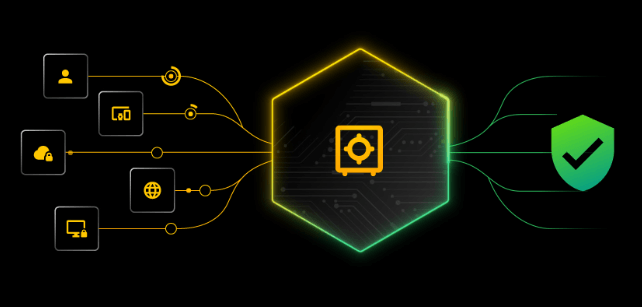
Revolutionizing Privileged Access Management

Use KeeperPAM, a cutting-edge, zero-trust cybersecurity technology, to secure and control access to your vital infrastructure.
PRODUCTS
Enterprise Password Management
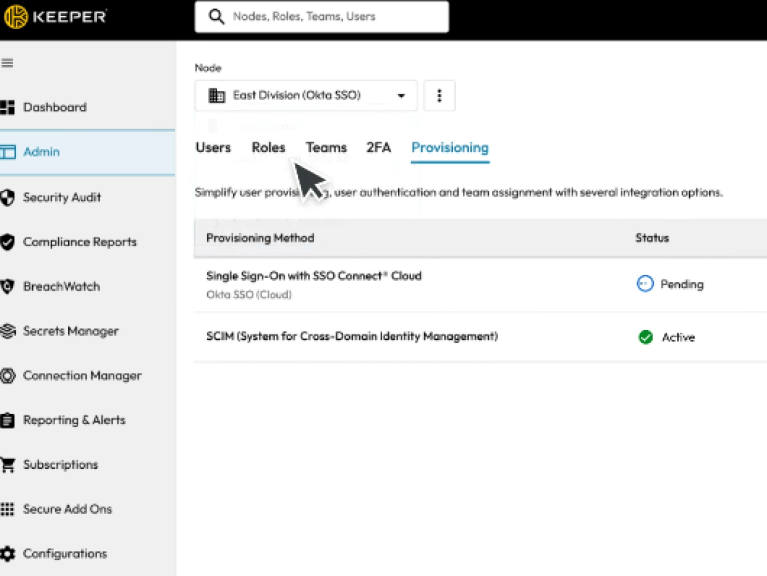
Keeper gives administrators extensive visibility, delegated administration, and fine-grained role-based enforcement procedures. Advanced reporting tools can be accessed via APIs, the command line, or the Admin Console user interface. Predetermined benchmarks are provided by the Risk Management Dashboard to guarantee that your company keeps the most secure setup.
Reduce standing access, minimize shadow IT, streamline audits, and comply with Sarbanes-Oxley (SOX) using Compliance Reports. Establish passphrase and password complexity parameters to make sure credentials meet industry and corporate standards.
Keeper gives administrators extensive visibility, delegated administration, and fine-grained role-based enforcement procedures. Advanced reporting tools can be accessed via APIs, the command line, or the Admin Console user interface. Predetermined benchmarks are provided by the Risk Management Dashboard to guarantee that your company keeps the most secure setup.
Reduce standing access, minimize shadow IT, streamline audits, and comply with Sarbanes-Oxley (SOX) using Compliance Reports. Establish passphrase and password complexity parameters to make sure credentials meet industry and corporate standards.
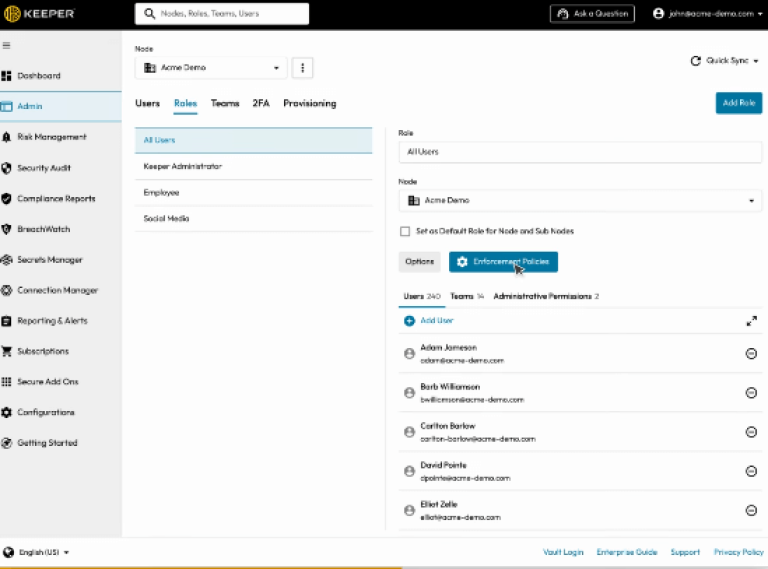
With more than 300,000 5-star reviews and millions of users globally, Keeper is designed to be user-friendly. For the best user experience, consumers can utilize their preferred platform with the help of the online vault, browser extensions, desktop apps, and mobile apps. To guarantee data isolation and protect your personal and professional lives, alternate between personal and commercial vaults.
By automatically typing in your passwords, passkeys, and 2FA codes, Keeper’s unique KeeperAI makes it simple for you to connect into websites and apps instantaneously. With a single click, users can safely share anything in their Keeper Vault, including files, photographs, and passkeys.
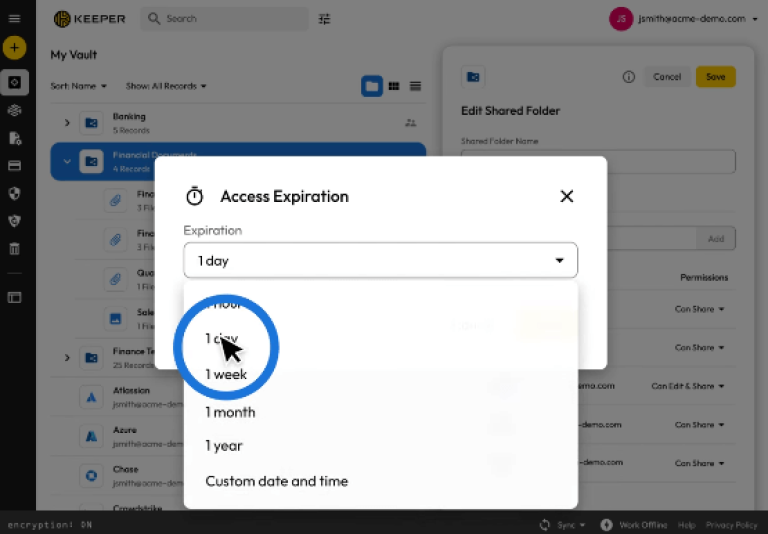
Use time-limited access, direct sharing, one-time sharing, shared folders, team folders, and self-destructing records to collaborate safely. Elliptic curve end-to-end encryption is used by Keeper’s sharing technology to guarantee that only authorized users can access data.
Teams can be added to shared files and synced straight from your identity provider, which lowers administrative burden and boosts corporate efficiency. Granular control over what can be shared both inside and outside the company is possible with role-based sharing policies.
Privileged Access Management
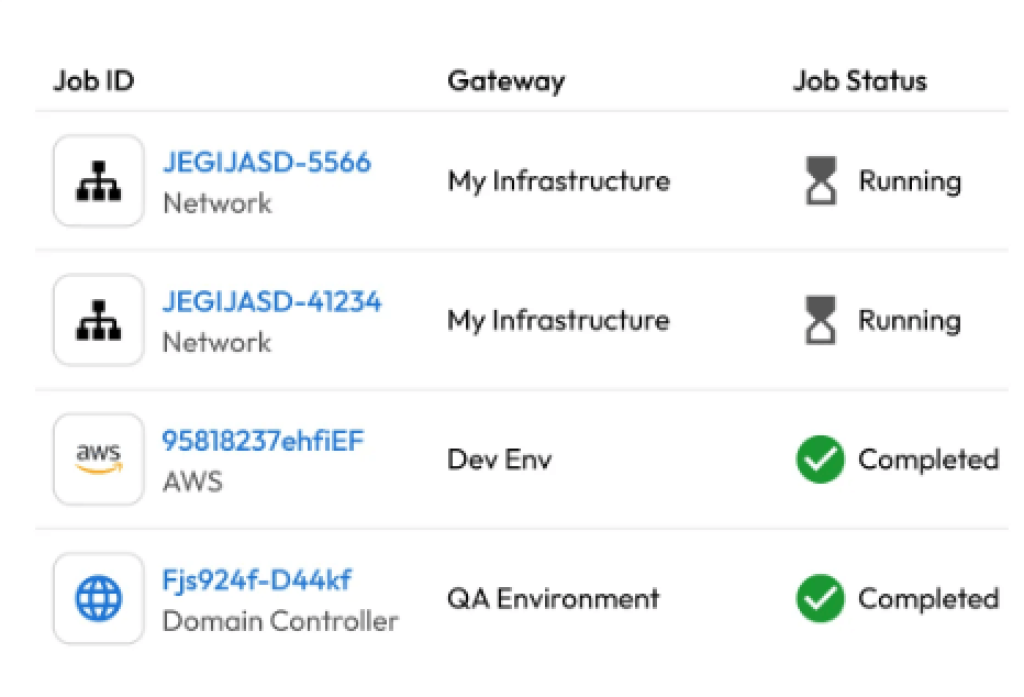
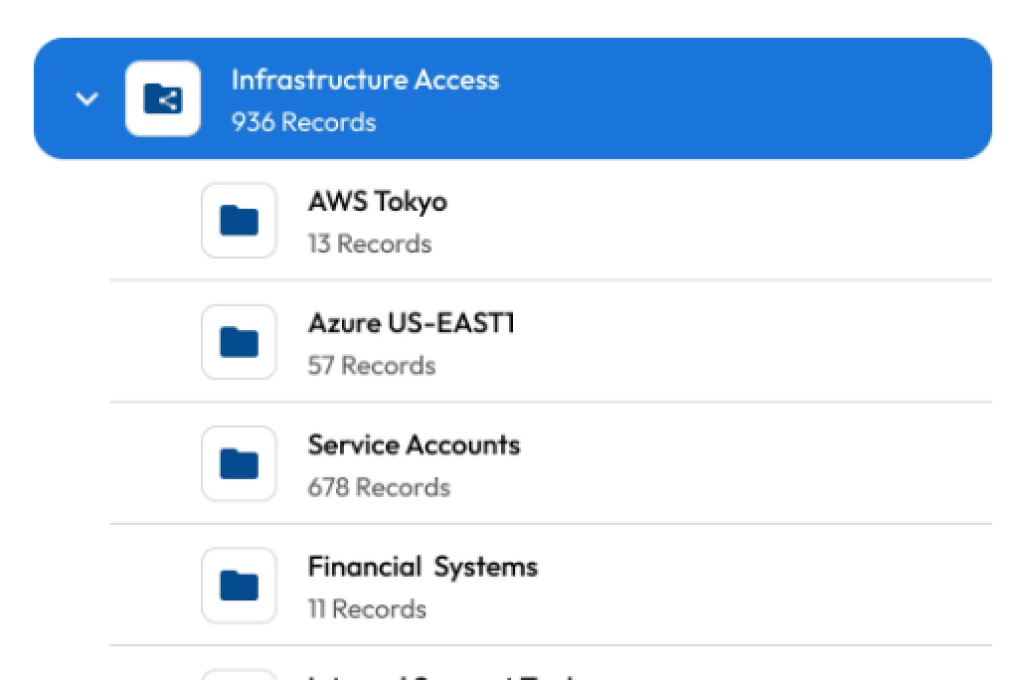
DevOps, IT security, and software development teams are empowered by Keeper Discovery, which gives them consolidated access to all privileged accounts and IT assets across local infrastructure, AWS, and Azure environments.
Organizations can import machines, databases, directories, accounts, and credentials into the Keeper Vault as controlled resources by using the Keeper Gateway to automatically find and classify these resources.
Every user in the company is fully covered by the Keeper Vault. Consistent policies are used to grant access, and KeeperPAM interacts with all network infrastructure and Identity Providers (IdPs).
Tunnels and connections made between Keeper and the target infrastructure are encrypted from beginning to end using a zero-knowledge and zero-trust architecture. To assist comply with CISA’s strict regulations, public sector businesses can safeguard their operational technology (OT) environments.
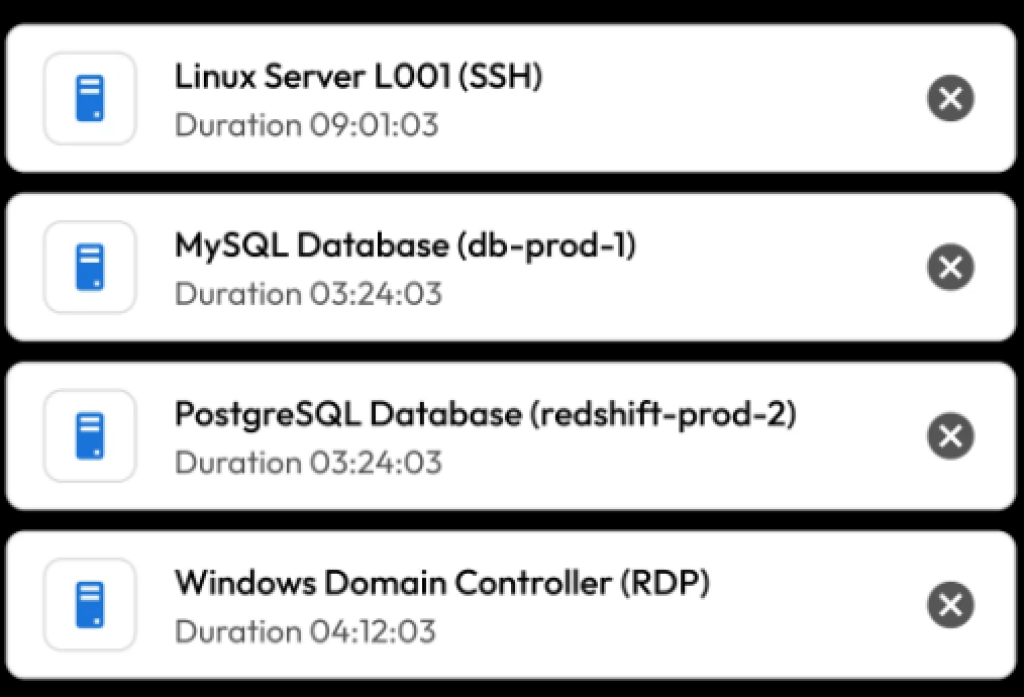
Experts in browser-based remote session protocols, including SSH, RDP, VNC, HTTPS, MySQL, PostgreSQL, SQL Server, and more, Keeper’s engineers were the original developers of Apache Guacamole.
KeeperPAM employs a zero-trust gateway service to access each environment. There is no requirement for firewall updates or ingress modifications, allowing for simple, safe access.
The passwords and SSH keys are never accessible to the user thanks to Keeper’s remote session features.
Credentials automatically rotate once access has been revoked, and access to a resource may be time-limited. KeeperPAM provides just-in-time access without standing privileges by supporting dynamic role or group elevation and ephemeral account provisioning. Additionally, while utilizing native tools, users can access resources through connection templates, receive temporary credentials with post-session rotation, or connect using their own private credentials.
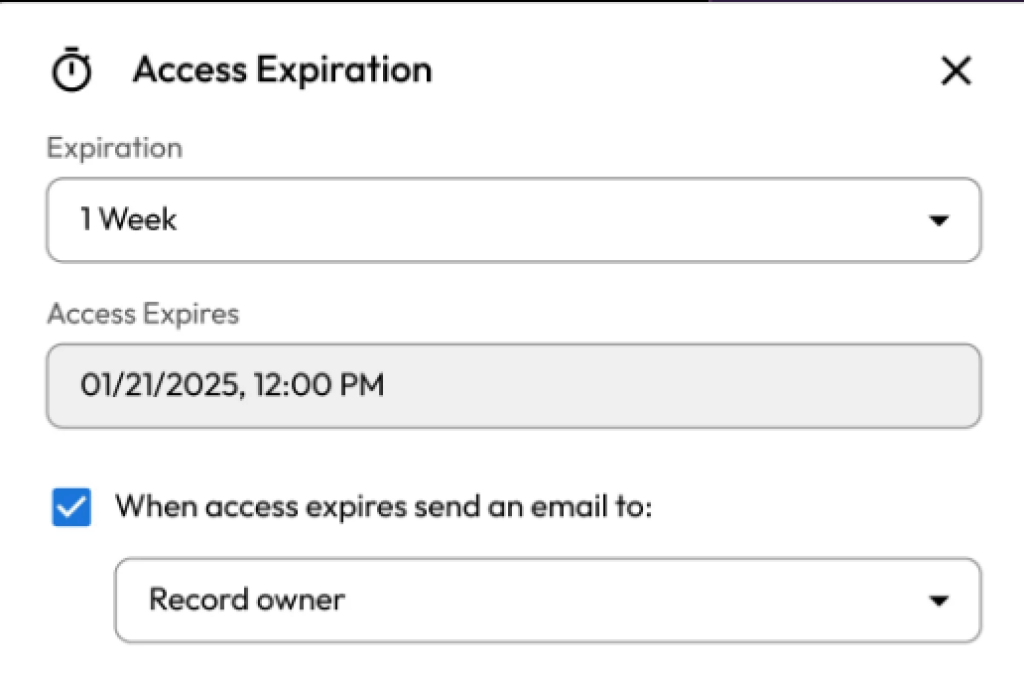
Supports multi-protocol session recording
Every protocol, including SSH, RDP, VNC, databases, and web browser sessions, can have its screen and keyboard activities recorded by remote sessions.
Enforce MFA protection on every system
Add a Multi-Factor Authentication (MFA) layer to both on-premises and cloud infrastructure, including resources that MFA does not support natively.
Automate password rotation
Secure service accounts on both cloud and on-
premises systems.
Simplify developer’s lives while streamlining security
Finally, developers can enhance security without encountering any difficulties due to superfluous network configurations.
Remote Browser Isolation
AppGate’s Third-Party Risk Management (TPRM) service secures external connections with Zero Trust, reducing exposure, accelerating onboarding, and ensuring continuous compliance.
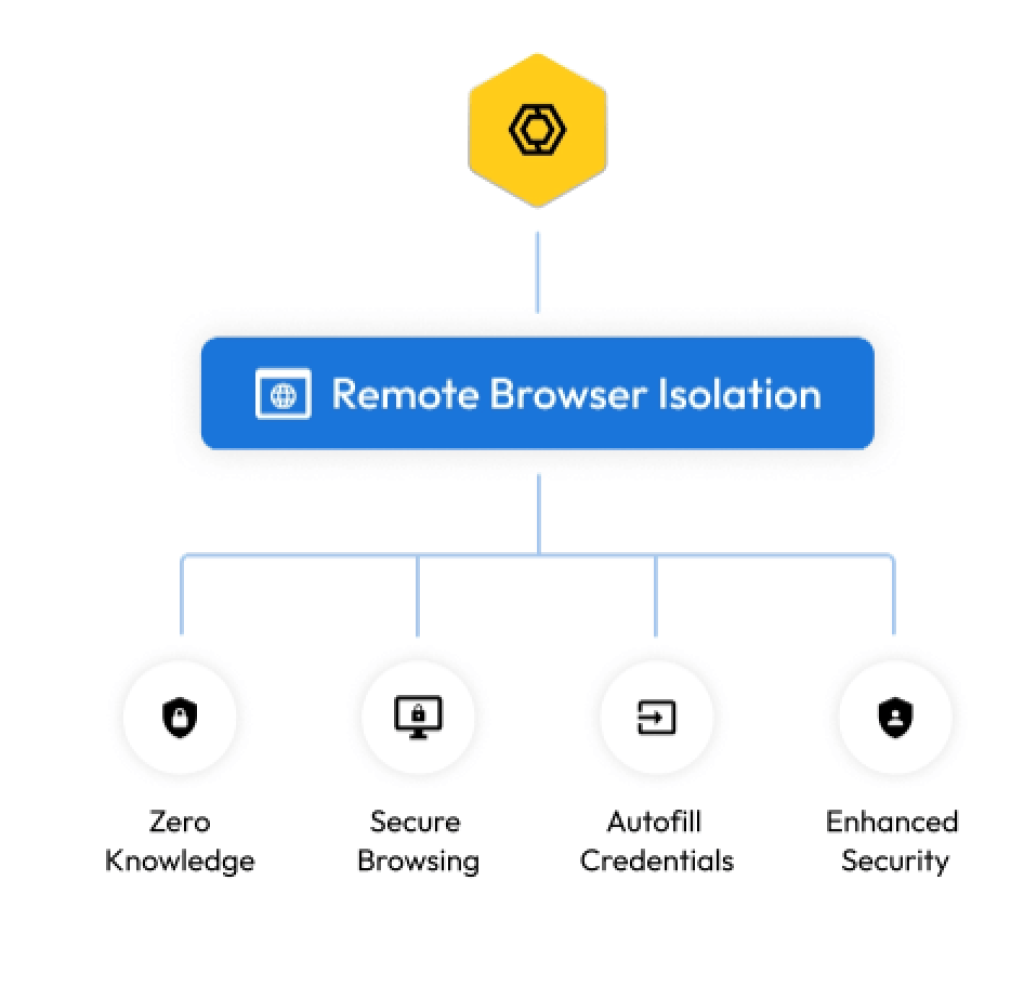
- Zero knowledge security: The customer is in full control of all network communications between the user’s device and the target websites and applications
- Easy to deploy: By simply publishing a Keeper Connection Manager container to any target environment, access to web-based resources can be restricted, monitored and controlled
- Secure and simplified web browsing: Access internal and external sites securely, without data exposure risks if a device is compromised
- Autofill credentials: Keeper’s remote browser isolation protocol can automatically inject credentials, submit forms and control the target web application without ever sending the credentials to the user’s device
- Enhanced compatibility and security: Keeper Remote Browser Isolation is visually projecting a virtualized instance of the latest version of the Chromium browser from the Keeper Connection Manager container through the user’s device, without transmitting any confidential or sensitive data
- Session recording: Just like other Keeper Connection Manager protocols, browser isolation sessions can be shared, recorded and monitored for compliance and auditing
- Zero Knowledge: All browsing activity flows through the customer’s Keeper Connection Manager container – not through Keeper’s servers
- Admin control: Specify allowed websites with precision based on domain, subdomain, path and wildcards for tailored access control
- Action restrictions: Customize browsing sessions by enabling or disabling actions like file uploads/downloads, clipboard use and more
- Protects against web-based threats while ensuring secure access to internal tools and applications
- Reduces the complexity and maintenance overhead associated with VPNs and traditional remote access solutions
- Meets strict compliance standards with detailed access logs and session recordings