Start managing application risk
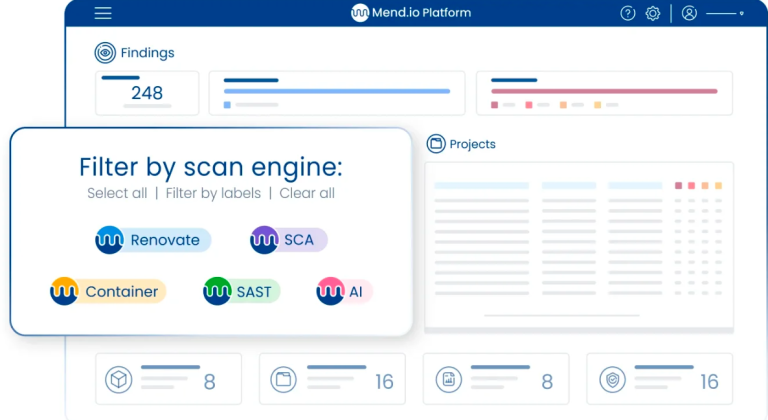
Mend.io gives you every one of the instruments you want to fabricate an experienced, proactive AppSec program that really oversees application risk.
For dev teams
Automated
dependencyupdates
Real-time, on-commit
and differential results
Reachability analysis
in the repo
Remediation suggestions
in the repo
For security teams
Holistic view
of code security
Centralized scan
configuration
Designed for
mass-deployment
Reachability, exploitability,
and CVSS 4.0 prioritization
PRODUCTS
Mend Renovate
Mend Renovate Enterprise lessens risk, further develops code quality, and cuts specialized obligation while further developing chance to deliver via consequently guaranteeing all conditions are stayed up with the latest.
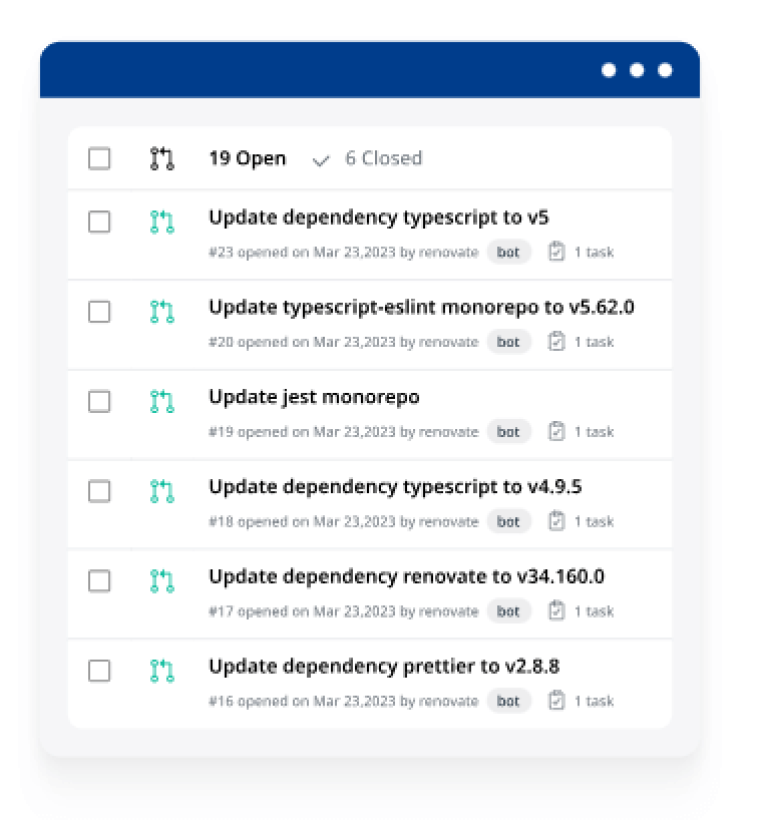
Delivers pull requests straight to the repo
No requirement for your devs to go through hours looking for updates, and pulling them, and combining them.
Mend Renovate Enterprise naturally filters generally your repos to recognize all conditions, and actually takes a look at every single reliance for refreshes. It then raises pull demands for accessible updates and completely sets them up for your devs, with publicly supported test situations with, reception information, discharge notes, and commit narratives.
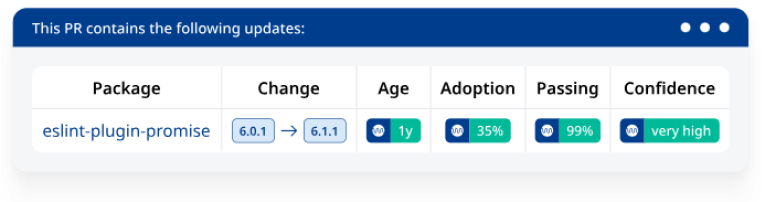
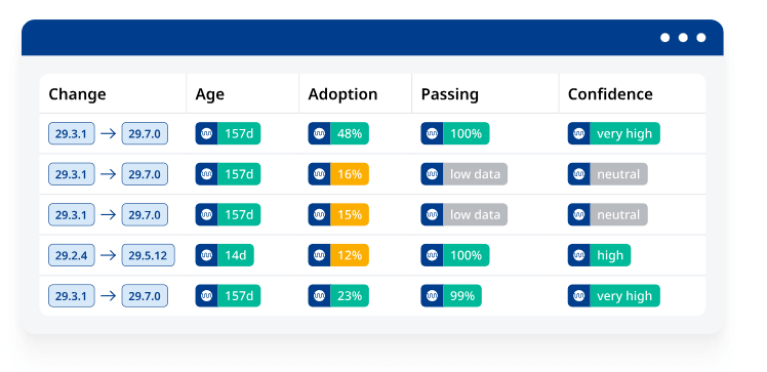
Help devs merge updates with confidence
Certainty that a reliance update won’t create issues in your application is one of a designer’s greatest worries to address.
Mend Renovate Enterprise eliminates this hindrance by giving your devs a determined union certainty rating for each get demand – affirming through publicly supported information that others have updated without issues.
Full scale automation
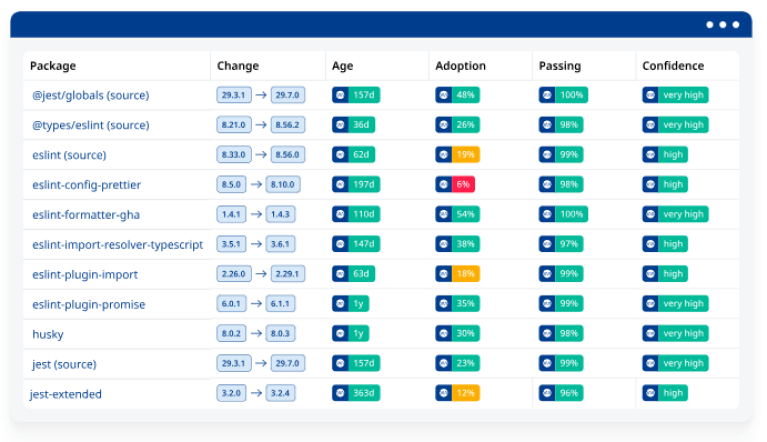
Update private repos
Beside open source conditions, huge advancement groups likewise should be certain they’re utilizing the most cutting-edge adaptation of their interior programming bundles.
Mend Renovate Enterprise does this for you as well, going past open source conditions to help your confidential module and reliance queries, guaranteeing they’re additionally exceptional.
DCAA Timesheet
Mend SCA
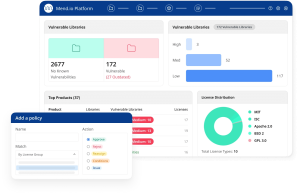
Automate Open Source Security. Reduce Risk.
- Prioritized remediation. Scan for vulnerabilities and malicious packages. Auto-prioritize threats. Remediate in 1-click.
- SBOM management. View all open source libraries and dependencies. Generate instant reports. Export in SPDX, CycloneDX, and other formats.
- Compliance. Auto-identify new licenses in your code. Instantly approve or reject. Create due diligence reports. 2,700+ licenses.
How Mend SCA helps you manage risk across your open source dependencies
Advanced reachability analysis
Risk-based prioritization
License compliance
Stop malicious packages
Software Bill of Materials (SBOM)
Mend Container
Container reachability analysis
Customary weakness recognition is sufficiently not to help your devs decrease risk productively.
Mend Container offers an inventive, agentless reachability investigation, distinguishing which weak strategies are really being utilized at runtime, both on the application layer and the holder layer.
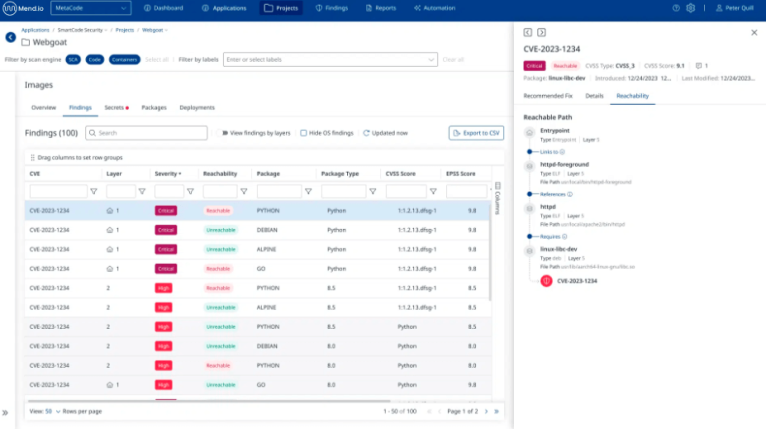
Development to deployment
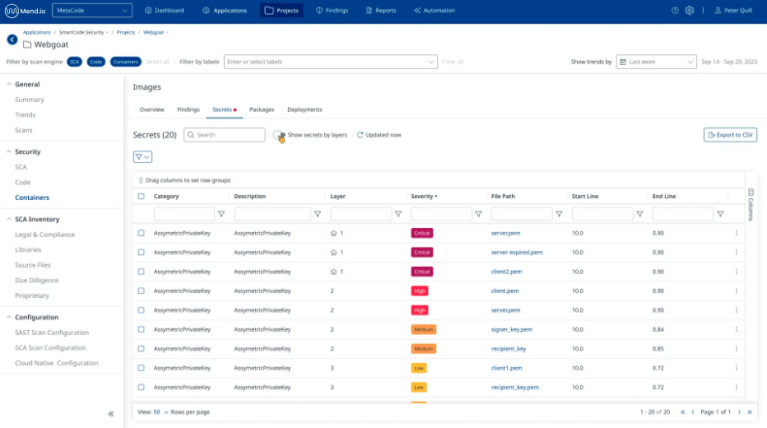
Secrets scanning
Envision a reality where touchy data like passwords, qualifications, keys, and declarations never escape everyone’s notice in your compartment pictures.
Mend Container goes past surface layers, fastidiously filtering through everywhere, including filesystems and code vaults, to uncover stowed away privileged insights that could uncover your frameworks.
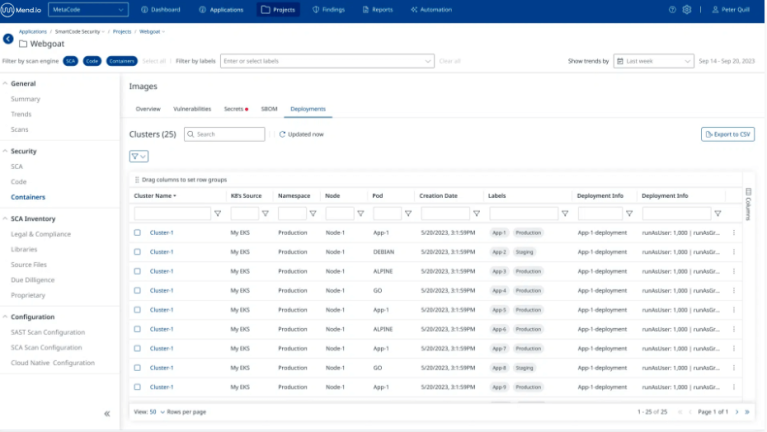
K8s cluster scanning
Smooth out your security interaction via naturally filtering all running compartment pictures inside your Kubernetes bunches.
This extensive view will permit your groups to recognize and mark conveyed holders, guaranteeing you center around getting the adaptations basic to your tasks.
Mend SAST
Mend SAST gives you and your developers all the tools you need to help you stay on top of critical vulnerabilities in your source code.
Delivering near real-time results
Mend SAST conveys results 10x quicker than conventional scanners, giving designers prompt criticism straightforwardly in their vaults.
This implies no pausing, no bottlenecks, simply fast weakness ID and fixing.

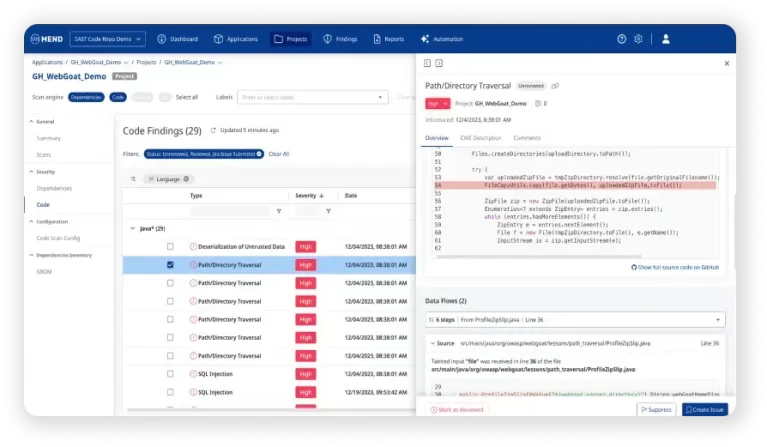
Data flow consolidation
Mend SAST’s creative information stream solidification slices through the clamor, blending related discoveries into one significant knowledge by consolidating numerous weaknesses with a solitary code change.
This implies no additional time squandered pursuing down individual weaknesses. All things considered, you can distinguish the main driver and remediate various issues without a moment’s delay, expanding your effect and saving significant improvement time.
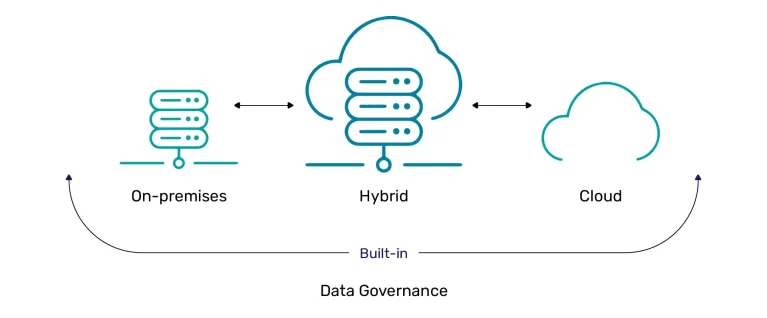
Hybrid cloud solution
Mend SAST offers on-premises filtering, which then, at that point, sends information to be examined in the cloud. Giving you true serenity that your source code never leaves your premises – however with all the speed and adaptability of cloud arrangement.
You likewise have the choice to utilize a committed occurrence – your own cloud server – for examining.
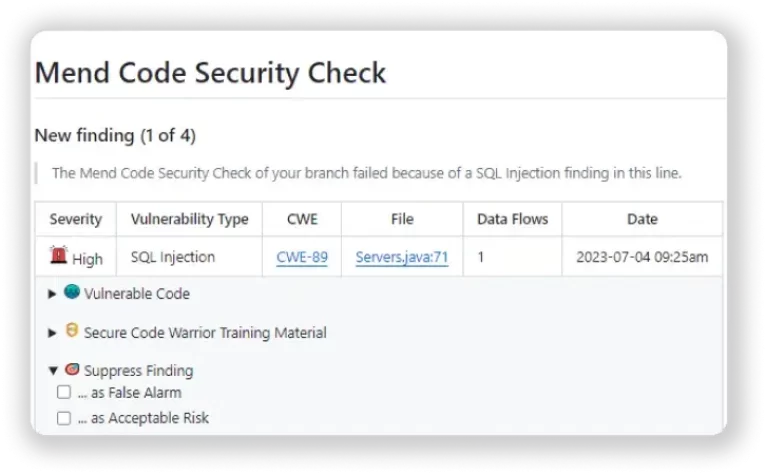
Security and Vulnerability Tested
Mend SAST coordinates consistently into your dev climate, allowing your designers to handle security issues in a split second without exchanging settings.
No really hunting through reports or unraveling language. Repair SAST pinpoints the weakness’ area, shows its information stream, and gives clear, significant stages to fix it. In addition, you get on-the-spot schooling to forestall comparable issues from now on.
Mend AI
AI model compliance
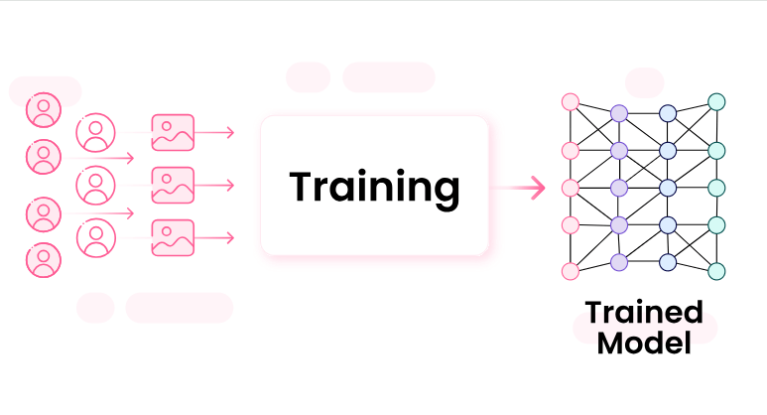
Construct secure computer based intelligence fueled applications with certainty.
Mend AI based intelligence broke down more than 350,000 pre-prepared models to assist your groups with revealing secret security gambles, authorizing concerns, and forming difficulties. Center around development and not security or consistence reviews.
License compatibility and compliance
Artificial intelligence models are frequently prepared on immense datasets which can incorporate prior, open-source codebases with shifting licenses – and now and again even exclusive code. Meaning the code it creates may mix between numerous various components, each with various permitting terms.
Mend AI has listed freely accessible, pre-prepared LLM models so organizations can surface significant data on the models they’re utilizing and stay away from issues with permit similarity and consistence.






