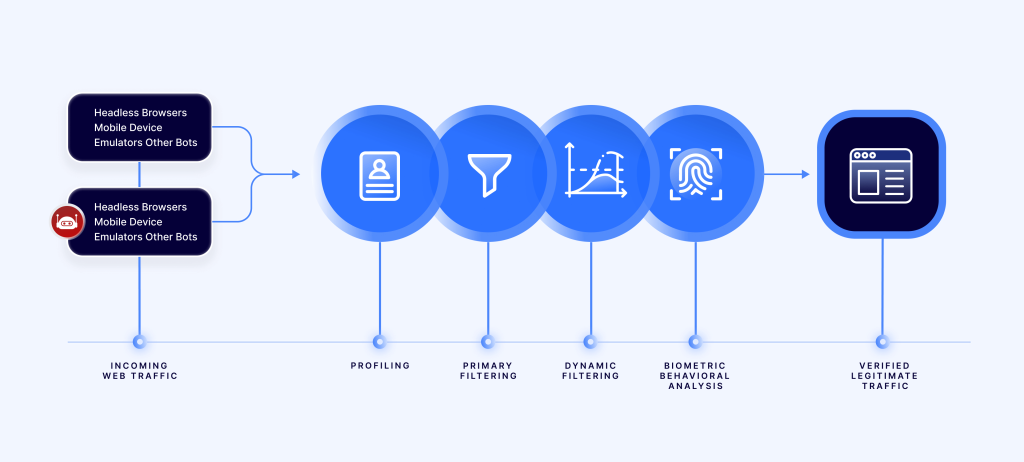
Step 1a: Profiling ACLs
Reblaze offers the industry’s most accurate ACL capabilities, enabling the filtration of requests based on various criteria such as geolocation, network usage (VPN, proxy, TOR, cloud platform, etc.), and more.
Out of the box, this feature can detect 75-80 percent of bot traffic, which further improves when Reblaze is tailored to the specific web app or API it protects. By employing Reblaze’s ACL, the system efficiently eliminates the majority of bot traffic without imposing a heavy processing workload, effectively preempting the need for deep packet inspection
Step 1b: Profiling Browser Environments
For incoming HTTP requests to be validated, they must successfully navigate a comprehensive stack of inspections and challenges.
Beyond conventional methods like agent validation or javascript injection, Reblaze takes it a step further by detecting headless browsers.
Through subjecting the requester to a series of advanced challenges, Reblaze exhibits its ability to identify even the most sophisticated headless environments with precision.

Step 2: Primary Filtering
To initiate primary traffic filtering, Reblaze adopts a multi-faceted approach, starting with blacklisting, rate limiting, and signature detection. This combination effectively eliminates a significant portion of bots, all while keeping the processing workload minimal.
For further scrutiny, the platform employs more rigorous tests. Layer 7 inspection, encompassing examination of JSON payloads, guarantees data integrity.
Additionally, Reblaze includes a full positive security model, and ingests web and API schemas for enforcement. A full API grants programmatic control, facilitating swift schema additions or revisions in both DevOps and DevSecOps environments
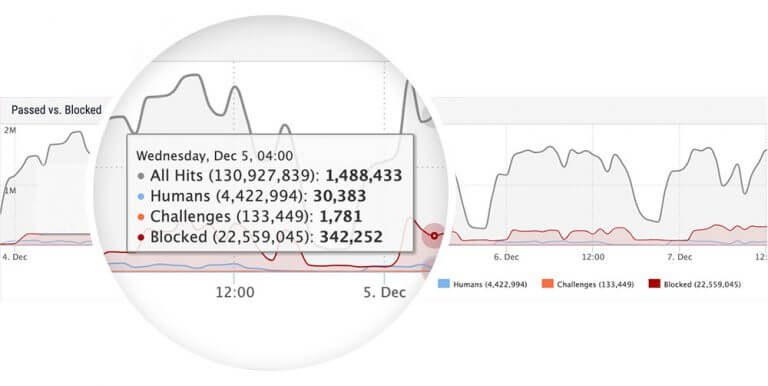
Step 3: Dynamic Filtering
Reblaze effectively prevents access for requestors exhibiting unusual usage patterns over an extended period. It achieves this by continuously monitoring resource consumption in various aspects, such as quantity, pace, rhythm, types, methods, and more.
Unlike many platforms that rely solely on IP addresses for tracking, Reblaze employs multiple identifiers, including IP, headers, cookies, and POST body arguments, to pinpoint attackers. This capability allows Reblaze to detect and thwart abuse even when attacks occur simultaneously from multiple addresses.
The platform’s ruleset capabilities deliver robust, flexible, and fine-grained filtering options, enhancing its effectiveness in managing web traffic and security.
Step 4: Biometric Behavioral Analysis
Reblaze creates an intricate and comprehensive behavioral profile of legitimate users for every application it protects.
Through continuous learning, Reblaze gains deep insights into the authentic users’ interactions with the app, including device and browser statistics, customary analytics, session metrics, and various interface events like mouse clicks, screen taps, zooms, scrolls, and more.
By nature, any hostile user, whether human or bot, will eventually exhibit deviations from the established patterns of legitimate user behavior.
The moment such deviations are detected, Reblaze swiftly identifies and blocks the offender from accessing the network any further.
Try Free Demo
Frequently Asked Questions
What is Reblaze Software?
Reblaze is a cloud-based web security platform that provides comprehensive protection against web threats, including DDoS attacks, bot traffic, application-layer attacks, and more. It offers solutions for web application firewall (WAF), bot management, DDoS protection, and content delivery.
Why should I buy Reblaze software?
Reblaze uses advanced security mechanisms and machine learning algorithms to detect and mitigate web threats in real-time, ensuring websites and web applications remain secure, available, and high-performing even in the face of sophisticated cyber attacks.
Can Reblaze integrate with other security tools and services?
Yes, Reblaze offers integrations with various security tools and services, allowing organizations to extend their security capabilities and create a layered defense strategy against web threats. It seamlessly integrates with SIEM systems, threat intelligence platforms, and more.
What level of support can we expect from you as a Reblaze reseller?
As an authorized Reblaze reseller, we provide comprehensive support to our clients, including Reblaze software demo after you buy Reblaze software.









