Outspeed Attackers with
AI-Powered Penetration Testing
Single Stage for Robotized Pen Testing, Nonstop Computerized Red Joining and NextGen Assault Surface Administration
Why Traditional Pen Testing Fails?
OrganizationsPen Test
Only Partial Asset
Inventory
Associations normally secure their most significant resources, neglect to test pre-nudge resources that frequently have creation information. Programmers know this, and continue to really look at your fringe resources for weaknesses.
Organizations Pen-Test Yearly/Quarterly; Hackers Attack Continuously
Programmers exploit new weaknesses in no less than 24 hours to 12 days, while organizations require as long as 30 days to find, check, focus on and fix weaknesses.
Pen-Testing Is Largely Manual, Costly & Time Consuming
Divided apparatuses, misleading positive alarm exhaustion,
costly specialists and little
groups mean the heroes are extended.
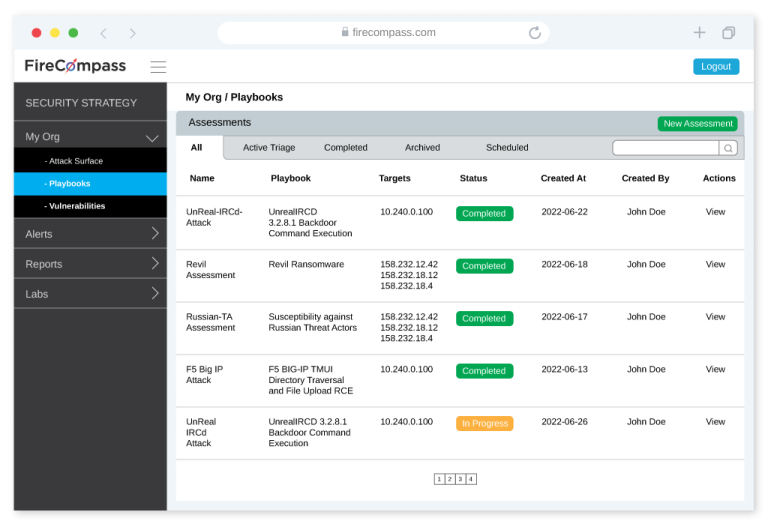
AI Powered Single Platform for Automated Pen Testing, Red Teaming & NextGen Attack Surface Management
AI based Recon: Discover Unknown Risky Assets in Real Time
AI based Pen Test: Run complex multi-stage attack paths at scale
AI based Red Teaming: Test Your Security Control Effectiveness Against Specific Adversarial Goals
AI + Humans: Pen Test as a Service (PTaaS) To Reduce Complexity and Cost
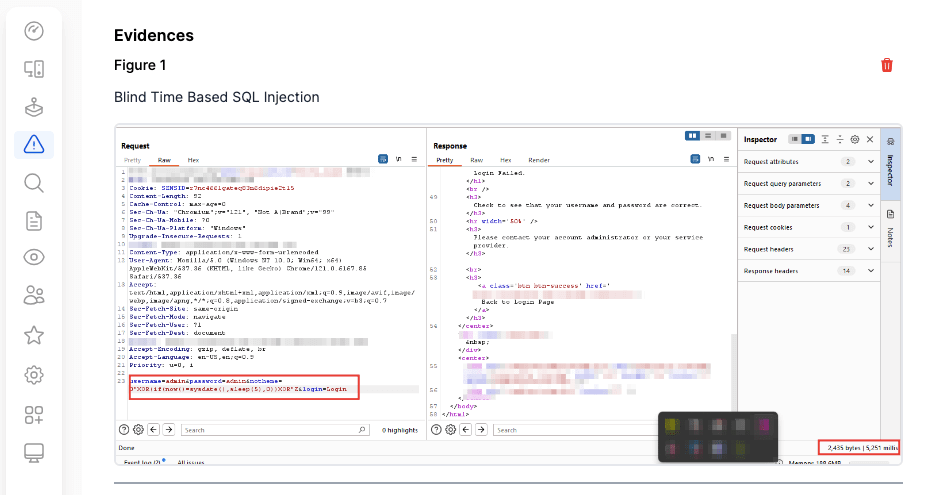
Prioritized Alerts with no False Positives
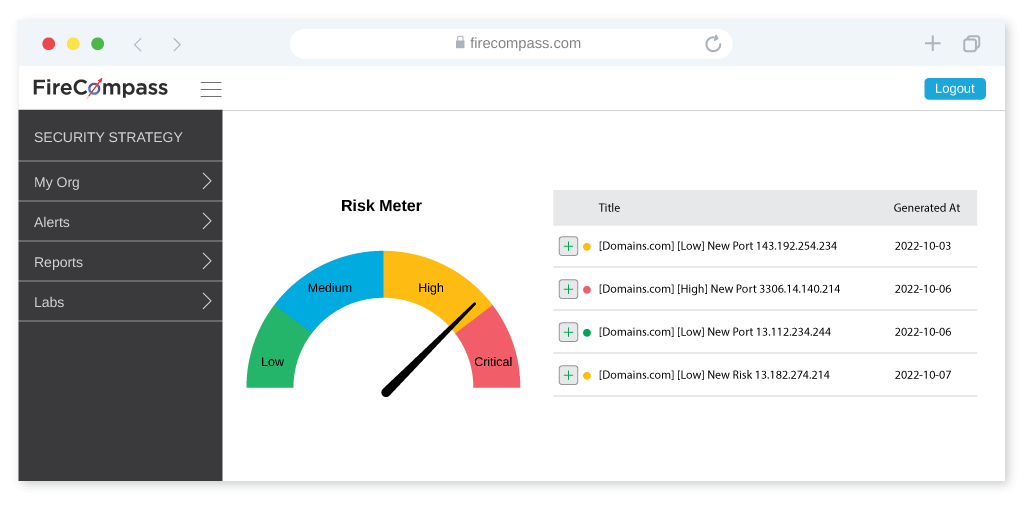
Attack Surface Management (ASM)
Why is Attack Surface Management (ASM) Important?
ASM, Assault Surface Administration distinguishes both known and obscure resources, and, focuses on found gambles and weaknesses. It tells an association the resources and applications that are apparent in the public space to an enemy.
Potential Risks Without Attack Surface Monitoring Tools:
- Rise in Shadow IT Assets and Risks
- Lack of visibility on unknown & orphaned Apps, Exposed databases, and APIs
- Lack of attack surface visibility on entry points for a hacker
How FireCompass Helps
Discover Risky Assets Before Hackers Do
FireCompass assists with avoiding outer breaks which could occur because of weaknesses in dangerous resources where the association has no assault surface perceivability or has lost perceivability
Reduce Your Digital Attack Surface
FireCompass assists associations with decreasing their Computerized Assault Surface by recognizing all pointless open ports/administrations and all potential weaknesses from Known and obscure resources
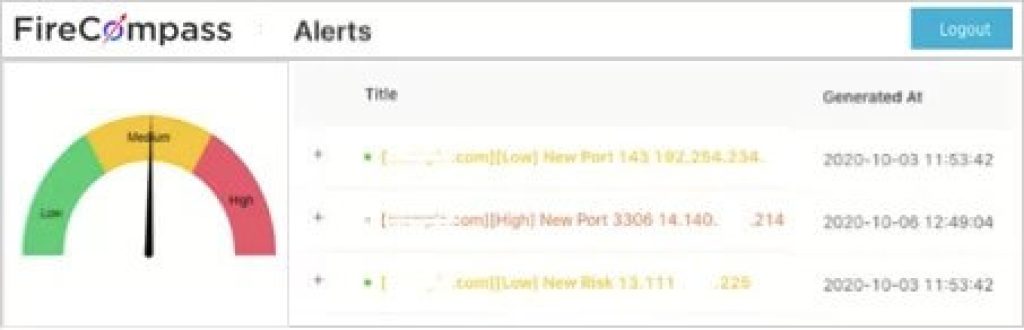
Monitor Continuously & Get Real Time Alerts
FireCompass consistently examines the web and
gives alarms on any
progressions or dangers
related with your
computerized impression
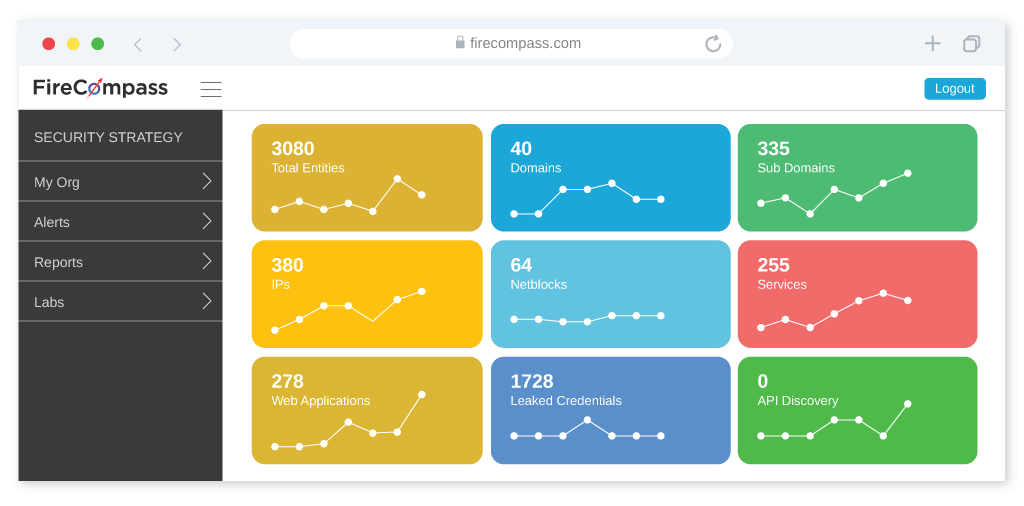
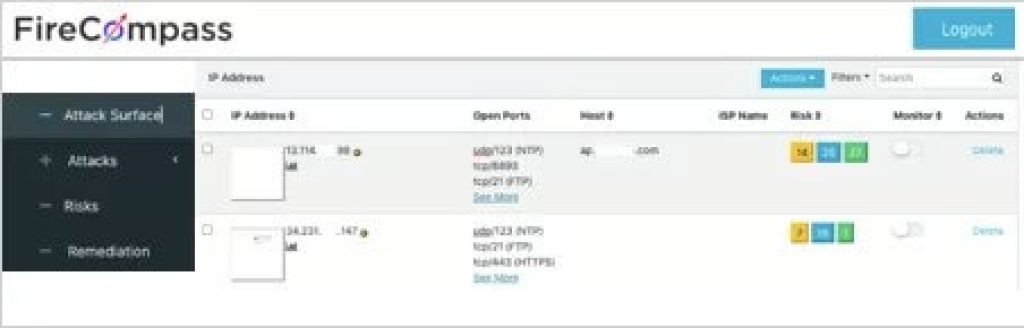
Discover Risky Assets
By using our Attack Surface Monitoring Tool, we provide Attack Surface Visibility to enable you to understand your assets and risks associated.
With FireCompass Attack Surface Management Platform:
- We help you discover the exposed infrastructure
- Create an inventory of the exposed Assets
- Identify vulnerable database servers and cloud buckets.
- Identify exposed domains and subdomains.
- Identify vulnerabilities in Applications
Reduce Your Digital Attack Surface
With our Attack Surface Management tool, we help you to reduce attack surface by:
- Identifying malicious infrastructure.
- Determining the exposed APIs and RDP among other surfaces.
- Determining the exposed documents & files, IoT infrastructure.
Monitor Continuously- Get Real Time Alerts
Benefits of Using FireCompass
Attack Surface
Reduction
Risk Based
Prioritization
Continuous Attack Surface Monitoring
Digital Footprint & Automated Shadow IT Risks
Your Digital Footprint & Risks
A few high profile breaks were caused because of Shadow IT. Computerized resource the board assists you with planning your whole advanced impression of known and obscure resources and the best advanced resource the executives apparatuses assist with lessening both, your Shadow IT and related gambles.
Most Dangerous Causes of Security Breaches
- Applications used by teams unknown to security team(Shadow IT)
- Attacks on Unknown or orphaned applications, database,
- APIs & Misconfigured Cloud Assets
- Lack of visibility on entry points for a hacker (through internet exposed assets & infrastructure)
How FireCompass Helps
Discover Your Digital Footprint & Shadow IT
Find your Information, Applications and Administrations which are freely uncovered on the Web, deliberately or unexpectedly.
Identify & Eliminate Shadow IT Risks
Gives total and consistently refreshed stock of web confronting advanced resources which assists with taking out Shadow IT Dangers
Monitor Continuously & Get Real Time Alerts
Continuosly screens and gives close to ongoing perspective on your advanced impression and dangers related
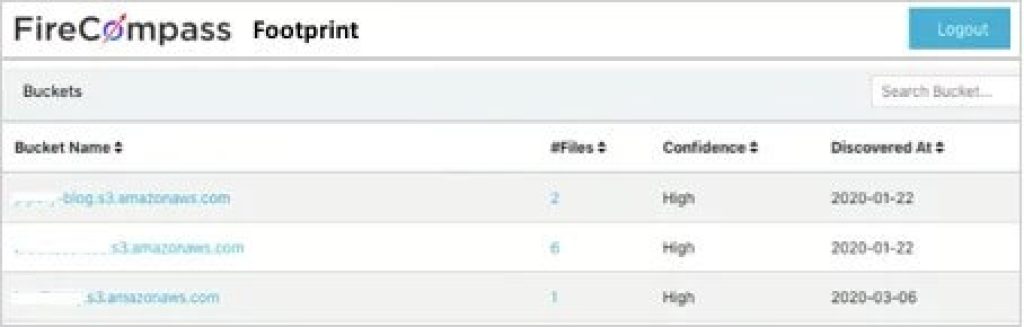
Discover Your Digital Footprint & Shadow IT
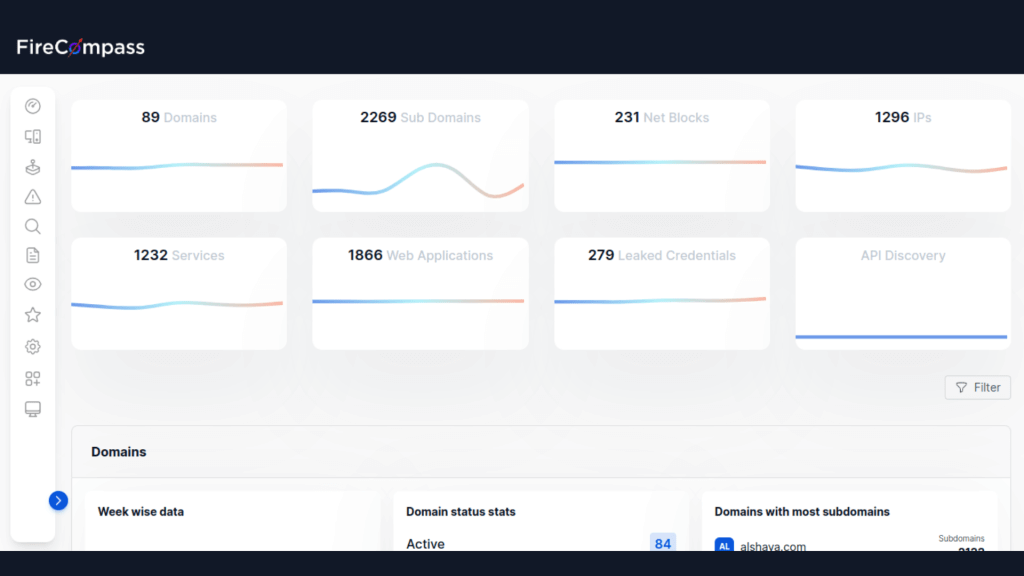
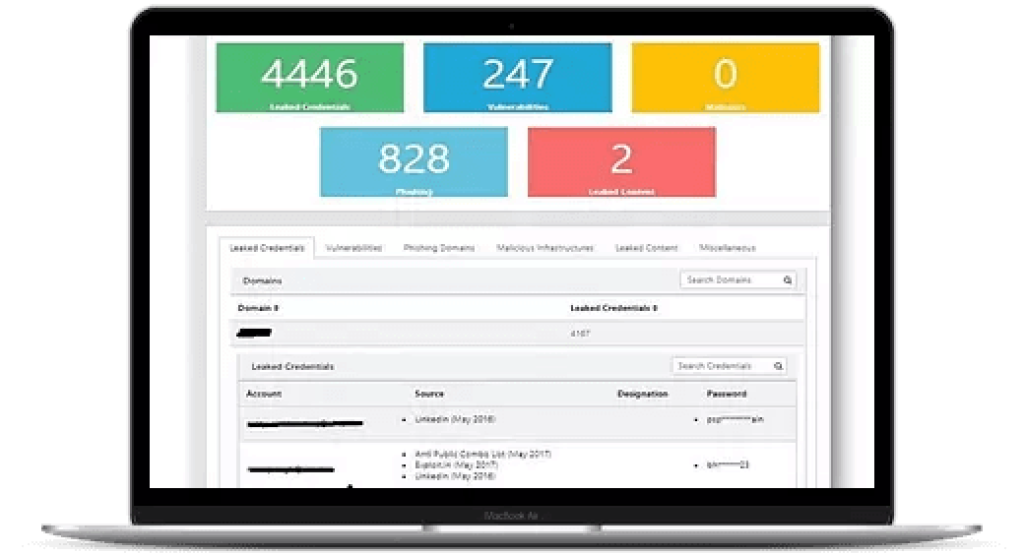
FireCompass automatically discovers an organization’s ever-changing digital footprint including shadow IT, unknown exposed databases, cloud buckets, code leaks, exposed credentials, risky cloud assets and open ports, etc. This includes identifying your:
- Enumerate vulnerabilities (CVEs, takeover Risk etc.)
- Discover exposed database servers & cloud buckets
- Discover domains, exposed applications & websites
- Identify exposed documents & files
Identify & Eliminate Shadow IT Risks
FireCompass helps organizations to track all the exposed digital assets. It helps to discover & mitigate Shadow IT risks by providing complete and continuously updated inventory of internet facing digital assets. It helps in –
- Identifying exposed documents & files
- Identifying compromised / malicious infrastructure
- Identifying exposed services like APIs and RDP
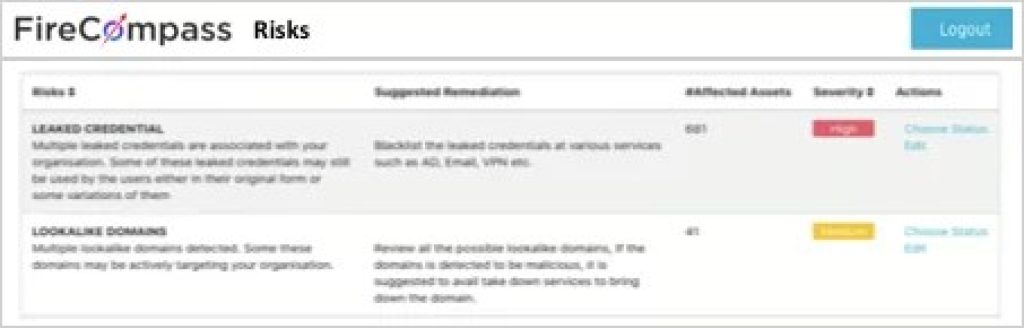
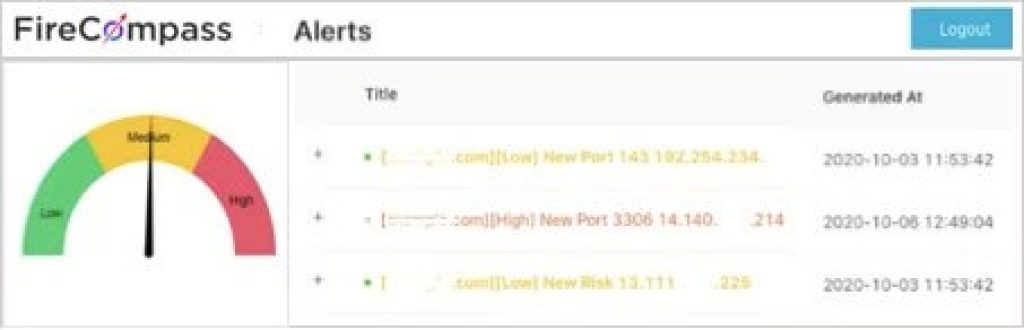
Monitor Continuously
Benefits of Using FireCompass
Mitigate Shadow IT Risks
Complete Asset Inventory
Single Platform
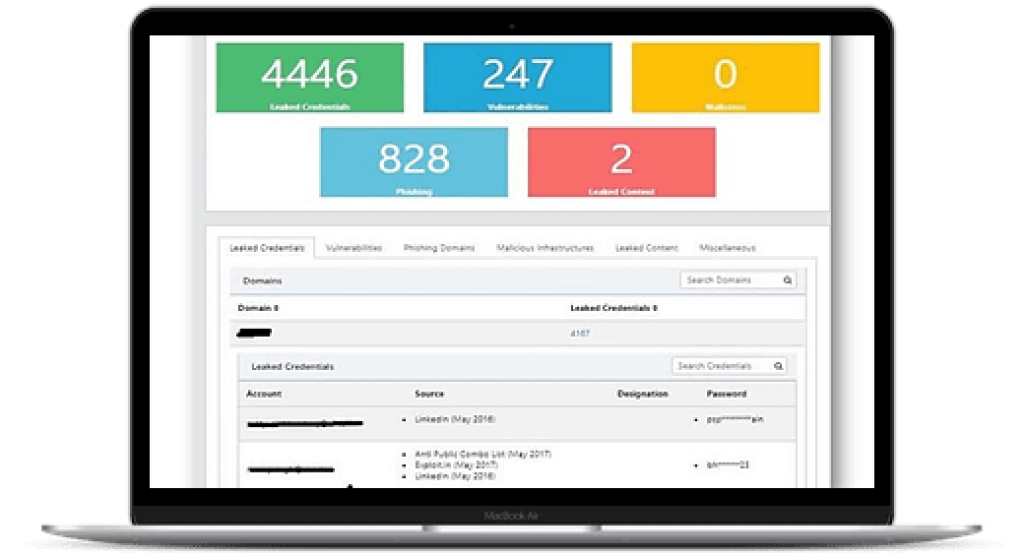
Dark Web Monitoring
Know about your Enterprise’s exposed critical data and passwords
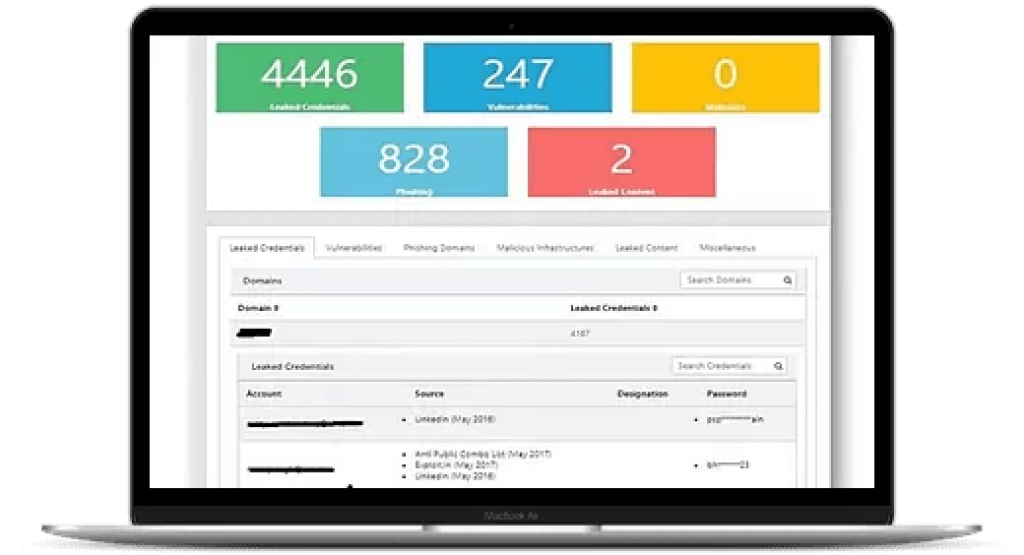
Monitor & Detect Compromised Credentials and Sensitive Data, across the Dark Web
Detect Breached Credentials (E-mails & Passwords)
Identify leaked credentials which are available on the dark web
Identify source of data breach
Detect Leaked Information and Sensitive Data
Discover leaked data across dark web, including sensitive files, financial / credit card
Extensive Monitoring of Dark Web for Organization Specific Intelligence
Recon & Attack Platform
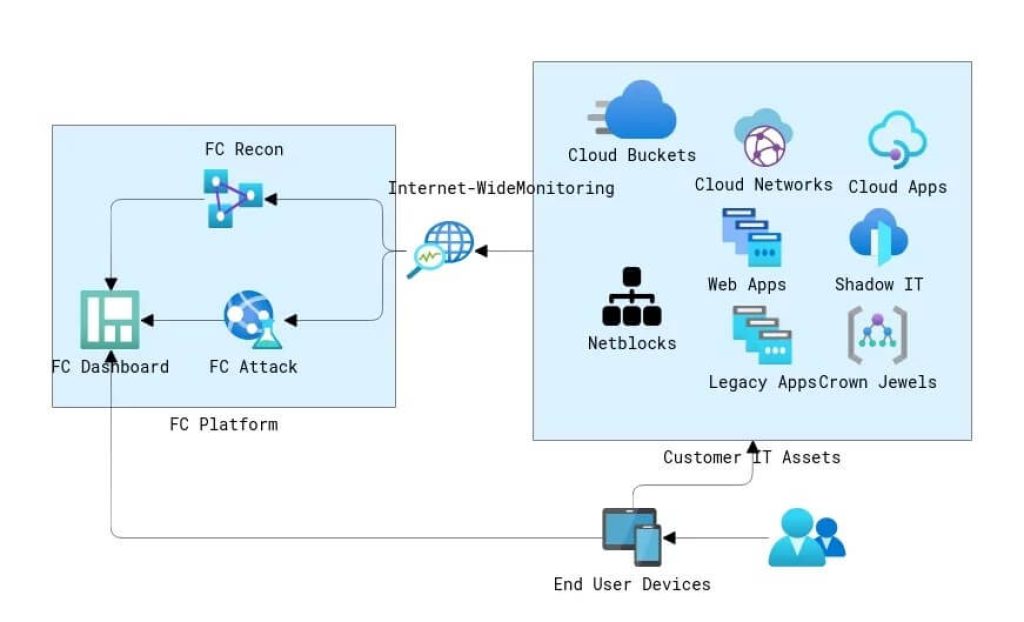
Deployment Architecture:
Software as a Service. No hardware.
No Software. No Agents.
Platform Architecture: Index, Recon, Attack
Indexing Platform
FireCompass runs constantly and records the most unimaginable and surface web involving similar elaborate surveillance methods as danger entertainers.
Automated Recon Platform
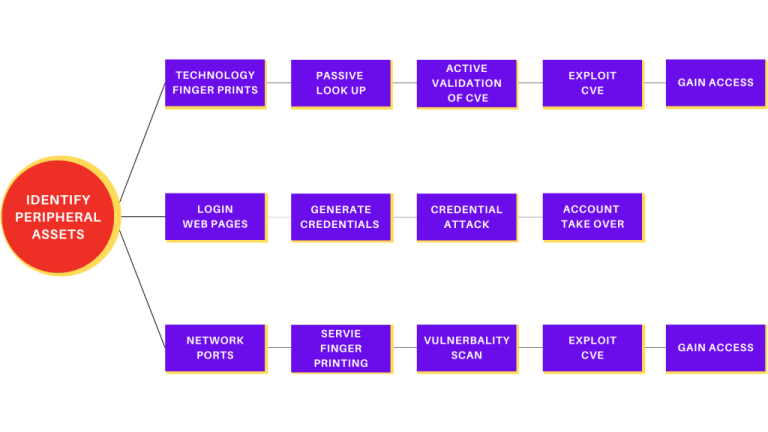
Firecompass utilizes elaborate observation strategies same like the danger entertainers and the stage consequently finds an association's dynamic computerized assault surface
Attack Platform
FireCompass persistent red joining tests your total assault surface to recognize vulnerable sides in your security program. The motor send-offs multi-stage assaults on your assault surface and distinguishes the break and assault ways.
Indexing Platform
FireCompass runs continuously and indexes the deep, dark and surface web using the same elaborate reconnaissance techniques as threat actors.
- OSINT data collection from deep, dark and surface web
- The engine collects data from various threat intel feeds
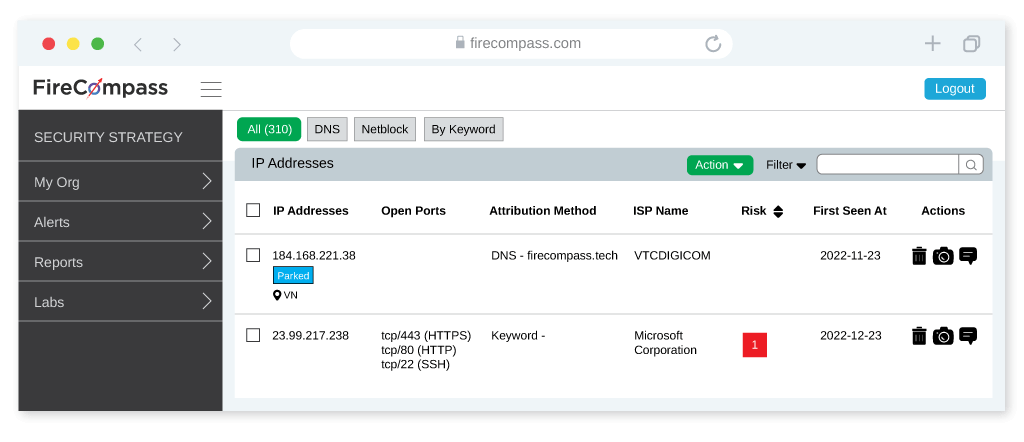
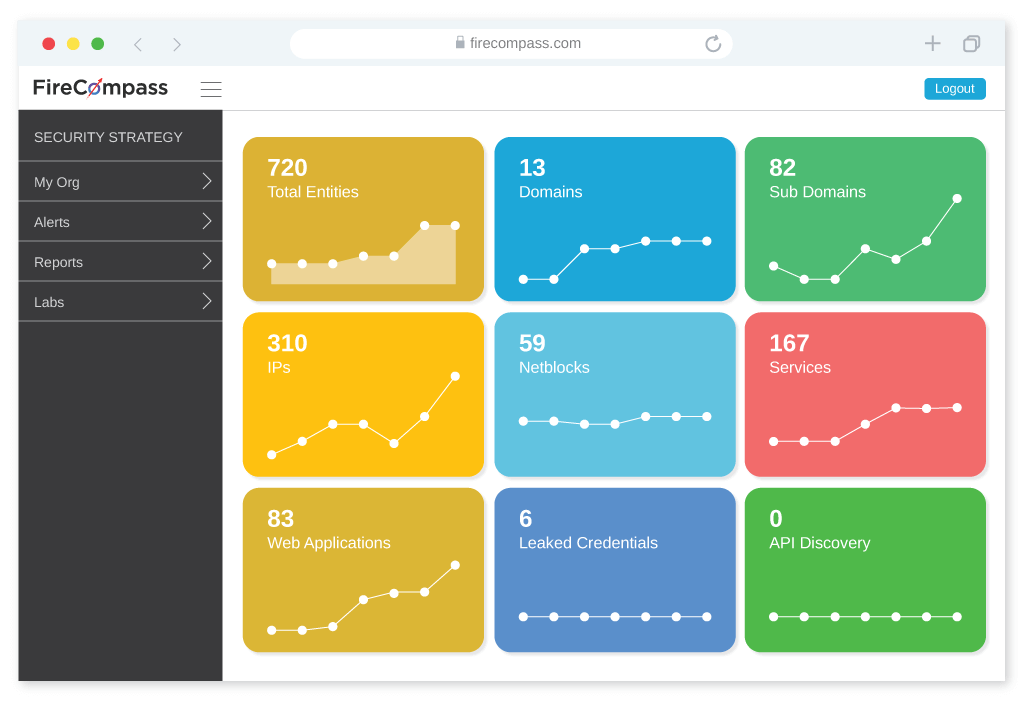
Automated Recon Platform
Firecompass uses elaborate reconnaissance techniques same like the threat actors and the platform automatically discovers an organization’s dynamic digital attack surface, including unknown exposed databases, cloud buckets, code leaks, exposed credentials, risky cloud assets, and open ports & more.
- Continuous Reconnaissance for a Dynamic Perimeter
- Discover your external attack surface, shadow risks and complete asset inventory
- Identify all possible vulnerabilities from known and unknown assets
Attack Platform (with Multi-Stage Attack Capability)
FireCompass Continuous Red Teaming tests your complete attack surface to identify weakest links in your security program and helps you to focus on your business critical assets. The engine launches multi-stage attacks, which includes network attacks, application attacks, and social engineering attacks, on the automatically discovered digital surface to identify breach and attack paths. Attack engine is used to:
- Conduct Port Scanning & Network VA
- Conduct DAST and OWASP Top 10 attacks on web based applications
- Conduct SAST attacks on Mobile applications
- Active Social Engineering attacks
- Objective based attacks & Cloud attacks
Ransomware Attack Surface Testing (RAST)
300% Rise in Ransomware Attacks
- Poor Cybersecurity
- Lack of Awareness
- Geopolitical Tensions
- Vulnerability of Internet-Connected Devices
- Growing Use of Cryptocurrency
- Increased reliance on Work From Home
How FireCompass Helps
Discover & Monitor for Risky Ports
FireCompass assists your association with dodging ransomware that assaults hazardous ports and administrations like FTP, RDP, and HTTP which represent around half of ransomware.
Reduce Your Digital Attack Surface
FireCompass assists associations with diminishing their Advanced Assault Surface by recognizing all pointless open ports/administrations and all potential weaknesses from Known and Obscure resources
Monitor Continuously & Get Real Time Alerts
FireCompass constantly breaks down the web and gives alarms on any progressions or dangers related with your computerized impression.
Discover & Monitor Risky Ports
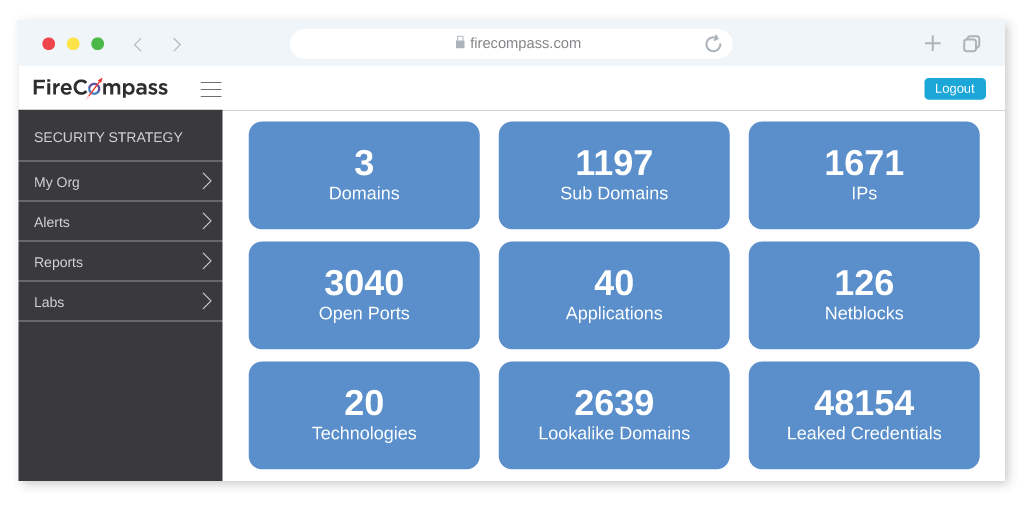
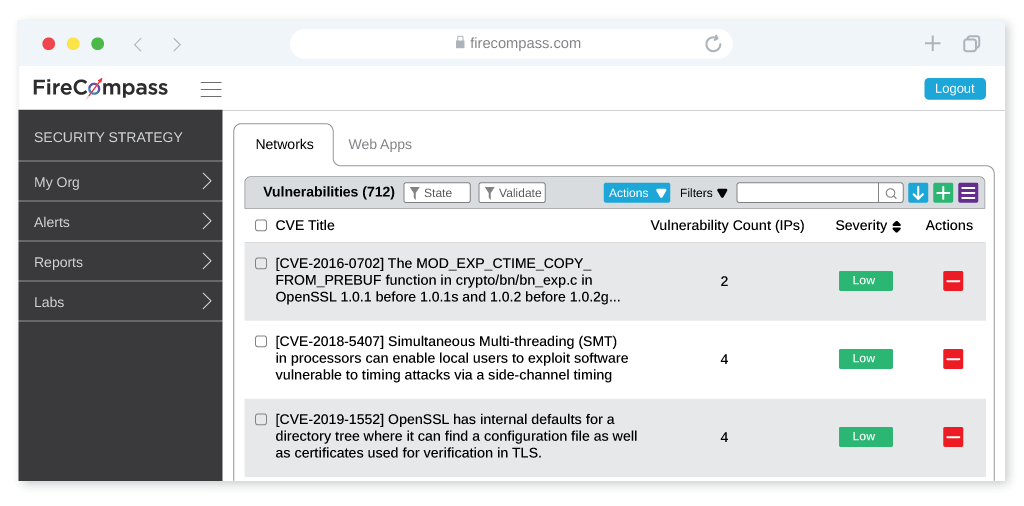
Reduce Your Digital Attack Surface
- Identify malicious infrastructure or domains that might be leveraged for phishing and other ransomware activities.
- Determining the exposed APIs, RDP, FTP, and HTTP systems that may be used to plant ransomware directly.
- Determining the exposed documents & files, IoT infrastructure and anything that may be used to weaponize and target ransomware.
- Automatically attribute assets for streamlined communication with owners to remove attack vectors quickly and efficiently.
Monitor Continuously - Get Real-Time Alerts