Metadata
Metadata software
- Campaign Automation
- Audience Targeting
- Campaign Experimentation
- Lead Enrichment
- Campaign Optimization
Experiment so you can get to revenue, faster
Let your paid campaigns optimize themselves using your opportunity data from Salesforce.
Not just clicks and impressions.
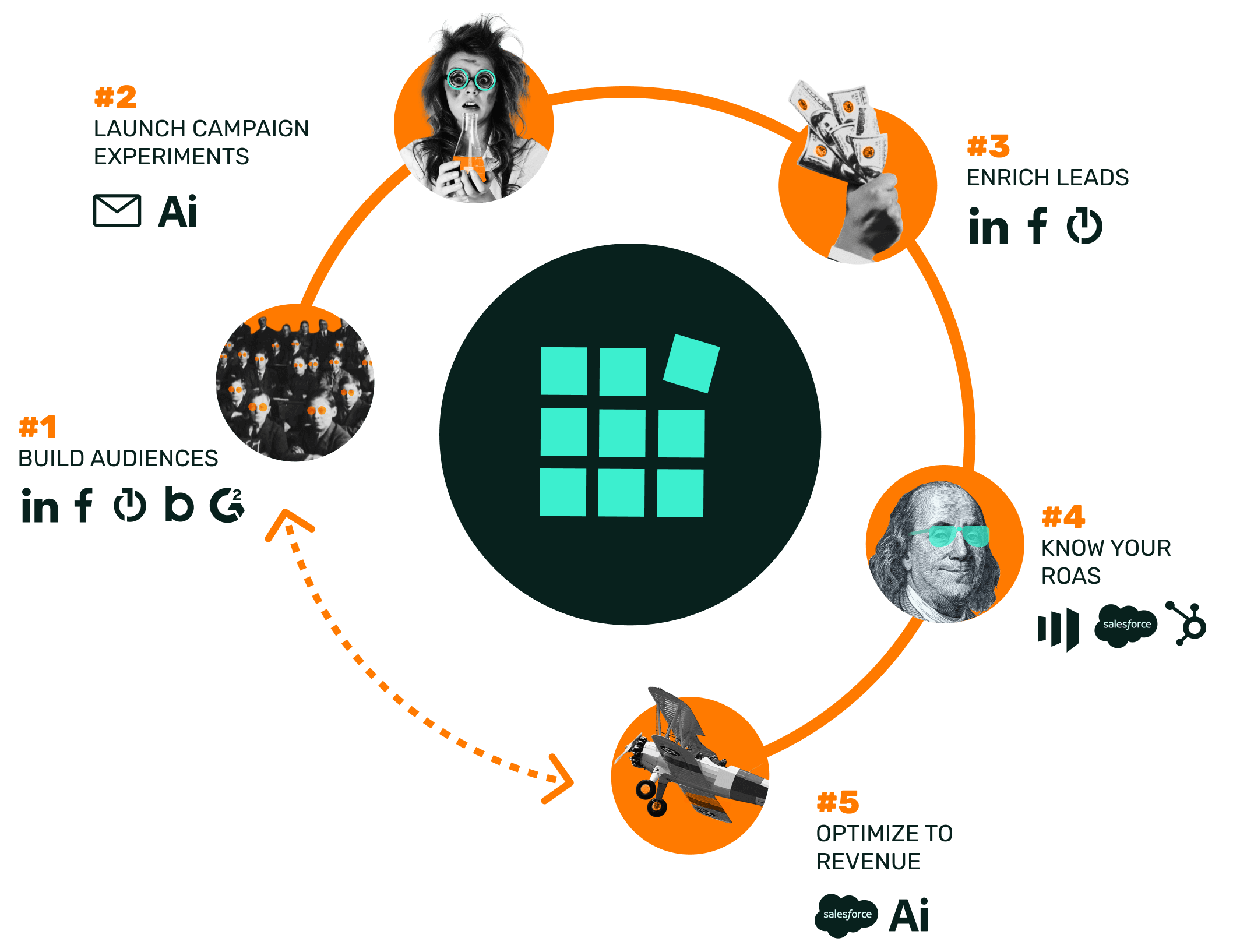
How Metadata works
B2B marketers automate their paid campaigns and drive more revenue with Metadata.

What you can do with Metadata
Audience Targeting
Match business profiles to personal emails so you can reach your best-fit audience across your ad channels. Increase your match rates by as much as 9x on Facebook and 7.5x on LinkedIn.
- Find your target accounts and actual buyers on Facebook
- Use the same data sources and targeting criteria
- Target both companies and people with your campaigns
Campaign Automation
Use the same tool to launch all of your paid campaigns. Save serious time and forget about having to manually build (and rebuild) new campaigns in each ad channel.
- Forget about having to log into multiple tools
- Select all of your campaign assets from a single library
- Focus more on strategy, creativity, and experimentation
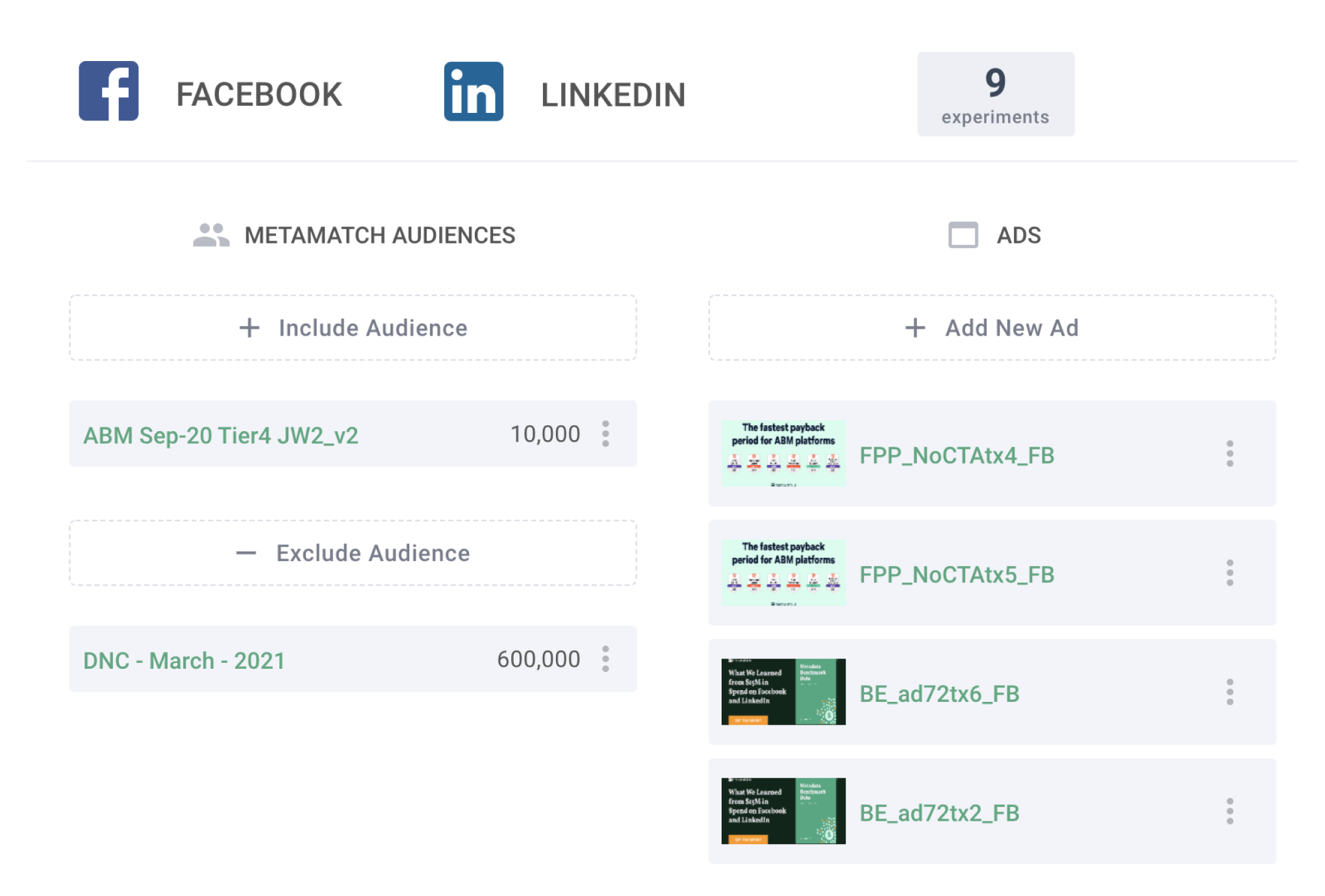
Campaign Experimentation
Experiment, except at scale. Launch hundreds of campaign experiments so you can quickly learn what’s working and more importantly, what’s not.
- Test new audiences, messaging, creative, and content offers
- Push your campaign experiments directly to your ad channels
- Find out what your audience actually wants
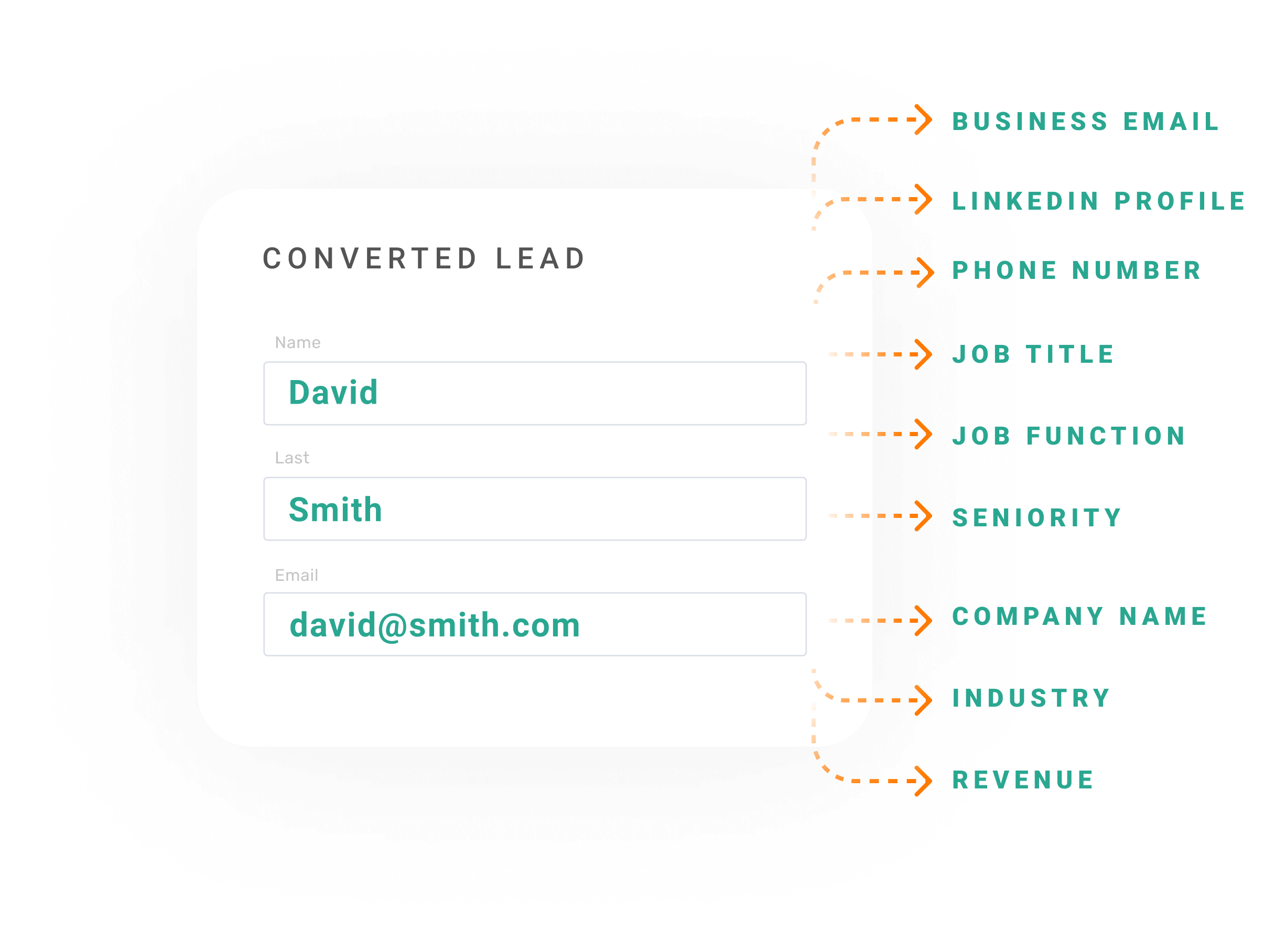
Lead Enrichment
Use a single field on your forms so you can drive more conversions. Enrich new leads from your campaigns with verified business data, automatically.
- Enrich your new leads with up to 20 business attributes
- Forget about stitching multiple data sources together
- Shorten your lead forms and remove friction
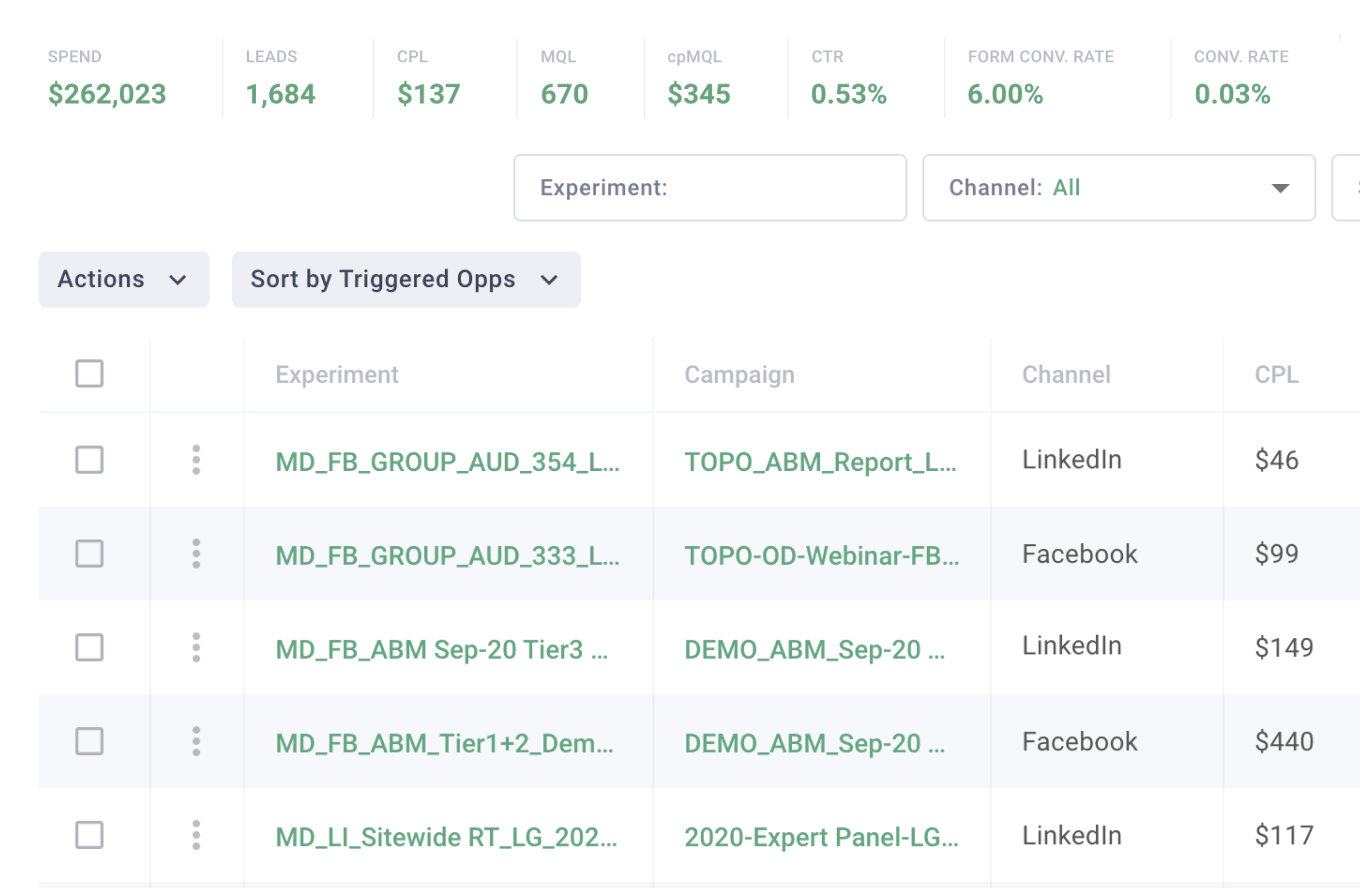
Campaign Optimization
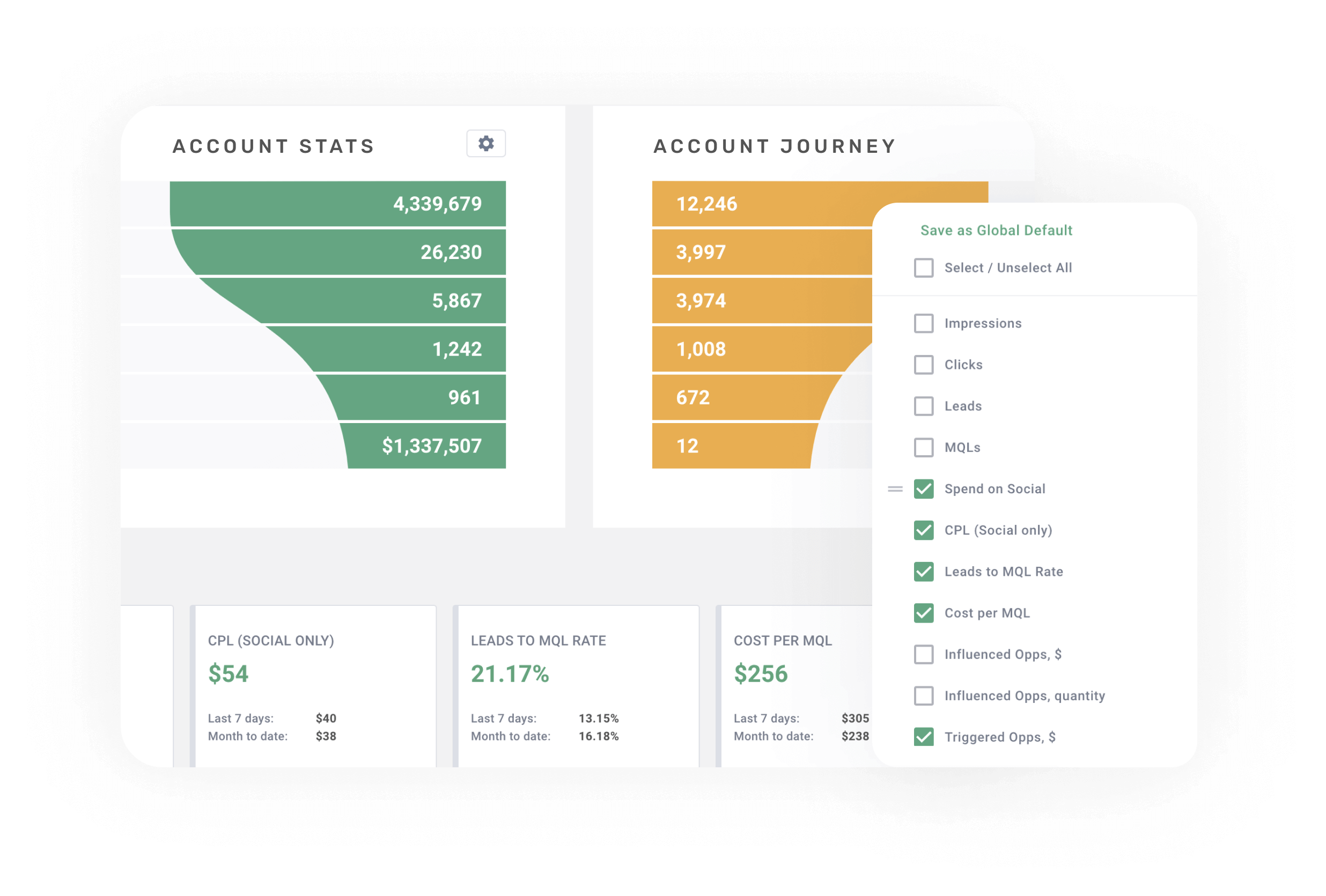
Don’t waste money on underperforming campaigns. Be ruthlessly efficient and let the platform reallocate your budget based on what drives pipeline.
- Customize your metrics, outcomes, and attribution
- Let AI optimize your campaigns using your funnel data
- Know where to spend your demand generation budget
Automate your paid campaigns and drive more revenue
Metadata eliminates manual and repetitive work for B2B marketers so you can focus on strategy and creativity.
Manual work is killing B2B marketers
One boring, repetitive task at a time. But your revenue targets keep getting bigger. And every new campaign creates more technical and mundane work you can’t keep up with. Now there’s a better way.
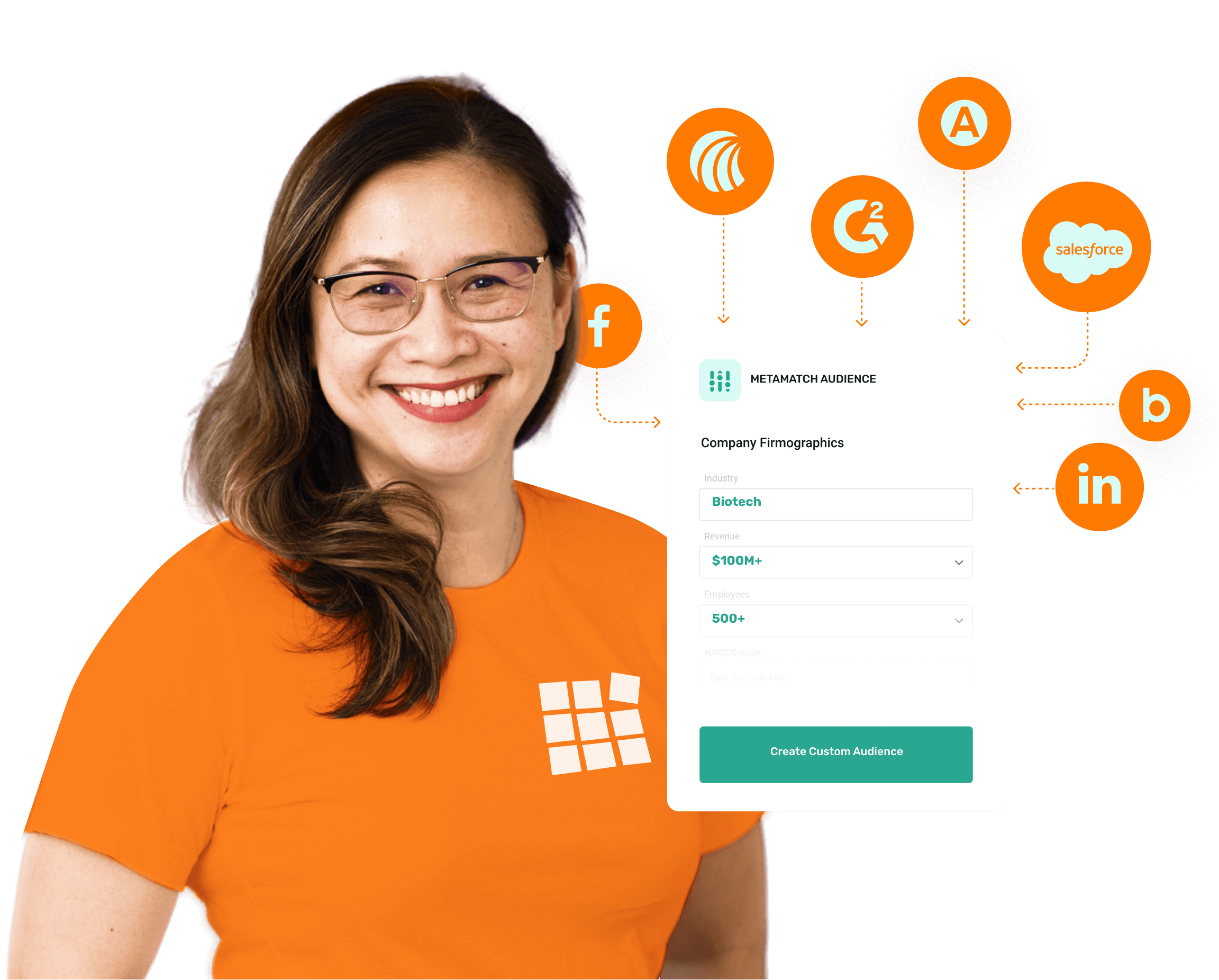
Build better audiences for your campaigns
Increase your audience match rates up to 9x on Facebook and 6.5x on LinkedIn.

We know what you're thinking
My buyers aren’t on Facebook. I’ve tried Facebook before and it didn’t work. Can’t I do this already on LinkedIn? Every one of our customers said the same things too. Until they used MetaMatch.
Welcome to MetaMatch
MetaMatch, our patented personal-to-corporate identity graph, allows you to build laser-focused audiences on Facebook and LinkedIn. Except the match rate is much higher. We match based on email addresses, not cookies or IP addresses.
How MetaMatch works
With MetaMatch, you can match personal emails to legit business emails with our proprietary database of 1.5 billion (with a b) B2B profiles. Metadata customers typically see match rates between 15-45% on Facebook and 50-60% on LinkedIn.
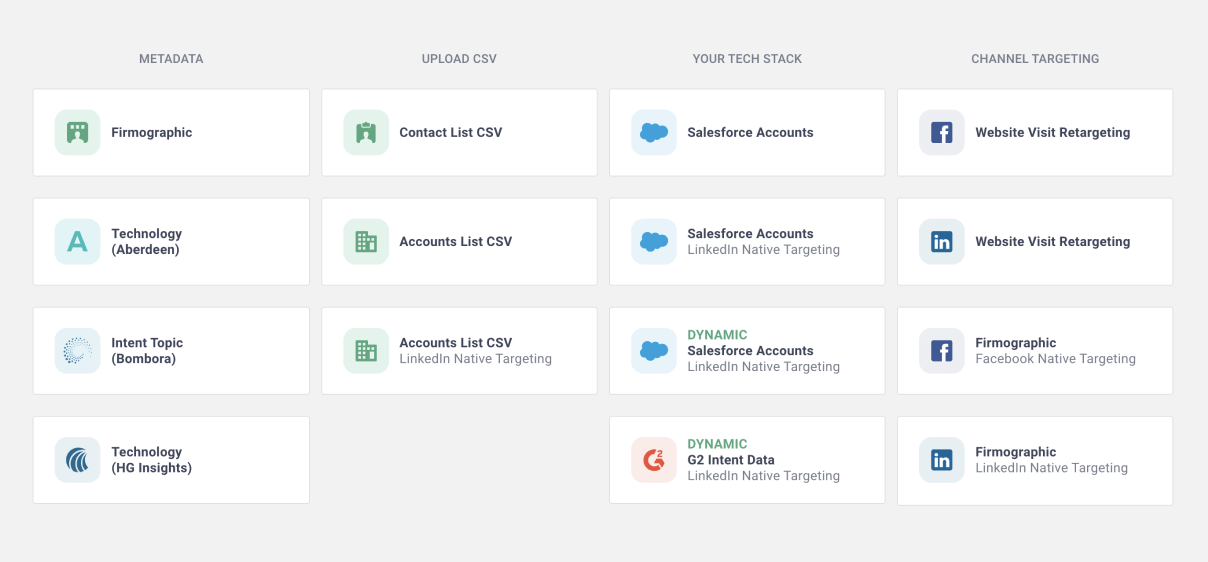
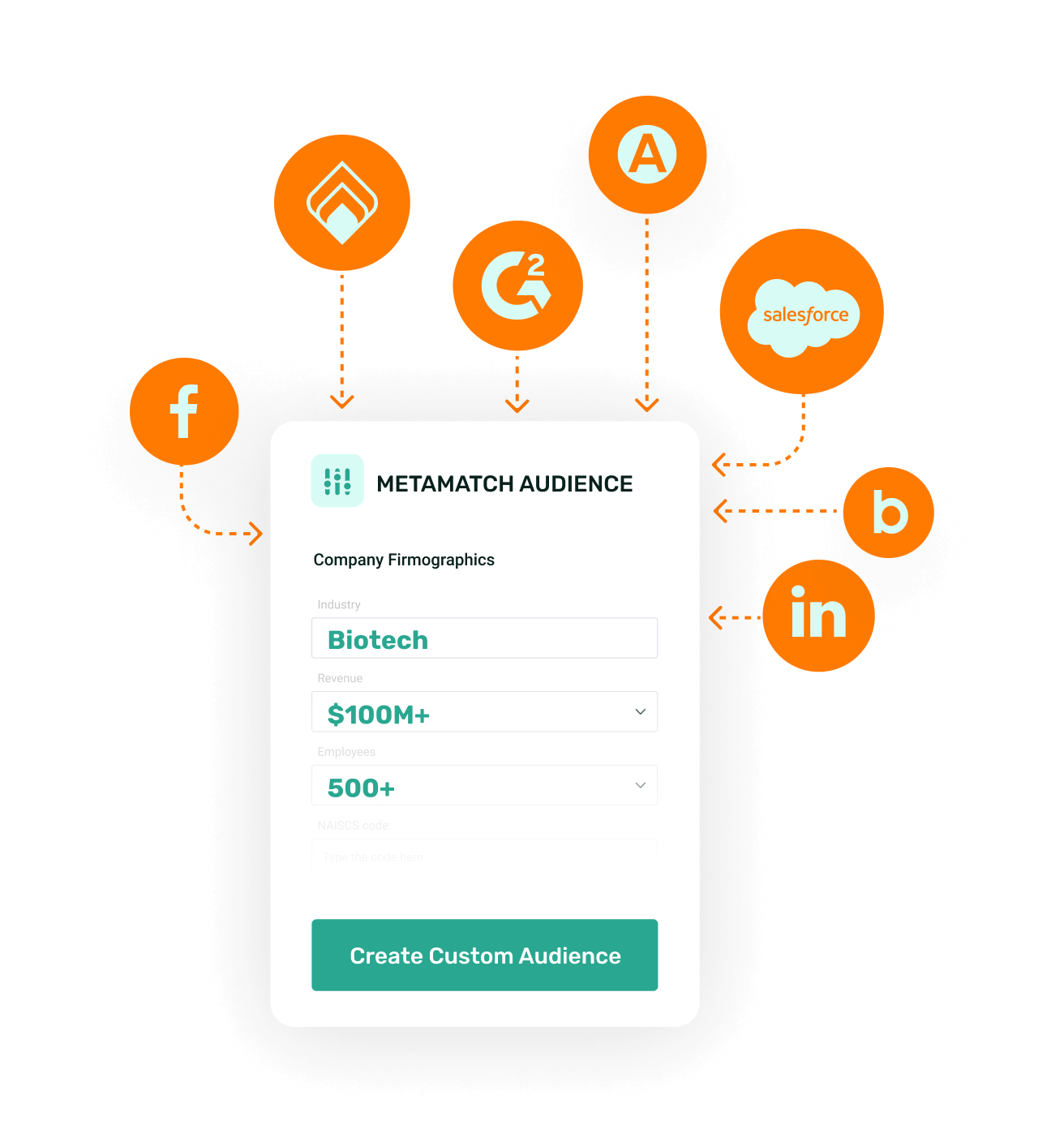
Pick how you want to target your audience
You can create your audiences using 15 different audience types.
- Get the flexibility you need to build the best audiences possible
- Use dynamic account targeting with your own Salesforce data
- Turn your intent data into a cheat code for your campaigns
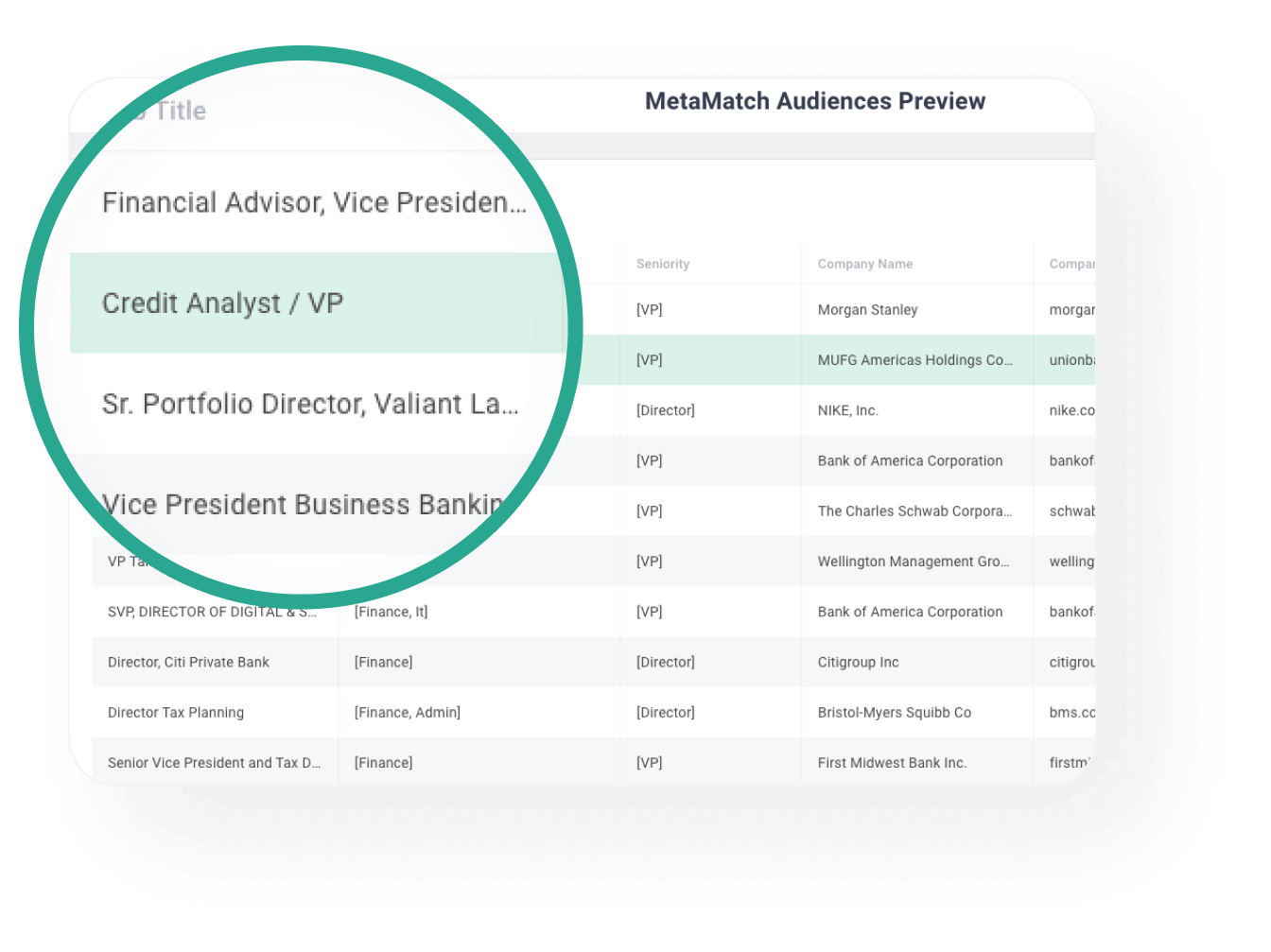
Preview your audiences before you waste any money
You can see which profiles meet your audience criteria before you launch your campaigns.
- See which types of people meet your initial audience criteria
- Refine your criteria to get laser-focused on your audience
- Stop wasting your budget on people who shouldn’t see your ads
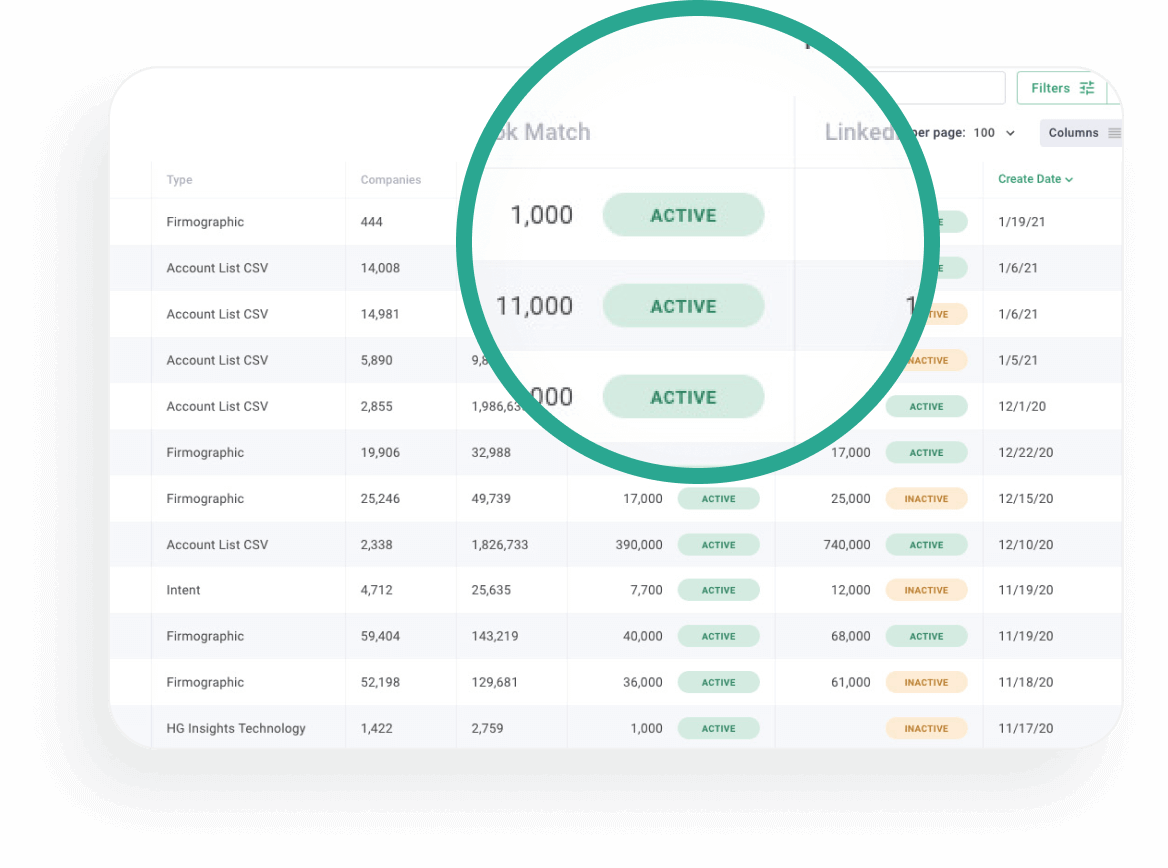
Push your new audiences directly to Facebook and LinkedIn
Forget about spreadsheets and push your audiences directly to each channel.
- Save yourself from having to manually export and upload audiences
- Review your matched audiences directly from Metadata
- Check the status of your audiences so you can start running campaigns
Security, Trust, Privacy
These are the foundational principles the Metadata platform was created from and the principles throughout every aspect of our business. Metadata has engaged independent experts and third parties to verify our security, privacy, and compliance controls, and has achieved related certifications.
SOC 2 Type II Report
We have assessed and audited our security as set forth in TSP section 100, 2017 Trust Services Criteria developed by the Assurance Services Executive Committee (ASEC) of the AICPA. The Trust Services Criteria is a set of control criteria to be used when evaluating the suitability of the design and operating effectiveness of controls relevant to the security, availability, or processing integrity of information and systems and the confidentiality or privacy of the information processed by Metadata.
We maintain a SOC 2 Type II report, which is designed to certify that the controls we maintain meet a high level of security. Our SOC 2 Type II report is available to all customers at any time.
Stringent Security Controls
Metadata monitors hundreds of internal and external security controls across our organization using a centralized automation and compliance management platform. Automated alerts and evidence collection are designed to allow Metadata to verify its security and compliance posture on an ongoing basis while fostering a security-first mindset and culture of compliance across the organization.
3rd Party Penetration Testing
Metadata completes annual 3rd party penetration testing by a qualified 3rd party assessor. Summaries of these reports are available to any Metadata client who requests them.
Phishing Testing
We have simulated phishing exercises with all worldwide staff using realistic phishing emails and methods. Employees are required to retrain should they fall victim to a simulated phishing attack and all staff are encouraged to submit suspicious emails and other phishing attempts to an internal system which monitors attempts to compromise our platform through social engineering methods.
Annual Security Training
We’ve partnered with a security awareness and training company that covers dozens of major topics for our employee training. Every new employee and contractor is required to take this training. As the threat landscape for companies is ever changing, new training is assigned to all staff periodically which covers new and relevant topics
Secure by Design
We strive to adhere to the principle of least privilege when connecting to customers’ environments and to scope our access to only what’s reasonably needed to satisfy the needs at any given point of customers. We log this activity and monitor it for compliance with internal controls.
Application
Web Application and Next Generation Firewalls
Metadata uses a Web Application Firewall (WAFs) coupled with Next Generation Firewalls (NGFW) designed to block against the latest threats spotted around the world.
Encryption
A minimum of Transport Layer Security (TLS) version 1.2 for data in transit and encryption at rest is used through all instances and confidential and secure networks. AES 256 is used to encrypt data at rest within our platform to assist with the protection of confidential customer data.
Infrastructure
Metadata makes use of trusted third party tools and platforms in an effort to protect its infrastructure, including to help ensure that only quality code is committed and released to production and that malicious modifications to our code are not introduced into production. Code merges undergo a static code analysis check prior to the code being merged to the main, which is designed to identify vulnerabilities in real-time.
Third Party Library Scanning
We regularly scan all of our libraries to help ensure we do not have vulnerable libraries in the codebase
Credential Checking
We scan our codebase to help ensure that credentials are not accidentally merged into code.
Peer Reviewed Merges
Along with our two-approver requirement, all code is peer-reviewed by a Senior Engineer before being merged to the main and released to production.
Endpoint
Mobile Device Management
All of our devices are centrally managed with policies around security, patching, and encryption enforced.
Endpoint Detection Response
Metadata uses technologies designed to ensure endpoint security, including antivirus and antimalware tools intended to identify and respond to potential threats.







