Added to wishlistRemoved from wishlist 0
Categories: API protection, Information Security, Security, Threat protection
Threat Detection & Incident Response Done Right.
FEATURES
Access Control
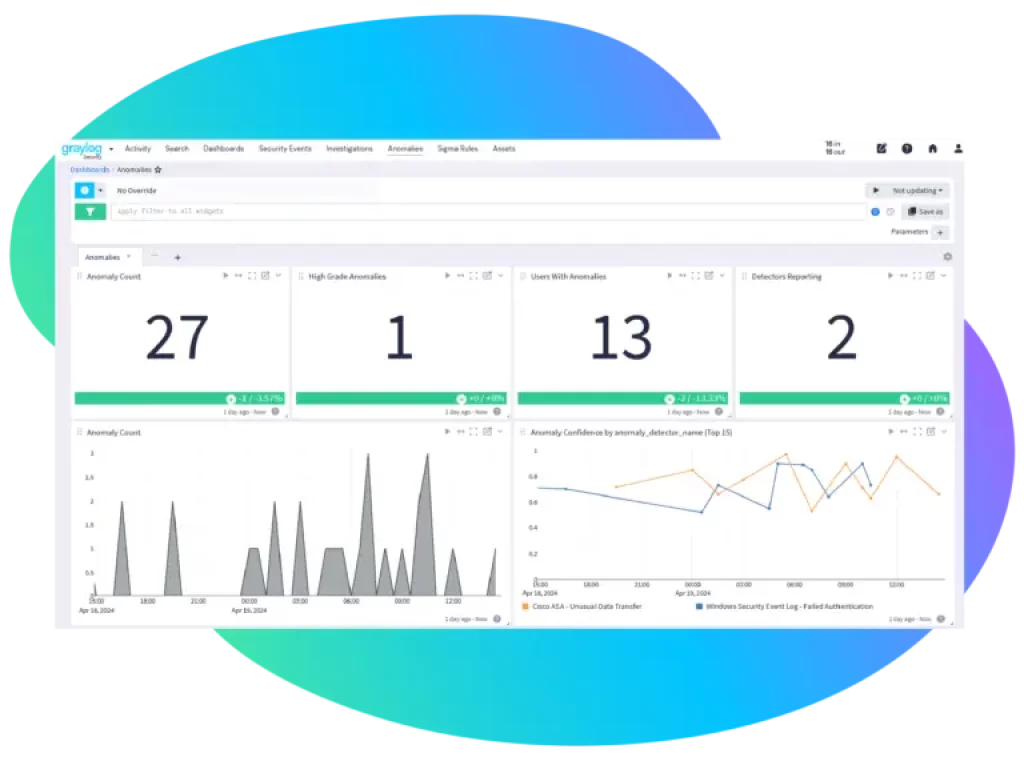
Anomaly Detection
Audit Logs & Archiving
Data Management
Integrations
Events & Alerts
Risk Management
Reports & Dashboards
Investigations
PRODUCTS
Graylog Security
Engaging Your Online protection with Cutting edge SIEM Innovation
Despite rising digital dangers, associations earnestly need proficient danger discovery and episode reaction (TDIR). A strong SIEM arrangement is fundamental, not discretionary, for CISOs handling the double difficulties of complex digital assaults and cost administration.

Identify
Graylog Security works on occurrence examinations. Whether working together across groups all through your association to synergize examination endeavors, recognizing patterns utilizing information saved from earlier examinations, adding significant curios to an examination as you research the episode, or consequently giving remediation steps so investigators can execute a speedy and informed reaction, no matter what their degree of skill. Graylog Security makes it all conceivable.
Prioritize
Graylog Security smoothes out the occurrence examination process, furnishing you with all the vital data to instantly and proficiently answer. With Graylog Security, you can flawlessly team up across groups inside your association, distinguish patterns utilizing information gathered from past examinations, and expeditiously add basic curios to your examination as you research the occurrence.


Respond
Graylog Security works on the occurrence examination process beginning to end so you have all the significant data you want readily available to execute a fast and informed reaction. Whether working together across groups all through your association to synergize examination endeavors, rapidly recognizing patterns utilizing information saved from earlier examinations, or rapidly adding significant curios to an examination as you research the episode, Graylog Security makes it all conceivable.
Evaluate & Evolve
Graylog Security assists you with understanding your digital flexibility by estimating basic security activities KPIs that address how really you moderate gamble so you know where to concentrate improvement drives.

Graylog Enterprise
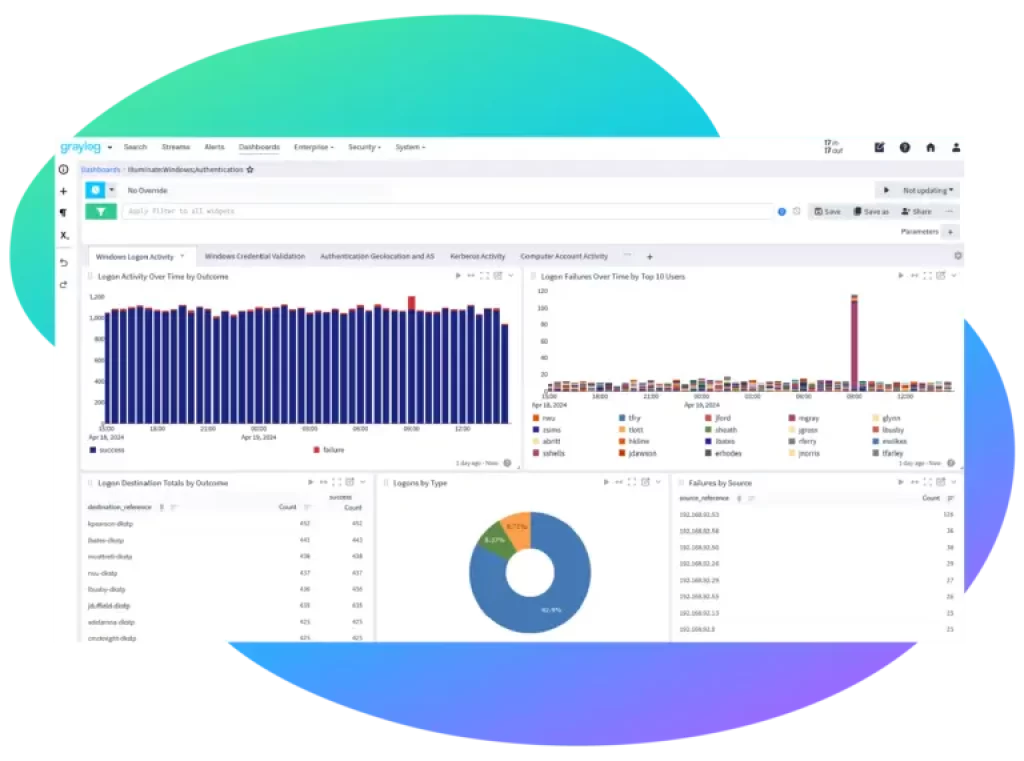

Operational Efficiency
Computerization is the situation! Graylog Venture speeds up fast issue ID and goal, diminishing margin time and improving framework execution. Less free time rises to a more joyful IT group.
Effective Collaboration
Job based admittance controls (RBAC) and Group The board abilities expand Graylog’s worth across your association, permitting groups to team up while utilizing similar informational indexes.


Scalability and Flexibility
Graylog Venture can without much of a stretch adjust to developing information volumes and rambling IT conditions, guaranteeing steady and viable log the executives.
Cost-Effective
All the more value for your money! Graylog Venture mechanizes log the board so you can allot assets to where they truly matter.


Compliance Made Easy
Revealing for administrative norms? Graylog Endeavor’s complete announcing abilities assist with improving on consistence endeavors for administrative norms and review processes.
Graylog Open
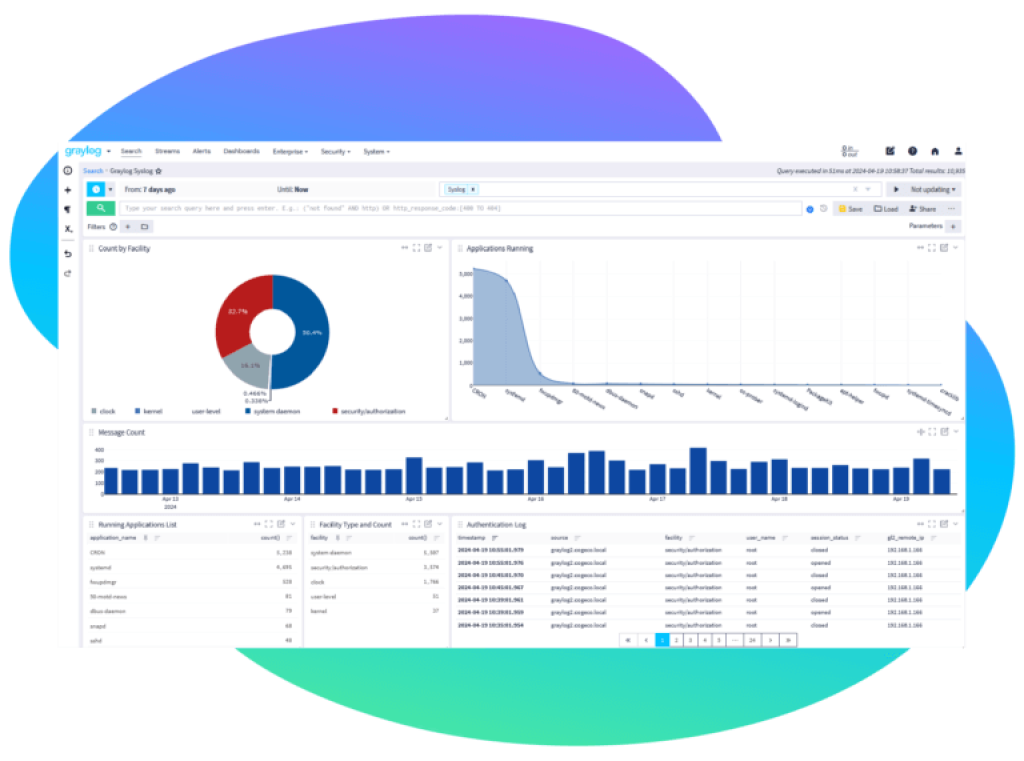
Unlimited Log Ingestion
Can’t conclude what logs to gather while trusting you don’t require information from different logs? Gather everything with Graylog Open.


View Log Data in Real-time
Graylog Open can decrease disappointment and smooth out examinations. Utilizing our log view gadget, you can impart your discoveries and designer them to the right inside crowd.
Search Through Volumes of Log Data
Use Graylog Open to rapidly construct search inquiries and start normal examinations so you can rapidly find and resolve issues, dangers, blackouts, and technical support help demands.


Configure Alerts for What Matters Most
Separate typical regular action from potential issues utilizing Graylog Open’s alarming capacities. Set edges for looking at specific issues and tell the ideal individuals to downplay the agitate.
Graylog API Security
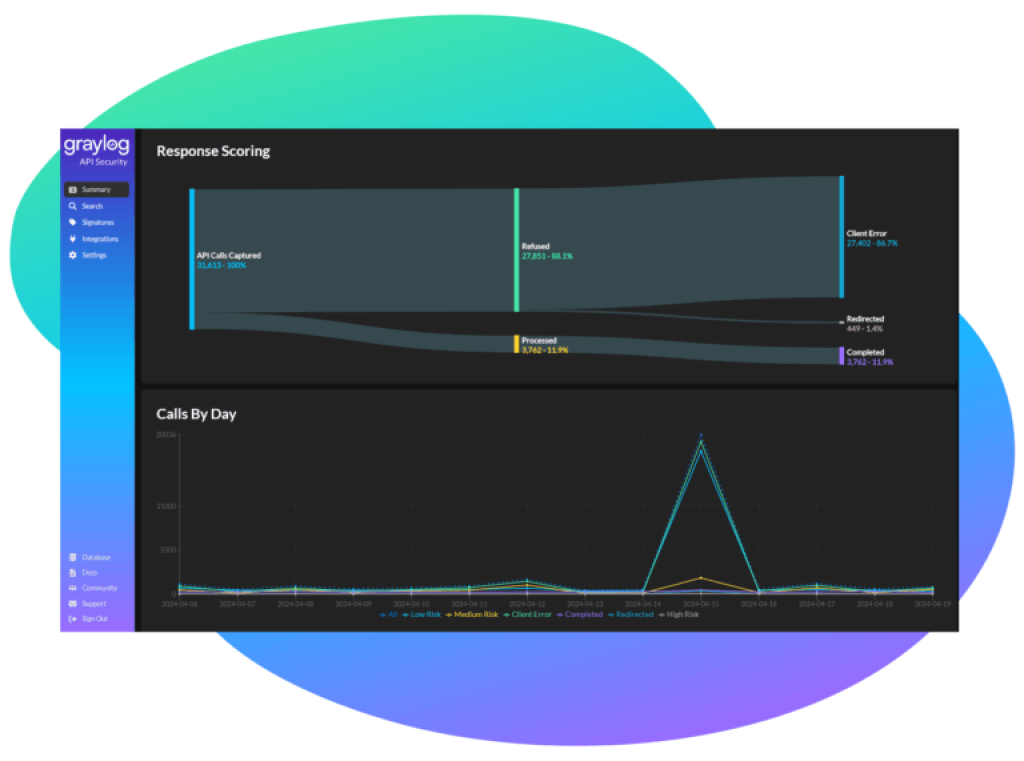
Full API Request & Response Capture: The Unfiltered Truth
Separate typical regular action from potential issues utilizing Graylog Open’s alarming capacities. Set edges for looking at specific issues and tell the ideal individuals to downplay the agitate.

Tuned Risk Assessment Scoring: A Game-changer in Graylog API Security
Graylog Programming interface Security doesn’t simply caution you on possible weaknesses; it engages your Security and DevOps groups with Programmed Chance Evaluation Scoring that is tuned to the kind of Programming interface being observed (REST, GraphQL, JSON) and features high-risk regions that need prompt consideration with accuracy.
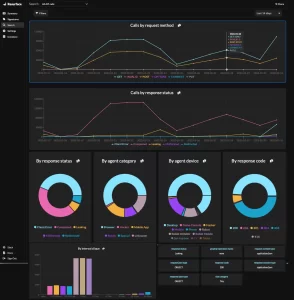
Graylog API Security: Actionable Solutions and Remediation Tips
- A rundown of the fundamental security issue alongside a significant level histogram for guaranteed setting in regards to the movement and power.
- Programmed remediation direction and significant knowledge to help rapidly resolve issues and enhance basic measurements like Interim to Answer (MTTR).
- Adaptable remediation direction choices to help Security and DevOps groups meet objectives inside their coordinated effort apparatus of decision.
- “Find out more” choices for each ready that interface straightforwardly to the Graylog Control center for extra ready setting and situational mindfulness, empowering quick and powerful navigation as groups answer explicit security circumstances.